CCleaner's malware contamination problem turned out to be a targeted attack targeting large companies such as Intel, Sony and Microsoft

System cleaner software "CCleaner"Talos Security Department under the umbrella of Cisco announced that" malware was aimed at targeted attacks targeting specific large companies "due to the problem of malware being downloaded and delivered to the full version of the official version . People who installed 32-bit CCleaner v5.33.6162 or CCleaner Cloud v1.07.3191 are recommended to reinstall HDD / SSD format / OS.
Cisco's Talos Intelligence Group Blog: CCleaner Command and Control Causes Concern
http://blog.talosintelligence.com/2017/09/ccleaner-c2-concern.html
The CCleaner malware contamination riot can be confirmed in the following article.
CCleaner's official file has been tampered with and downloaded with malware included - GIGAZINE

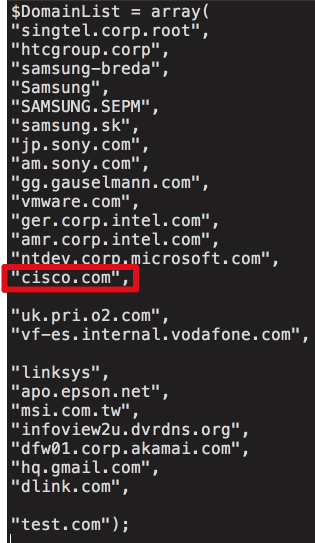
Talos analyzed the data remaining in the C2 server controlling malware, it turned out that the server was further distributed fraudulently. Domain names such as Microsoft · Gmail · VMware · Akamai · Sony · Samsung are listed in the distribution list, and Talos' Cisco was also targeted.
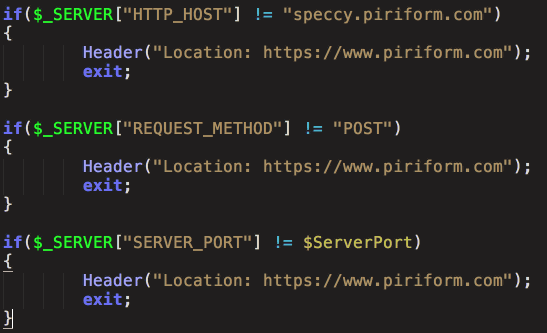
According to the analysis of the PHP file, it was said that a mechanism for checking whether to continue server operation or redirect to Priform's website was implemented.
The software installed on the machine and running processes are retrieved from the list and stored in the MySQL database.
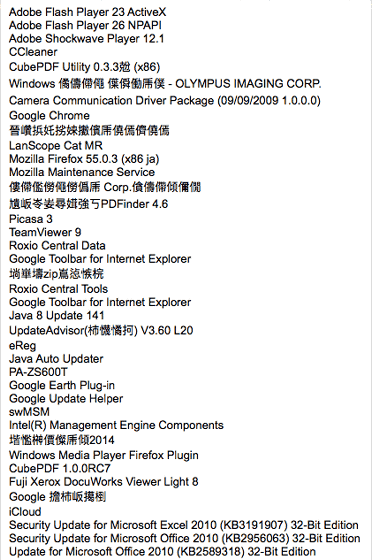
Process list

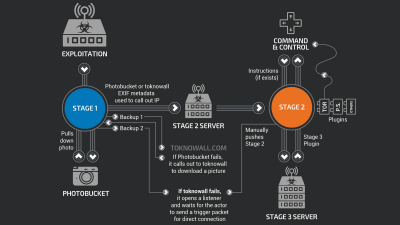
The PHP script was selected as a target to attack by combining it with information such as IP address, MAC address, host name, domain name, etc., and the C2 server was structured to further distribute malware corresponding to the target environment Thing. In other words, malware containing CCleaner was the first step (first payload) to select targets of the targeted large enterprise and the delivery of the second payload to Honmar was the real purpose.

By combining the collected information, the database table for starting the second payload is completed.

Analyzing "OK" in the database table and excluding duplicate entries, it turned out that the second payload was sent to 20 systems. Talos reports the possibility of attacks on these 20 organizations.

The number of government-related systems in the world that may be affected by this cyber attack is "540"

The attack target system belonging to the domain containing the word "bank" is "51".

According to Talos, the code of this cyber attack is very complicated and obfuscation measures are applied, and the internal structure is hidden by anti-debug / anti-emulation technique. Also, the existence of a fileless third payload which is written directly to the memory area without being written to the storage has been confirmed.
In the process of data analysis, we know that the timeline of the command server was set based on China, but considering the altitude of the cyber attack method, it is difficult to distinguish the investigation from the Bluff It is pointed out that there is a possibility.

Kaspersky Laboratory is known as a hacking organization with high technical strength from the commonality of code "Group 72"Is pointed out.

The second stage attack found by the analysis by Talos is a limited thing that took place from 12th September to 16th October 2017. CCleaner with malware has been downloaded and distributed for about one month and installed on the terminal of 2.27 million users, so it is pointed out that the range of actual attacks is wide.
Originally, it was found that CCleaner's malware contamination problem, which was thought to be the purpose of collecting information such as CCleaner user's IP address and MAC address, was only a stepping stone for cyber attacks aimed at a specific large company For the most part, Talos advises users installing the 32-bit version of CCleaner v5.33.6162 or CCleaner Cloud v1.07.3191, not only to update to the new CCleaner, but also to format the entire system.
Related Posts: