FBI destroys Chinese botnet 'Raptor Train' that infected 260,000 routers and network cameras with malware

Office of Public Affairs | Court-Authorized Operation Disrupts Worldwide Botnet Used by People's Republic of China State-Sponsored Hackers | United States Department of Justice
https://www.justice.gov/opa/pr/court-authorized-operation-disrupts-worldwide-botnet-used-peoples-republic-china-state
Derailing the Raptor Train - Lumen
https://blog.lumen.com/derailing-the-raptor-train/
Chinese botnet infects 260,000 SOHO routers, IP cameras with malware
https://www.bleepingcomputer.com/news/security/flax-typhoon-hackers-infect-260-000-routers-ip-cameras-with-botnet-malware/
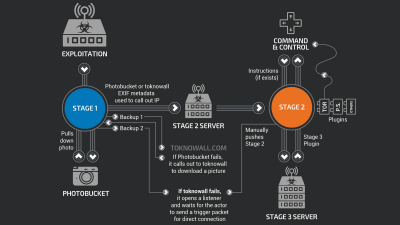
'Raptor Train' is a botnet used primarily to target the U.S. and Taiwanese military, government, higher education institutions, telecommunications facilities, defense industrial bases, and IT companies, and has been confirmed to have been in operation since around May 2020. Researchers from Black Lotus Labs, Lumen's threat research and operations division, discovered the existence of Raptor Train while investigating a compromised router.
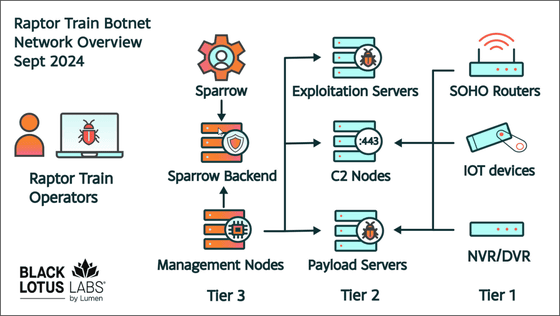
Raptor Train is a bot network based on malware-infected consumer devices, including servers, routers, modems, network video recorders (NVRs), digital video recorders (DVRs), network cameras (IP cameras), and NAS .
The main payload of Raptor Train is the Mirai variant 'Nosedive', a malware for distributed denial of service (DDoS) attacks. However, it has not been confirmed at the time of writing that Raptor Train is deploying DDoS attacks. Raptor Train is built in three layers, each of which is responsible for 'submitting tasks', 'managing exploit or payload servers', 'operating the command and control (C2) system', etc.
The number of actively compromised devices in Raptor Train has fluctuated over time, but more than 200,000 devices have been leveraged in the Raptor Train bot network since its inception in May 2020. Raptor Train activity peaked in June 2023, when more than 60,000 devices appeared to be operational.
According to research from Black Lotus Labs, the number of devices building Raptor Train has fluctuated by several thousand units since August 2024.
According to the FBI, more than 260,000 devices have been infected with Raptor Train to date, broken down as follows:
| Country/Region | Number of infected devices | ratio |
|---|---|---|
| America | 126,000 units | 47.9% |
| Vietnam | 21,100 units | 8.0% |
| Germany | 18,900 units | 7.2% |
| Romania | 9,600 units | 3.7% |
| Hong Kong | 9,400 units | 3.6% |
| Canada | 9,200 units | 3.5% |
| South Africa | 9,000 units | 3.4% |
| England | 8,500 units | 3.2% |
| India | 5,800 units | 2.2% |
| France | 5,600 units | 2.1% |
| Bangladesh | 4,100 units | 1.6% |
| Italy | 4,000 units | 1.5% |
| Lithuania | 3,300 units | 1.3% |
| Albania | 2,800 units | 1.1% |
| Netherlands | 2,700 units | 1.0% |
| China | 2,600 units | 1.0% |
| Australia | 2,400 units | 0.9% |
| Orlando | 2100 units | 0.8% |
| Spain | 2000 units | 0.8% |
FBI Director Christopher Wray, who attended the Aspen Cyber Summit held in New York, USA on September 18, 2024 local time, reported that Raptor Train was operated by Flax Typhoon , a threat actor supported by the Chinese government.
Wray announced that the FBI had seized control of the Raptor Train through a court-authorized operation, during which Flax Typhoon also attempted to migrate infected devices to new servers and launch DDoS attacks against the FBI.
In June 2024, the FBI obtained a MySQL database from the Raptor Train botnet (Tier 1) and the upstream management server of Tier 3, the third layer from the C2 server (Tier 2), which contained records of 1.2 million compromised devices, of which 385,000 were individual systems in the United States. Because Raptor Train used an IP address of China Unicom in Beijing, the FBI identified the cyber attack using Raptor Train as 'a cyber attack carried out by Chinese state-sponsored hackers working for the Chinese company Integrity Technology Group in Beijing, known as Flax Typhoon.'
The FBI has published a list of devices and manufacturers confirmed to be affected by Raptor Train, which is as follows:
◆Modem/Router
・ActionTec PK5000
・ASUS RT series/GT series/ZenWifi
・TP-LINK
・DrayTek Vigor
・Tenda Wireless
・Ruijie
・Zyxel USG
・Ruckus Wireless
・VNPT iGate
・Mikrotik
・TOTOLINK
◆Network Camera
・D-LINK DCS series
・Hikvision
・Mobotix
・NUUO
・AXIS
Panasonic
・NVR/DVR
・Shenzhen TVT NVRs/DVRs
◆NAS
・QNAP (TS series)
・Fujitsu
・Synology
・Zyxel

Black Lotus Labs researchers, like the FBI, have assessed that Raptor Train's operators are likely state-sponsored Chinese hackers, specifically Flax Typhoon. Black Lotus Labs made this assessment not only because Raptor Train's attacks targeted targets that aligned with Chinese interests, but also because the languages used in the codebase and infrastructure, as well as other tactics, techniques, and procedures employed, are similar to those of China. Black Lotus Labs researchers also pointed out that the connections from Tier 3 to Tier 2 of Raptor Train were consistent with Chinese workday hours.
Black Lotus Labs also pointed out that Raptor Train 'exploited more than 20 different device types with zero-day and N-day vulnerabilities to build a bot network.' Furthermore, Black Lotus Labs points out that Raptor Train distinguishes between payload servers in the Tier 1 layer and payload servers in the Tier 2 layer, saying, 'The former deliver more general payloads, while the latter perform targeted attacks against specific device types.' The research team noted that the reason for the distinction between the payload servers 'may be part of an effort to better conceal the zero-day vulnerabilities used in the attacks.'
Raptor Train has been used in scanning operations targeting the U.S. government, the U.S. military, IT providers, and the defense industrial base, but it has also been used in cyber attacks targeting government agencies in Kazakhstan, suggesting that the group may be operating globally and not just targeting the U.S.
In addition, the Black Lotus Labs research team recommends that general users reboot their routers regularly and update their firmware to the latest version.
Related Posts:
in Security, Posted by logu_ii