Cyber attack group 'Turla' used Dropbox to store stolen data

Turla Crutch: Keeping the “back door” open | WeLiveSecurity
https://www.welivesecurity.com/2020/12/02/turla-crutch-keeping-back-door-open/
Turla Crutch attacks Ministry of Foreign Affairs in an EU country, misuses Dropbox in cyber-espionage, ESET discovers | ESET
Russian hacking group uses Dropbox to store malware-stolen data
https://www.bleepingcomputer.com/news/security/russian-hacking-group-uses-dropbox-to-store-malware-stolen-data/
Researchers at security firm ESET have discovered previously undocumented backdoor malware and document theft tools. The malware has been given the name ' Crutch ' by its creator.
When I examined 'Crutch', there was a similar part with the second stage backdoor malware 'Gazer' that Tulra used from 2016 to 2017. Since the malware used by Turla has not been shared with other groups, it was found that 'Crutch' is the malware used by Turla.
It has been suggested that Crutch, like the other tools Turla uses, is used only for specific targets, confirmed to have been used from 2015 to early 2020. I am.
On the other hand, it was confirmed that Crutch and the third stage backdoor malware 'FatDuke' existed at the same time on one machine. There is no evidence that the two malware interact, and each may have attacked the same machine independently.
According to ESET, Turla used Crutch's toolset on multiple machines from the Ministry of Foreign Affairs of an EU country. The tool was designed to leak sensitive documents and other files to Dropbox accounts managed by Turla operators.
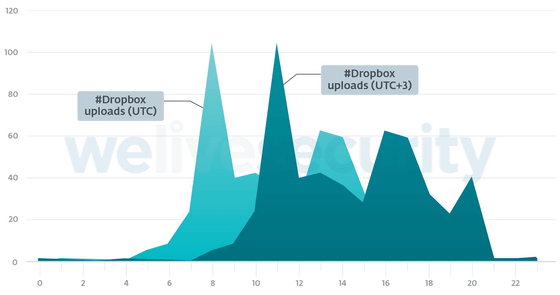
The graph below is a graph of some of the movements of the captured file along the time axis. Light green is when the time stamp is set to Coordinated Universal Time (UTC), and dark green is when the time stamp is set to ' UTC + 3 '. 'UTC + 3' is a time zone that includes Turkey, Saudi Arabia, Belarus, Moscow, Russia, etc. Since the time stamp can be said to indicate the working time of the operator, it can be estimated that the operator in the 'UTC + 3' time zone is working from 8:00 to 20:00.
It seems that 'Crutch' is not a first-stage backdoor, but a tool that is deployed after an attacker breaks into the network. After versions 1-3 with backdoor commands were used from 2015 to 2019, version 4 will stop supporting backdoor commands in 2019 and automatically upload files on local and removable drives to Dropbox. It is said that it has appeared.
The discovery further strengthens the perception that Turla is an organization with the resources to operate large and diverse tools.
Related Posts:
in Security, Posted by logc_nt