A Trojan horse 'ZuoRAT' aimed at small offices and personal routers is reported, is it the Chinese government in the background of the attacker?

Researchers at Black Lotus Labs , the threat intelligence division of CDN company Lumen Technologies, are targeting new remotes targeting small office or personal (SOHO) routers, aiming for a surge in remote workers during the outbreak of the new coronavirus. It is reported that ' ZuoRAT ', which is an access type Trojan horse (RAT), has appeared.
ZuoRAT Hijacks SOHO Routers to Silently Stalk Networks --Lumen
https://blog.lumen.com/zuorat-hijacks-soho-routers-to-silently-stalk-networks/
ZuoRAT malware hijacks SOHO Routers to spy in the vitims Security Affairs
https://securityaffairs.co/wordpress/132709/hacking/zuorat-soho-campaign.html
ZuoRAT is designed to target ASUS, Cisco, DrayTek, and NETGEAR routers, allowing malicious attackers to steal sensitive information exchanged over the network. ZuoRAT consists of at least four malwares, three of which were newly developed.
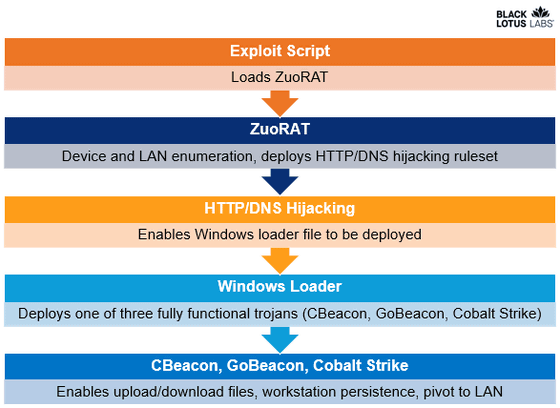
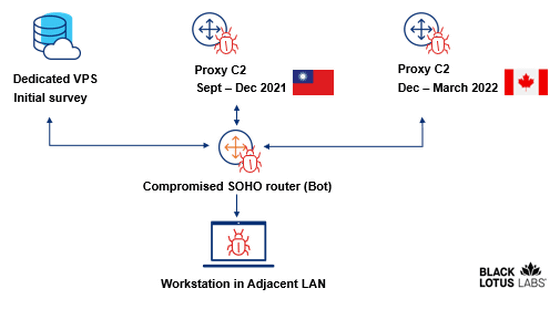
ZuoRAT malware first detects vulnerabilities in unpatched routers, and ZuoRAT creates a backdoor by exploiting the detected vulnerabilities. And not only the information of the targeted router and LAN is sent to the C2 server , but also the router itself is operated as a proxy C2 server after erasing its own traces. According to researchers, the router hijacking part of ZuoRAT is a significantly modified version of Mirai .
In addition, ZuoRAT replaces IP addresses corresponding to domains such as Google and Facebook with malicious IP addresses under the control of the attacker. ZuoRAT also hijacks the HTTP protocol, tampering with the communication and redirecting the user to another IP address 302 .
According to researchers, the commands and instruction structures used in this campaign are deliberately complicated to hide what's happening. One structure is used to control the infected router and the other structure is reserved in case the connected device becomes infected.
The ZuoRAT threat removes the first exploit consisting of files stored in a temporary directory once the router is restarted. However, in order to recover completely, it is necessary to initialize the infected device to the factory default state.

According to researchers, some ZuoRAT samples have confirmed connections to Chinese IP addresses and may be targeting Hong Kong. In addition, when analyzing multiple samples, the researchers found that the program database paths were all common, some of which contained Chinese characters, and also included words for Chinese place names. Pointed out that ZuoRAT was developed by a Chinese cyber criminal. Its complex and elaborate structure also suggested that the Chinese government may be involved.
Researchers said, 'Organizations need to carefully monitor SOHO devices to see if the activity shown in this study is occurring. ZuoRAT is clever in its operation, so the scale of damage has not been discovered. In order to mitigate the ZuoRAT threat, make sure to update the device firmware including the router and make sure that these devices have the latest firmware. I need to. '
Related Posts: