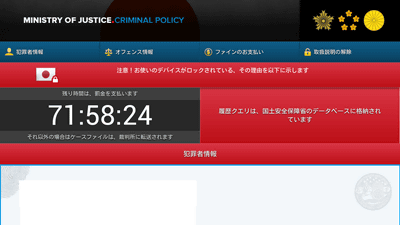
Ransomware which requests about 60,000 yen to hostage by changing PIN code to enter on lock screen is spreading infection

ByErvins Strauhmanis
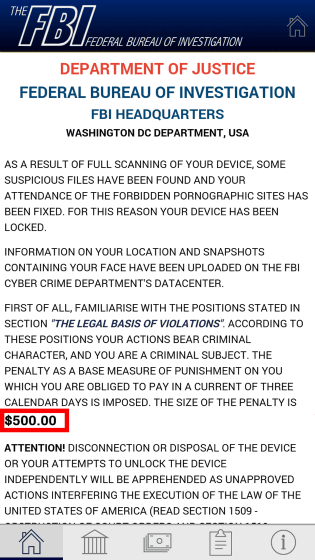
By pretending to be a patch update, malware acquires the administrator's privilege without user's notice, locks the terminal after arbitrarily changing the PIN code, it is $ 500 as "browsing and possessing illegal porn" There is widespread malware that claims demands (about 60,000 yen) is spreading among Android terminals.
Aggressive Android ransomware spreading in the USA
http://www.welivesecurity.com/2015/09/10/aggressive-android-ransomware-spreading-in-the-usa/
The newly reported malware is "Android / Lockerpin.A". After installing on the terminal through an application or movie, it gets the administrator's authority of the device. Android / Lockerpin.A in the early stages, like many malware, rely on a way that users aggressively administer the administrator authority, but in the new version the technique is further elaborate. Android / Lockerpin.A looks like an update of itself as an update of the patch, displays an activate window, and if you think that the user is harmless and allows updates, it will give you administrator privileges without knowing it.
This is a notification of the malware that faked it as an update of the patch actually displayed. If you press "Continue" and proceed, it will grant administrator rights to malware.

After acquiring the administrator's privilege, I will show you to pay 500 dollars (about 60,000 yen) as "I have browsed and possessed illegal pornography".
After the above screen is displayed, the screen is locked, but at this time the malware will change the PIN code to a completely new one, which is different from the one set by the user himself.
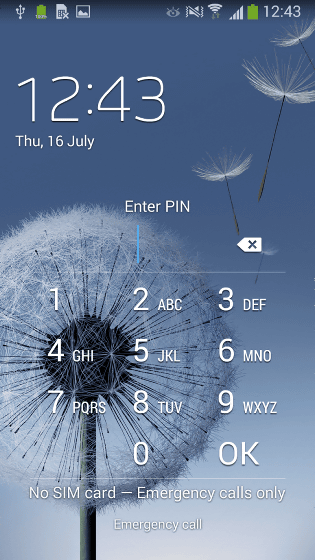
If you are using normal malware, you can uninstall the application,Android Debug BridgeSafe Mode with Android / Lockerpin.A In the case of Android / Lockerpin.A, the PIN code is reset, and the new PIN code is set randomly, so it can not be unlocked by users and attackers It is a feature.
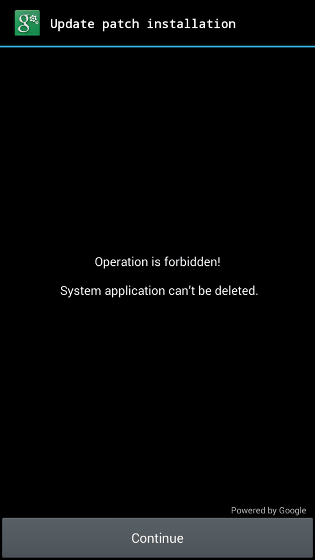
Also, Android / Lockerpin.A not only acquires administrator privileges, it is set to fail with the callback function when trying to withdraw the administrator's privilege of malware. The only remaining unlocked road is to reset the terminal to factory default state, but if this method is adopted, all the data in the terminal will be deleted.
However, Android / Lockerpin.A is a security applicationESET Mobile SecurityIt is impossible to invalidate or delete the function of the security software, and if the security software is functioning, you will notice an abnormality. At the present time, 77% of Android / Lockerpin.A detected by ESET Mobile Security is for the terminal of the United States.

In addition, Android / Lockerpin.A is put in the adult movie itself or an application for watching adult movies, and it will not infect unless you install a third party application that is not currently handled on Google Play Store ... apparently ...
Related Posts:
in Software, Smartphone, Posted by darkhorse_log