Microsoft discovers malware 'MCCrash' that launches DDoS attacks targeting Minecraft servers

In
MCCrash: Cross-platform DDoS botnet targets private Minecraft servers - Microsoft Security Blog
https://www.microsoft.com/en-us/security/blog/2022/12/15/mccrash-cross-platform-ddos-botnet-targets-private-minecraft-servers/
Microsoft discovers Windows/Linux botnet used in DDoS attacks | Ars Technica
https://arstechnica.com/information-technology/2022/12/microsoft-discovers-windows-linux-botnet-used-in-ddos-attacks/
Microsoft warns of new Minecraft DDoS malware infecting Windows, Linux
https://www.bleepingcomputer.com/news/security/microsoft-warns-of-new-minecraft-ddos-malware-infecting-windows-linux/
This malware, named 'MCCrash' by Microsoft security researchers, infects Windows and Linux of various distributions, builds a botnet and performs DDoS.
The infection route is 'KMSAuto Lite', a cracking tool aimed at illegally obtaining licenses for Windows products. If you install this software to avoid Microsoft Office authentication, your device will be infected with MCCrash.
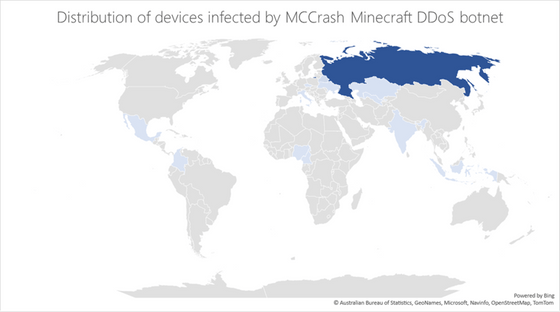
Below is a map based on the IP addresses of devices infected with MCCrash via cracking tools. You can see that the infected people are concentrated in Russia.
After invading a Windows machine, MCCrash builds a botnet by targeting other Windows machines, Linux machines, and IoT devices, which often have less security measures than PCs, on the Internet. It then sends a string of characters as a username to the Minecraft server, which is meant to drain the machine's resources, causing the server to crash. This is how a DDoS attack using MCCrash works.
According to Microsoft, MCCrash is
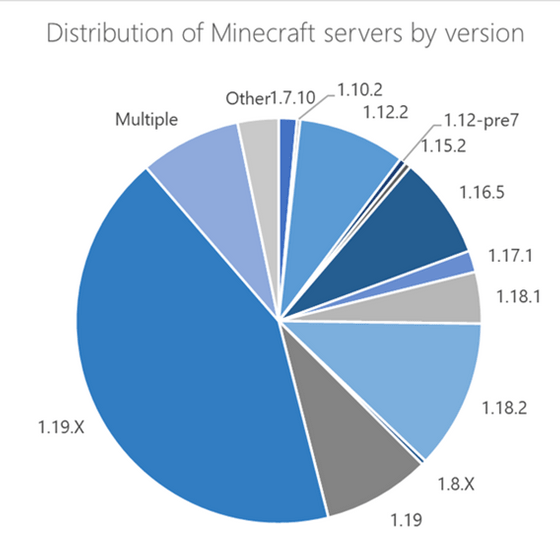
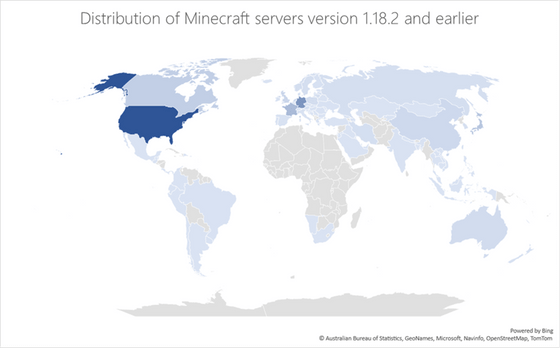
The distribution map of servers before version 1.18.2 is as follows. The main targets are Minecraft servers in the United States, Germany, and France, but it has been shown that the damage will extend to various parts of the world, including Japan, Asia, the Middle East, and South America.
Microsoft commented on MCCrash, ``The unique ability to use IoT devices, which are often unmonitored, greatly increases their impact and makes them less likely to be detected.'' It also points out that it was created to sell DDoS services on darknets and criminal forums, as it has features designed to target private servers of Minecraft for Java.
Related Posts: