Microsoft releases information on malware 'Adrozek' that hijacks browsers and inserts advertisements in search results

A research team at
Widespread malware campaign seeks to silently inject ads into search results, affects multiple browsers --Microsoft Security
https://www.microsoft.com/security/blog/2020/12/10/widespread-malware-campaign-seeks-to-silently-inject-ads-into-search-results-affects-multiple-browsers/
Microsoft exposes Adrozek, malware that hijacks Chrome, Edge, and Firefox | ZDNet
https://www.zdnet.com/article/microsoft-exposes-adrozek-malware-that-hijacks-chrome-edge-and-firefox/
According to Microsoft's research team, attacks using Adrozek were detected at least in May 2020, and attacks by Adrozek were most active around August 2020, at the same time 30,000 vehicles a day. It is reported that the malware was detected on a super terminal. According to the research team, the number of terminals where Adrozek was detected reached 'hundreds of thousands' in the five months from May to September 2020. It is designed to insert ads on search result pages when Adrozek-infected devices use search engines, targeting major browsers such as Microsoft Edge, Google Chrome, Yandex Browser, and Mozilla Firefox. It seems that
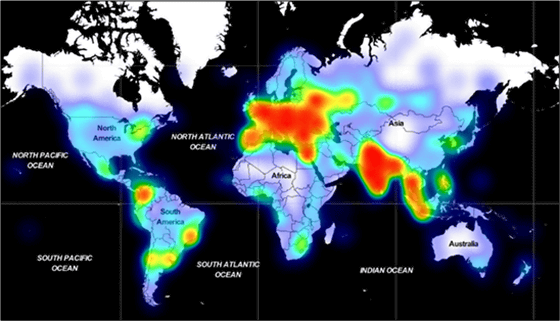
The distribution map of the terminals where Adrozek was detected is as follows. The attack range is mainly from Europe and South Asia to Southeast Asia.
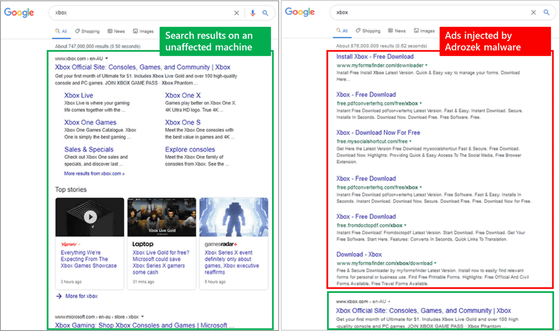
When infected with Adrozek, malicious ads that should not be displayed will be displayed on top of the correct ads that are displayed when using a search engine in a browser. Clicking on this fraudulent ad will lead to an
The left side of the image below is the search result page where the advertisement was displayed normally, and the right side is the search result page where the malicious advertisement displayed by the browser of the PC infected with Adrozek is displayed. The malicious advertisement surrounded by the red frame is displayed above the normal advertisement in the green frame, which leads to the affiliate page.
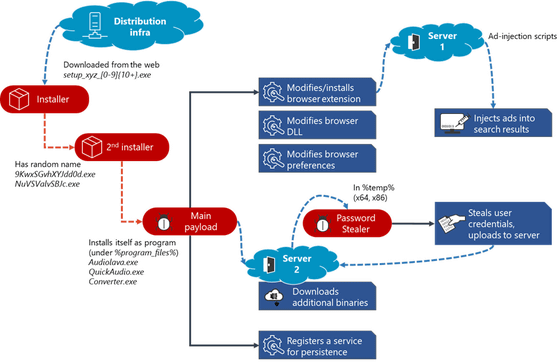
According to the research team, Adrozek is distributed by
Once Adrozek is installed on your PC, Adrozek uses a registry key to get the persistence of restarting your PC. After that, Adrozek searches for browsers such as Microsoft Edge and Google Chrome installed in the local area of the PC. If the browser is found, Adrozek will rewrite the browser's AppData folder to force the extension to be installed.
After that, Adrozek changed a part of the browser's dynamic link library (DLL) file and changed the browser settings to disable the security function so that the security function installed in the browser would not detect malware. To be.
This allows the browser to display malicious ads on the search results page. The figure below summarizes the infection route of Adrozek.
'Adrozek's operations are very sophisticated, especially its distribution infrastructure,' said a Microsoft research team. Tracking 159 domains where Adrozek installs on its own, it's clear that each domain hosts an average of 17,300 URLs, and each URL hosts more than 15,300 installers. It is said that it became.
The research team said, 'Many domains host tens of thousands of URLs, some of which host more than 100,000 unique URLs, some of which have about 250,000 URLs. There was also a hosting domain. The large infrastructure for distributing Adrozek indicates that the attacker is willing to keep this cyber attack running for a long time. I point out. Also, according to the research team, some domains have been in operation for only one day, while others have been in operation for 120 days.
As a whole, we are applying polymorphism to the operation of the distribution infrastructure, so it is expected that the number of devices infected with Adrozek will increase further in the next few months.
Cyberattacks that exploit affiliate programs aren't new, but Microsoft's research team said, 'This kind of cyberattack is becoming more and more sophisticated, as one malware is designed to run across multiple browsers. It shows that it is. '
Related Posts: