Malware is installed and shipped to smartphones such as Huawei, Xiaomi, Oppo, Samsung

It was revealed that Android smartphones such as Samsung and Huawei were shipped with pre-installed malware displaying advertisement without user's permission. There seems to be 5 million terminals shipped with malware mixed in.
RottenSys: Not a Secure Wi-Fi Service At All - Check Point Research
https://research.checkpoint.com/rottensys-not-secure-wi-fi-service/
Check Point Mobile, a security countermeasure company,RottenSysThe malware named "pre-installed on 5 million Android terminals was revealed. The name "RottenSys" was named because malware was being disguised as "System Wi-Fi service" at the outset.
Recently, applications that self-name System Wi-Fi service became prominent in Xiaomi's low-priced smartphone "Redmi" series, as a result of checkpoints by Check Point Mobile engineers, the application is a safe Wi-Fi related service Instead of providing it, I found that I need permission to access sensitive items such as permission of accessibility unrelated to the Wi-Fi service, access to the calendar, permission to download in the background and so on.
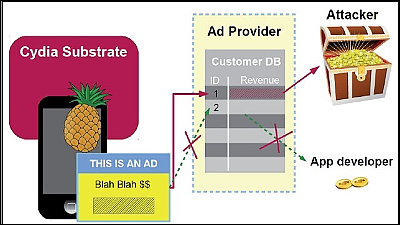
RottenSys is, so as not to be caught out that it is a malicious application, the original is set so as not to activity immediately, instead to be connected to the C & C server, the additional components list that contains the malicious code Send the list and download the component from the C & C server. When all necessary components are downloaded, they will run components in parallel using the Android application's virtualization framework "Small" and display home screens, pop-up windows, full-screen advertisements. In addition, RottenSys connects to China Tencent's advertising platform "Guang Dian Tong" and China Baidu's "Baidu ad exchange" to display advertisements.

From the post that RottenSys displayed the ad on Xiaomi terminal, you can see how the ad is displayed.
Check Point Mobile is also investigating the inflow route of RottenSys, suggesting a relationship with "Tian Pai", a mobile phone sales agency based in China / Hangzhou "Tianzhua" and "Tianjin" I heard that he is finding a clue to do. According to Check Point Mobile, 49.2% of the devices infected with RottenSys found in the survey seems to have been shipped from Tian Pai's sales channel.
The terminals on which RottenSys is installed are as follows. Huawei tops sub-brands including Honor sub-brand, followed by Chinese men's including Xiaomi, Oppo, Vivo, Meizu, LeEco, Coolpad, Gionee and so on, including Samsung terminals.

The trend of infection of RottenSys is as follows and it is increasing at a stretch after mid-2017. According to Check Point Mobile's survey, it was confirmed that 4.96 million 4460 infections were confirmed by March 12, 2018. Since C & C servers are discovered each time the survey progresses, Check Point Mobile points out that there is much possibility of actual damage.
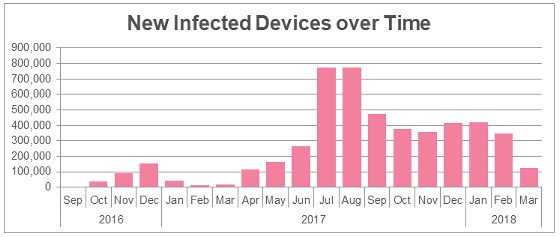
It is estimated that advertisements displayed by RottenSys are only in the past 10 days, the number of impressions exceeds 1.3 million, and advertisement revenue is over $ 115,000 (about 12 million yen).

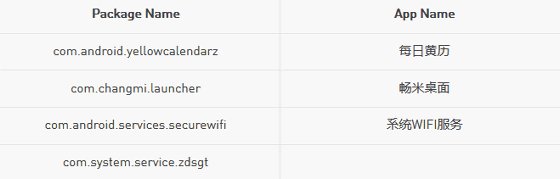
It is very difficult for general users to identify programs related to RottenSys, but it is OK if you use the following four package names and application names as guidelines. Check Point Mobile recommends that you locate the target package name in the Android system's application settings and uninstall it.
Related Posts:
in Hardware, Software, Smartphone, Security, Posted by darkhorse_log