It is clear that the malware of the cyber attack group 'Turla' targeting government agencies also uses satellite lines
By
Security companies Kaspersky and Symantec have pointed out that cyber-attack groups ' Turla ' targeting government agencies and embassies are using malware for reconnaissance activities. Turla has been espionage for at least five years, and it has been revealed that the malware used by Turla also uses satellite lines.
Satellite Turla: APT Command and Control in the Sky --Securelist
https://securelist.com/blog/research/72081/satellite-turla-apt-command-and-control-in-the-sky/
The cyber attack group 'Turla', which has been spying on government agencies, embassies, the military, pharmaceutical companies, educational institutions, etc. using the malware 'Wipbot', has been conducting 'long-term surveillance activities' for at least five years. The shift to '' has been revealed by a Symantec survey. In addition, Symantec said, 'From the characteristics of the selected target and the advanced technology used for malware, it is thought that there is a group supported by the state behind the attack activity,' and spying activities at the national level. It points out that.
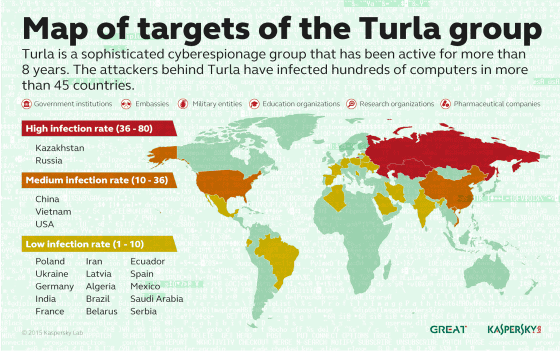
This is a map created by Kaspersky that shows the distribution of Turla's target locations. Kazakhstan and Russia were the most attacked, followed by China, Vietnam and the United States, followed by former eastern countries such as Poland, Ukraine and Latvia, South America such as Brazil, Mexico and Argentina, and Saudi Arabia. Damage is spreading all over the world, including the Middle East in Iran.
According to Kaspersky Lab's report, Turla uses an advanced rootkit such as 'Ouroboros' to set up an advanced backdoor called the Cobra / Carbon system on the targeted PC. Get full control of the system by connecting to the spy organization's command-and-control (C & C) server through backdoors known as 'World CupSec,' 'Tadj Makhal,' 'Wipbot,' and 'Tadvig.' As a result, the files on the PC may be deleted or sent to the outside, or the files may be sent and executed.
Turla has been found to infect target PCs with malware using two types of attack strategies: 'spear phishing' and 'watering hole attacks'. 'Spear-type phishing' is a method of sending an email to a target, opening the attached PDF file, and exploiting vulnerabilities such as Adobe Reader to infect malware.
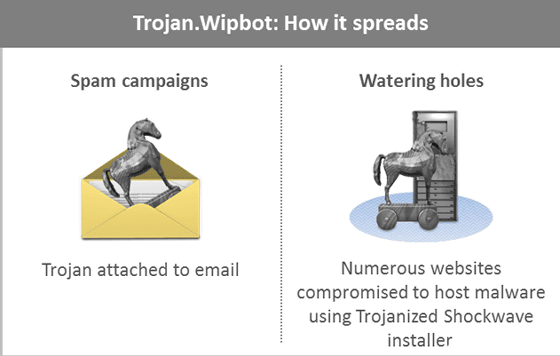
On the other hand, another 'watering hole attack' is to hack a website that the target PC frequently visits and embed malicious code, so that when the target browses the site, Java exploit or fake Microsoft Security How to infect malware via Essentioals etc. Kaspersky Lab has confirmed more than 100 websites infected with such malware, including the websites of local governments. A Symantec study also found that Turla has invaded at least 84 legitimate websites since September 2012, including many government and international websites. I am.
Turla's malware uses extremely high technology to steal information from target PCs, but attacks on the most important targets use satellite lines to prevent the location of C & C servers from being tracked. Kaspersky reveals.
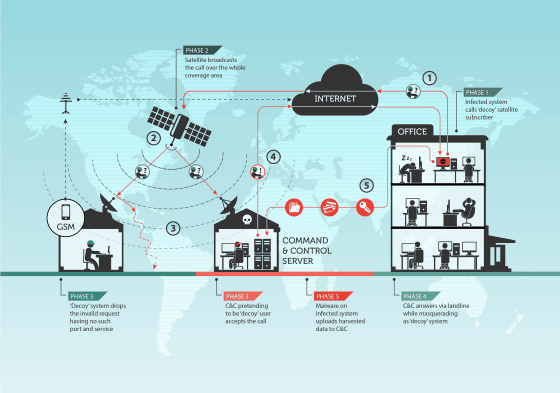
The C & C server is the 'keystone of the attack,' and for those who follow a cyberattack group, pinpointing their physical location is essential to tracking the group. However, cyber-attack groups take advantage of the fact that it is difficult to pinpoint the exact location because satellite network providers use satellite IP addresses that cover multiple countries and continents spanning thousands of square kilometers. That's why it protects the C & C server.
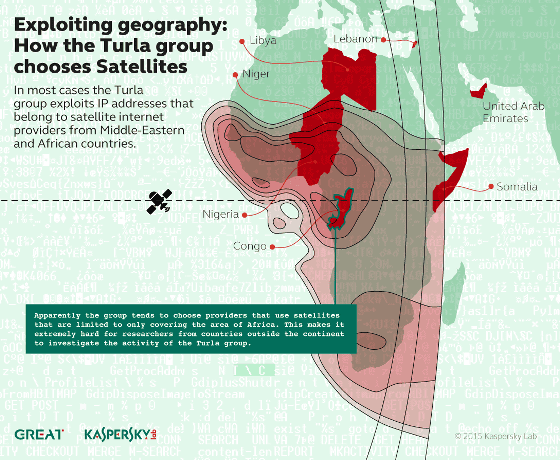
Kaspersky Lab's research has shown that Turla often uses satellite IP addresses assigned to Congo, Nigeria, Somalia in Africa, Lebanon in the Middle East, and the United Arab Emirates.
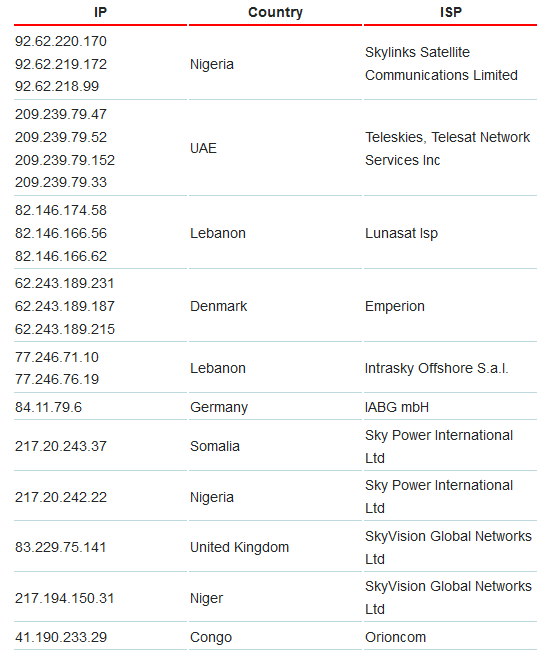
Based on the WHOIS information of the satellite IP address used by Turla, it looks like this when classifying countries and ISPs.
According to Kaspersky, it is clear that Turla's coding is not an English-speaking organization with many English grammar errors. Also, the fact that the system is compiled with a term that means Russian suggests that Turla is based in Russia. In addition, while Simantech avoids specifying the country name of Russia, 'the time stamps of attack activities occur within the standard business hours of the time zone that is almost 4 hours ahead of UTC (Coordinated Universal Time).' Strongly suggests the involvement of Russia-based organizations.
Related Posts: