Russian cyber espionage group Secret Blizzard is hijacking and attacking other hackers' servers and infrastructure

A tracking campaign conducted by US telecommunications company
Snowblind: The Invisible Hand of Secret Blizzard - Lumen Blog
https://blog.lumen.com/snowblind-the-invisible-hand-of-secret-blizzard/
Frequent freeloader part I: Secret Blizzard compromising Storm-0156 infrastructure for espionage | Microsoft Security Blog
https://www.microsoft.com/en-us/security/blog/2024/12/04/frequent-freeloader-part-i-secret-blizzard-compromising-storm-0156-infrastructure-for-espionage/
Russian hackers hijack Pakistani hackers' servers for their own attacks
https://www.bleepingcomputer.com/news/security/russian-hackers-hijack-pakistani-hackers-servers-for-their-own-attacks/
On December 4, 2024, Black Lotus Labs , the cyber threat research and operations division of Lumen, published a report on the threat actor 'Turla,' which it has been tracking in collaboration with Microsoft since January 2023. According to the report, Turla, which has been active since December 2022, has been deploying malware tools by accessing networks previously infiltrated by the Pakistani threat actor 'Storm-0156.'
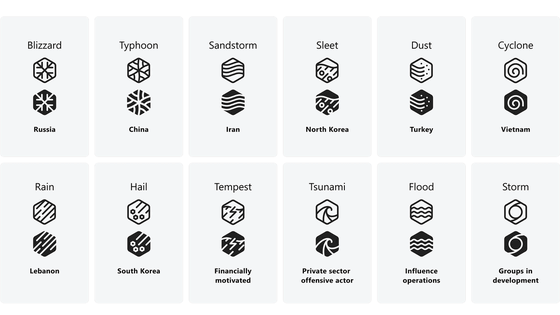
Microsoft has announced rules for naming malicious threat actors after meteorological phenomena, naming Russian threat actors 'XX Blizzard.' Turla uses a network of Pakistani threat actors, but the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has linked Turla to Center 16, the intelligence division of the Russian Federal Security Service, so the report calls it 'Secret Blizzard,' following Microsoft's naming rules.
Microsoft launches new rules to name malicious threat actors from Russia, North Korea, China, etc. after meteorological phenomena such as 'tsunami, typhoon, blizzard, etc.' - GIGAZINE
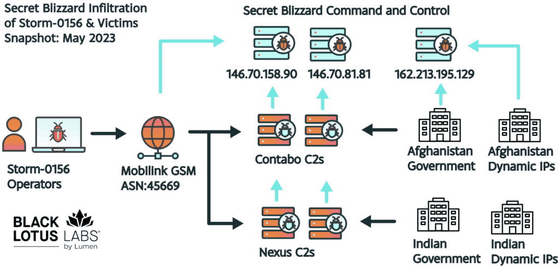
Storm-0156 mainly targeted government agencies in Afghanistan and India, intercepting, collecting and decrypting data. Lumen has been monitoring Storm-0156's activities for years, and discovered a control server for Storm-0156 during monitoring. The server was observed to be communicating with a virtual private server (VPS) IP address known to be associated with Russian hackers, which led to the existence of Secret Blizzard.
Secret Blizzard compromised several Storm-0156 control servers in late 2022 and deployed its own malware payloads, including backdoors and downloaders. Lumen also identified patterns of data transfer that were inconsistent with previous tactics employed by Storm-0156 to identify Secret Blizzard's activities.
According to Microsoft, Secret Blizzard's access to Storm-0156 appears to have been primarily used to install backdoors into Afghan government institutions, including the Afghan Ministry of Foreign Affairs, the Afghanistan General Intelligence Directorate , and the Afghan government's foreign consulates. Lumen explains that 'compromises are particularly easy to execute in the threat actor environment, as nation-state groups are unable to protect themselves with cutting-edge security tools.'
The following is a diagram showing Secret Blizzard's activities by Lumen. The light blue at the top of the diagram shows Secret Blizzard's commands, which are executed from backdoors created in Storm-0156 and Afghanistan government networks. Microsoft points out that Secret Blizzard's careful approach of hijacking existing threat actors to hide its identity may be related to political considerations.
Lumen said, 'Secret Blizzard, under the umbrella of the Federal Security Service of the Russian Federation, has consistently used sophisticated techniques to achieve its objectives while maintaining the secrecy of its operations. Secret Blizzard's unique strategy is to shift the blame to other threat actors when responses to threats reveal network exploitation. We published this report because we believe that approaches like Secret Blizzard's will continue to persist as Western countries, including the United States and Europe, continue to condemn Russian cyber activities. Black Lotus Labs will continue to monitor and track Russian state activity clusters to help protect and secure the Internet.'
Microsoft also stated, 'Secret Blizzard frequently hijacks the infrastructure and tools of other threat actors, suggesting that this is an intentional tactic and technique used by Secret Blizzard. The approach of hijacking other threat actors has both advantages and disadvantages. By leveraging other people's campaigns, Secret Blizzard can gain a foothold in networks of interest with relatively minimal effort. On the other hand, because the target of the attack is limited to the original threat actor's target of interest, the information obtained through Secret Blizzard's techniques may not be fully aligned with the priorities of the information they want to collect. In addition, if the operational security of the threat actor who established the initial foothold is insufficient, network security alerts may be triggered in the tools deployed by the actor who carried out the initial breach, unintentionally exposing Secret Blizzard's activities.' The results of the investigation are summarized as follows:
Related Posts:
in Security, Posted by log1e_dh







