Over 12,000 attacks by government-supported hacker groups occurred in three months worldwide, including Japan

by
An activity report of `` Threat Analytis Group (TAG) '' that is countermeasures against attacks on Google services was announced, and attacks such as phishing were carried out in Japan all over the world by a hacker group supported by the government It has become clear that the number has exceeded 12,000 in three months.
Protecting users from government-backed hacking and disinformation
https://blog.google/technology/safety-security/threat-analysis-group/protecting-users-government-backed-hacking-and-disinformation/
Google's Threat Analysis Group (TAG) has been active for more than 10 years to prevent targeted attacks against Google services, including Gmail and Google Drive. TAGs are mainly monitored by more than 270 hacker groups supported by governments in more than 50 countries, whose activities began with information gathering and intellectual property theft, and dissident activists. Attacks targeting cyber, cyber attacks, and the spread of fake news.
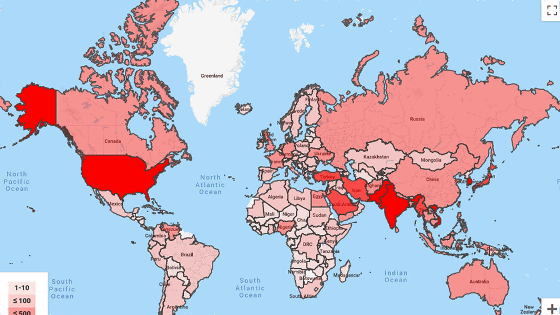
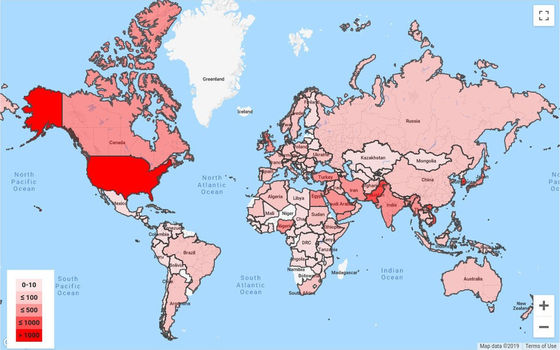
Phishing is a particularly popular attack method used by government-supported hacker groups, and more than 12,000 cases have been confirmed in the three months from July to September 2019. The following image is a map showing the distribution of countries attacked by government-backed hacker groups. Attacks are particularly common in the United States, Pakistan, South Korea, and Vietnam, but about 500 cases have been reported in Japan.
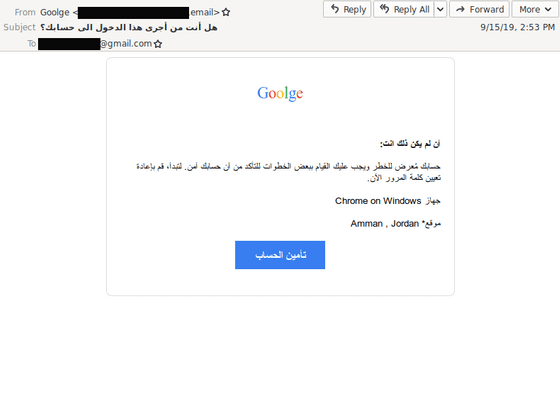
According to TAG, more than 90% of phishing by these government-supported hacker groups came from “credential phishing emails”. “Credential phishing emails” are attacks through emails disguised as security reports by Google, for example. Clicking the fake link button attached to the email opens a screen asking for a password update or security code, and attempts to hijack the user's account.
Among the hacker groups monitored by TAG, the most prominent activity is “Sandworm”, supported by the Russian government. In October 2019, it became clear that a group called `` Tsar Team (common name: Fancy Bear) '' supported by Russia was attacking anti-doping organizations around the world, but `` Sandworm '' is also
You can read more about the attacks on anti-doping organizations by Russian hacker groups in the following articles:
It turns out that Russian-backed hacker groups were attacking anti-doping organizations around the world-GIGAZINE
by skeeze
One of the distinctive activities of `` Sandworm '' is an attack by malware camouflaged as a fake application.In December 2017, a fake traffic information application targeting Korean Android users was uploaded to the Google Play store. It was.
The fake traffic information app uploaded by 'Sandworm' was deleted by TAG before being downloaded 10 times, but a more sophisticated attack was confirmed in November 2018. First, “Sandworm” hijacks the account of a real developer who has released several popular apps that have been downloaded more than 200,000 times via phishing emails, and mixes backdoors into the app code. Uploaded to the Google Play store with the developer's signature. However, this app was also detected in advance by TAG, and no user had downloaded the app.
In addition, TAG has identified and suspended 15 Google accounts and YouTube channels that used Russian-related fake information and information manipulation based in multiple African countries such as Central African Republic, Sudan, Madagascar, and South Africa. It was. In addition, a total of 28 YouTube channels were closed when a government-supported hacker group that had been running an anti- freedom Papua campaign in Papua and West Papua, Indonesia was identified.
Google said, “We want to prevent future attacks and improve security awareness by proactively disclosing the latest information on attacks detected by TAG in the future” He clarified the idea of embarking on a hacking measure supported by a government.
Related Posts:
in Security, Posted by log1l_ks