Google's threat analysis group reveals that Russian government-backed hacking organizations are attacking Ukraine and surrounding areas with phishing scams and DDoS attacks

Google's
An update on the threat landscape
https://blog.google/threat-analysis-group/update-threat-landscape-ukraine/
Since Russia's invasion of Ukraine began, online security has never been more important to people in Ukraine and its surrounding areas. Government agencies, independent media outlets, and public service providers need security to establish secure communications in order to function properly. Google's TAG is working 24 hours a day, focusing on platforms that help users access and share important information, establishing security and security for their users.
TAG has been working for many years to take action against the threatening actors around Ukraine, warning of the existence of hundreds of government-sponsored attacks against Ukrainian users in the last 12 months. I did. This government-backed attack is primarily from Russia.
Over the past two weeks, TAG has been monitoring the activities of threat actors such as ' Fancy Bear ' and ' Ghostwriter .' It seems that these threat actors have carried out a wide range of cyber attacks from espionage to phishing .

Fancy Bear is known to be a threat actor associated with the GRU, the Russian Government's intelligence agency, and has several large-scale credential phishing
The following is one of the web pages used for credential phishing attacks. The domains actually used for credential phishing attacks are 'id-unconfirmeduser.frge.io', 'hatdfg-rhgreh684.frge.io', 'ua-consumerpanel.frge.io', 'onsumerspanel.frge.io' and so on.
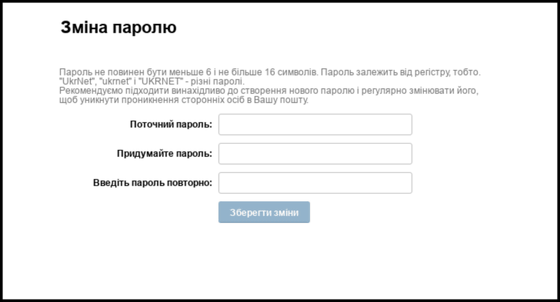
Another threat actor, Ghostwriter, has launched a credential phishing attack on Polish and Ukrainian government and military organizations in the past week. This attack seems to target users of email providers such as 'i.ua', 'meta.ua', 'rambler.ru', 'ukr.net', 'wp.pl', and 'yandex.ru'. The domains used for credential phishing attacks by Ghostwriter are 'accounts.secure-ua.website', 'i.ua-passport.top', 'login.creditals-email.space', and 'post.mil-gov.space'. Five of 'verify.rambler-profile.site'.
Please note that these domains are blocked by Google Safe Browsing .
In addition, China-based threat actor Mustang Panda is also conducting a cyberattack on European organizations in connection with Russia's invasion of Ukraine. According to TAG, Mustang Panda used an attachment with the filename 'Situation at the EU borders with Ukraine.zip' to carry out the attack. This file contains an executable file with the same name, which downloads multiple additional files to load the final payload. According to TAG, Mustang Panda is a threat actor who was originally in Southeast Asia.
In addition, as DDoS attacks targeting Ukrainian websites continue to be detected, TAG has said that Ukrainian government websites, embassies around the world, and government sites around conflict areas remain online and themselves. We are announcing that we have expanded the coverage of Project Shield , a free protection tool against DDoS attacks, to protect it. According to TAG, more than 150 websites in Ukraine, including many media outlets, use Project Shield, and we recommend that all targeted organizations register with Project Shield.
Related Posts:
in Security, Posted by logu_ii