Details of the zero-day vulnerability ``Triangulation'' that allows you to access sensitive iPhone data just by sending an iMessage are released, and it is also revealed that secret hardware functions were used
Kaspersky Lab, the security company that discovered this vulnerability, has announced the analysis results of the vulnerability ``Triangulation'' that enables zero-click attacks on Apple devices, which was discovered and fixed in June 2023.
Operation Triangulation: The last (hardware) mystery | Securelist
4-year campaign backdoored iPhones using possibly the most advanced exploit ever | Ars Technica
https://arstechnica.com/security/2023/12/exploit-used-in-mass-iphone-infection-campaign-targeted-secret-hardware-feature/
Triangulation is a vulnerability that allows access to sensitive data on a device, including the microphone and camera, simply by sending an iMessage, and Kaspersky Lab has confirmed that it has been exploited for at least four years since 2019. . This vulnerability could be attacked not only on iPhones but also on Macs, iPods, iPads, Apple TVs, and Apple Watches. Detecting infection is extremely difficult, even for people with advanced knowledge.
Apple has implemented a security update that fixed a zero-day vulnerability, and it may have already been exploited - GIGAZINE

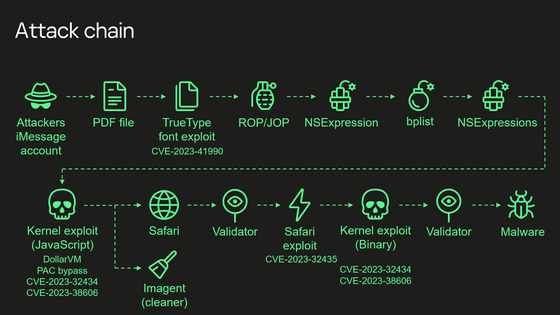
On December 27, 2023, Kaspersky Lab published the results of its Triangulation analysis. The attack chain is shown in the diagram below.
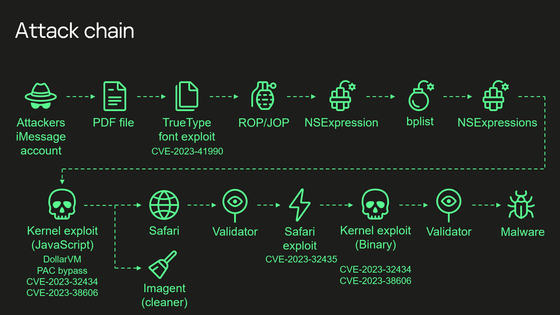
At each stage of the chain, the attack is carried out as follows.
1: Attacker sends malicious attachment via iMessage
The application processes this file without any notification to the user.
2: Exploiting remote code execution vulnerability
This vulnerability had existed since the early 1990s until it was removed with a patch.
3: Privilege escalation exploit written in JavaScript is executed
Patch the JavaScriptCore library with multiple stages written in ROP/JOP and NSExpression/NSPredicate query languages. Although this JavaScript code has been obfuscated and minified , it is approximately 11,000 lines of code, and is said to analyze and manipulate JavaScriptCore and kernel memory.
4: Get the ability to execute native API functions
Use DollarVM ($vm), a debugging feature of JavaScriptCore, to manipulate JavaScriptCore's memory and obtain the ability to execute native API functions. It supports both old and new iPhones, and also has a mechanism to bypass Pointer Authentication Code (PAC) .
5: Gain read/write access to the entire physical memory of the device at the user level
It exploits the XNU kernel memory mapping system call and integer overflow vulnerability CVE-2023-32434 to gain user-level read/write access to the device's entire physical memory.
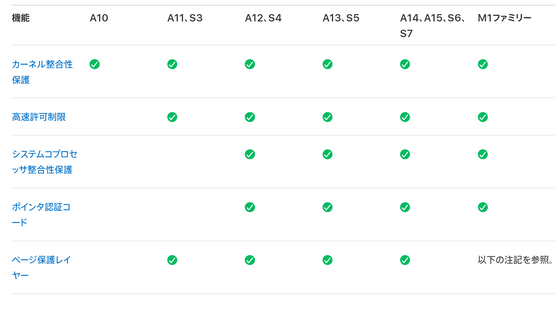
6: Bypass page protection layer
Bypass the page protection layer using memory-mapped I/O registers. This vulnerability has been fixed as CVE-2023-38606 .
7: Erasing and verifying traces
At this stage, it is possible to perform all sorts of operations on the device, including running spyware, but the Triangulation attacker now erases any traces of the intrusion and launches Safari in hidden mode to verify the victim. He said that he had set it to access a web page for.
8: Malware installation
If the validation 'passes', shellcode is executed using

In this attack chain, some memory-mapped I/O addresses used by the attacker to bypass the page protection layer did not exist in the device tree . This address allows arbitrary data to be written to any physical address, bypassing hardware-based memory protection systems. This address is not used in the firmware or in the chip's hardware registers, and Kaspersky researchers suspect it was a feature that was either included for debugging or testing purposes, or was included by mistake.
Kaspersky researchers looked everywhere, including source code, kernel images, and firmware, but found no mention of memory-mapped I/O addresses, and how the Triangulation attackers were able to figure out how to use these addresses. He says it is a mystery whether he knew about it.
Regarding Triangulation, the Russian Federal Security Service (FSB) claims that ``American intelligence agencies cooperated with Apple and planted malware in order to obtain information from Russian diplomats,'' but Apple is suspicious. is denied.
``Apple cooperated with the US government for the purpose of spying on Russia,'' the Russian Federal Security Agency claims, ``Apple devices are a spyware paradise'' - GIGAZINE

Related Posts: