Backdoor 'Daxin' closely connected to China turned out to be able to hijack 'devices not directly connected to the Internet'

Malware that enables the ThreatHunter team of cybersecurity company
Broadcom Software Discloses APT Actors Deploying Daxin Malware in Global Espionage Campaign | CISA
https://www.cisa.gov/uscert/ncas/current-activity/2022/02/28/broadcom-software-discloses-apt-actors-deploying-daxin-malware
Daxin: Stealthy Backdoor Designed for Attacks Against Hardened Networks | Symantec Blogs
https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/daxin-backdoor-espionage
Chinese cyberspies target govts with their'most advanced' backdoor
https://www.bleepingcomputer.com/news/security/chinese-cyberspies-target-govts-with-their-most-advanced-backdoor/
New Chinese hacking tool found, spurring US warning to allies | Reuters
https://www.reuters.com/technology/new-chinese-hacking-tool-found-spurring-us-warning-allies-2022-02-28/
According to CISA, 'Daxin' provides complex and difficult-to-detect command and control features that allow remote access to devices that should be in a secure state that is not directly connected to the Internet. It is an advanced rootkit backdoor that I had. By using Daxin, an attacker can sneak deep into the target network and steal data. According to the ThreatHunter team, Daxin is 'one of the most advanced backdoors' deployed by Chinese attackers.
One of the characteristics of Daxin is that it is 'malware targeting Windows kernel drivers', which is not very typical in the malware world. Daxin has a high degree of stealth, which derives from its advanced communication capabilities that combine data exchange with normal Internet traffic.

Daxin is not only malware that provides remote access to compromised computer systems by attackers, it can also steal data from infected devices, execute commands remotely, and install other malware. am. Malware like Daxin is typically used to steal information from protected networks or further compromise devices, so it is encrypted for data transfer to prevent it from being detected by network traffic monitoring tools. Malware or obfuscation. On the other hand, in the case of Daxin, it is designed to escape network monitoring by monitoring network traffic on the terminal, detecting a specific pattern and imitating it. Then, after detecting a specific pattern of network traffic, the attacker can communicate with the
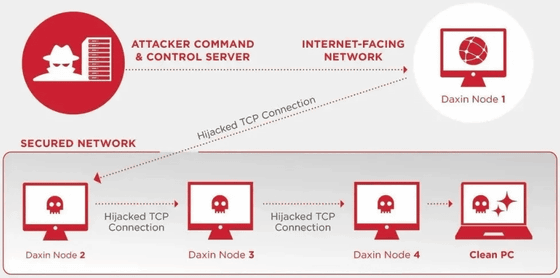
The ThreatHunter team said, 'Daxin hijacks TCP connections, which increases the stealth of communications and allows them to establish connections on the network using strict firewalls. This allows the Security Operations Center ( SOC) It will be difficult for analysts to detect anomalies on the network. '
In addition, Daxin increases the number of infected devices by hijacking TCP connections, so if only the terminal that is the source of infection is connected to the Internet, it will spread the infection even if other terminals are not connected to the Internet. Is possible. Elsewhere, Daxin's built-in functionality can be extended by placing additional components on infected terminals. This additional component associates a 32-bit service identifier with a particular handle, allowing an attacker to communicate with this component by sending a particular message remotely. As a result, complex communication paths can be established in Daxin-infected terminal networks, which makes it difficult to detect malicious traffic and 'minimizes the possibility of an attacker being detected. That's why.
The ThreatHunter team has discovered that Daxin-based attackers are associated with a Chinese government-backed hacking group, Slug (also known as Owlproxy). In addition, Daxin was first detected in 2013, and it seems that it had the same function as the present at that time, but it seems that there was no evidence that it was used for cyber attacks for a while. The latest cyberattack involving Daxin was observed in November 2021 and was targeted at companies related to the telecommunications, transportation, and manufacturing industries.
Related Posts: