Reported that a group of hackers connected to the Chinese government is launching a large-scale hacking attack targeting Japanese companies

'Large-scale hacking attacks targeting Japanese and related companies around the world are being carried out by a group of hackers who appear to be backed by the Chinese government,' a security researcher at
Japan-Linked Organizations Targeted in Long-Running and Sophisticated Attack Campaign | Symantec Blogs
https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/cicada-apt10-japan-espionage
APT Exploits Microsoft Zerologon Bug: Targets Japanese Companies | Threatpost
https://threatpost.com/apt-exploits-zerologon-targets-japanese-companies/161383/
Massive, China-state-funded hack hits companies around the world, report says | Ars Technica
https://arstechnica.com/information-technology/2020/11/massive-china-state-funded-hack-hits-companies-around-the-word-report-says/
The large-scale attacks discovered by the researchers are targeting multiple Japanese companies and their subsidiaries in 17 countries and regions around the world. Researchers report that the targets of the attack are diverse, including automobile companies, pharmaceutical companies, general trading companies, and
Simmantech's Cloud Analytics technology, which utilizes artificial intelligence, is involved in the discovery of large-scale attacks targeting Japanese companies. After Cloud Analytics, which can analyze the huge amount of data held by NortonLifeLock (Simantec's consumer business), flagged a suspicious cyber attack, the research team conducted a detailed analysis. It is said that an overall picture of a large-scale attack that spans countries around the world has emerged.
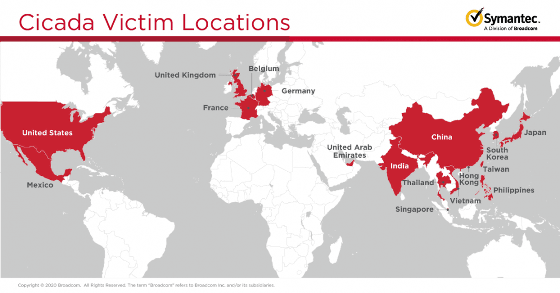
The series of attacks continued at least from mid-October 2019 to October 2020, with considerable time and resources devoted to it. This is a map showing the countries and regions where the companies that were actually damaged are located. You can see that companies in Asia, Europe, North America, etc. are targeted. The companies that were damaged were mainly famous and large-scale Japanese companies and their affiliated companies, and the companies that were attacked in China were also subsidiaries of Japanese companies. Researchers attribute the series of attacks to the hacker group APT10 (Cicada), which is believed to be backed by the Chinese government.
Hacking with APT10 has been a hot topic for some time, targeting companies and institutions around the world.
It turns out that the cracker group 'APT10' has invaded the network of a large company, and the perpetrator may be the minion of a Chinese intelligence agency --GIGAZINE

by Nicolas Raymond
It is presumed that many hackers who carry out large-scale hacking with a wide range of attacks, such as this one, are generally supported by the government. APT10 has a precedent of hacking Japanese companies before, and it is similar to the past movement of APT10 in that it targets MSPs that operate, monitor, and maintain customers' computers and networks. It is said that it is.
In addition, a hacker's widespread attack technique called ' DLL sideloading ' replaces a DLL file, which is a Windows program file, with a malicious file to inject malware while avoiding the detection of security software. Researchers have pointed out that the shellcode and obfuscation techniques used in this attack method also overlap with those used by APT10 in the past.
From the above points, researchers believe that the series of attacks is due to APT10, and argue that many organizations related to Japan can be the target of sophisticated and resource-rich cyber attacks. So far, the automotive industry has been the main target, but it needs to be aware that organizations in all other areas are at potential risk.
In addition, some of the attacks confirmed by Symantec used the vulnerability Zerologon , which Microsoft had just patched in August 2020. The use of the latest vulnerabilities also suggests that attackers are constantly evolving their hacking tools and tactics.

Related Posts:
in Security, Posted by log1h_ik