The threat spyware that names the name "Sauron's eyes" has appeared, and the possibility of a crime by a national-level spy group also

ByPascal
Adventurous novels that were also filmized "The Lord of the Rings" "The Adventures of the Hobbit" Appeared in the Hades ·Sauron. Since that Sauron is only the soul that lost the body, it appears as a huge first eyelid "eyes of Sauron" in the work, and it is drawn as a symbol of awe as "Eye seeing everything". It revealed the existence of terrible spyware which names the "eyes of Sauron".
Researchers crack open unusually advanced malware that hid for 5 years | Ars Technica
http://arstechnica.com/security/2016/08/researchers-crack-open-unusually-advanced-malware-that-hid-for-5-years/
ProjectSauron: top level cyber-espionage platform covertly extracts encrypted government comms - Securelist
https://securelist.com/analysis/publications/75533/faq-the-projectsauron-apt/
Strider: Aiming "Sauron's eyes" on target Cyber Spy Group | Symantec Connect Community
http://www.symantec.com/connect/ja/blogs/strider-0
It is clear that there is a group called Strider that spy acts on specific targets such as Russia, China, Sweden, Belgium, etc. using spyware. According to Symantec of security software development, Strider seems to be using high-performance spyware called "Remsec", which forms a backdoor among intruding computers and records typing information of computer users It seems to have the function to do and steal files in the computer.
The letters "SAURON (Sauron)" are contained on this Remsec keylogger module, and from this, Kaspersky, who develops security software like Symantec, calls the same spyware "Project · Sauron" I will.
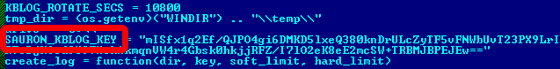
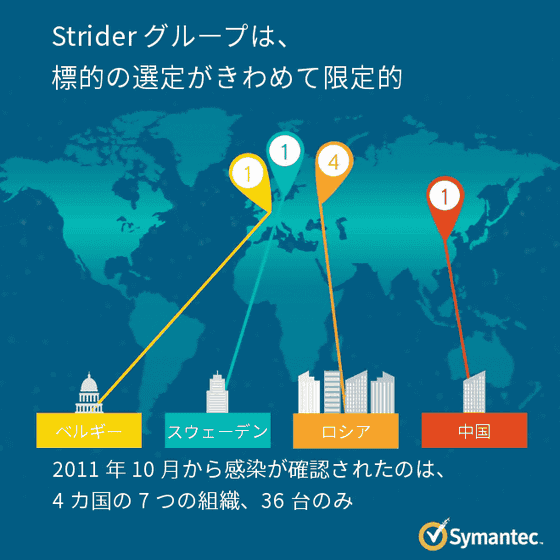
Symantec confirmed Remsec infection only in seven organizations in four countries of Russia, China, Sweden and Belgium, with only 36 infected computers. Spy is targeted at numerous organizations and individuals in Russia, one airline in China, one organization in Sweden (organization details are unknown), one embassy in Belgium, only a small number of organizations It is a spy act aimed at.
Symantec obtained Remsec samples from one customer. As Remsec's design is modular, each module works as a framework that allows an attacker to fully control the infected computer, so attackers can extract data while moving between networks and deploy custom modules as needed I heard that you can do it. Also, since Remsec has many stealth functions, it is difficult to detect using Remsec with conventional antivirus software. In addition, many Remsec functions are deployed on the network, so they only exist on the memory of the computer and are not stored on the disk, so it seems to be more difficult to detect. Because of these characteristics, the group called Strider that uses Remsec can be thought of as "an attack group with advanced technical power," Symantec.
When Symantec confirms it, there are six types of Remsec custom modules, which are as follows. The character string "Sauron" is found in the code of the keylogger module which is one of this custom module.
· Loader:It is a module named MSAOSSPC.DLL that loads and executes files from disk. The file on the disk contains the executable BLOB payload. Another function of the loader is the recording of the data log. For executable BLOBs and data encryption and decryption key iteration 0xBAADF00D is used. The loader is implemented as a fake security support provider to ensure persistence as well.
· Lua module:In some examples of Remsec, modules written in the programming language Lua are used. Remsec runs the Lua module using the Lua interpreter, and the Lua module performs each function. The Lua module is also stored in BLOB format which can be executed like the loader. The Lua module has the following functions.
- Network loader:Load and execute the executable file on the network. RSA / RC6 encryption may be used.
- Host loader:Load at least three other Lua modules into the running process. In this case we refer to three modules named ilpsend, updater (these two have not been discovered so far), kblog (which seems to be the keylogger module described below).
- Keylogger:It records the keystrokes, extracts the data, and sends it to the server managed by the attacker. This is the module with the string "Sauron" in the code. Considering that function, there is a possibility that the attacker made a nickname of this module named after the devil king of the clairvoyant appearing in the "ring story".
· Network listener:Many Remsec implement different technologies when opening a network connection based on the monitoring of certain types of traffic. Types of traffic include ICMP, PCAP, RAW network sockets and so on.
· Back door of basic pipe:Minimal backdoor module, controlled by named pipes. Executable BLOB format data or standard executable file format data can be executed.
· Advanced pipe back door:You can use more commands than basic pipe, such as send executable BLOB, list file, read / write / delete file.
· HTTP backdoor:This module contains multiple URLs of Command & Control (C & C) server.
It is possible to create such advanced custom tools, Strider has been operating for a period of at least 5 years without involving a malware detection network, and Remsec has a very advanced cyber spy function, and target Considering the nature of the organization that he is referring to, Strider says "The possibility of a national attack group will emerge," Symantec said. In addition, Symantec products and Norton products have this spyware "Backdoor.RemsecIt is detected as ".
In addition, Symantec and Kaspersky publish reports on Spyware / Remsec, respectively, at the same time.
(PDF)Security Response Custom Report - Symantec_Remsec_IOCs.pdf

(PDF)The-ProjectSauron-APT_research_KL.pdf

Related Posts:
in Security, Posted by logu_ii







