You can find a bug that makes it possible to access photos, call history, messages, etc. of iPhone or Mac

A vulnerability has been discovered in both iOS and macOS that allows code signing to be bypassed and arbitrary code to be executed. By exploiting this vulnerability, attackers can access photos, call history, messages, etc. on iOS / macOS devices.
Trellix Advanced Research Center Discovers a New Privilege Escalation Bug Class on macOS and iOS
https://www.trellix.com/en-us/about/newsroom/stories/research/trellix-advanced-research-center-discovers-a-new-privilege-escalation-bug-class-on-macos-and- ios.html
Ever since the original iPhone came with iOS, Apple has carefully placed limits on what software can run on its mobile devices. Specifically, the iPhone can only run applications signed by Apple-trusted developer certificates, and there is no scripting language like AppleScript on iOS. The ability to dynamically execute code has been almost completely removed, creating a powerful barrier to exploits that must find a way to execute malicious programs. And as Apple ported iOS features to macOS, it began to strictly enforce code signing on macOS as well.
However, a vulnerability team at the Trellix Advanced Research Center, the research arm of cybersecurity firm Trellix, has been able to bypass code signing on iOS and macOS to allow arbitrary code to be executed in the context of multiple platform applications. I discovered a new vulnerability that you can. This vulnerability allows privilege escalation and sandbox evasion on both iOS and macOS. If this vulnerability is used by malicious applications or exploits, it may be possible to access sensitive information such as user's messages, location information, call history, photos. The severity of this vulnerability is moderate to high, with a CVSS score of 5.1 to 7.1.
The video embedded in the tweet below shows in an easy-to-understand manner how a malicious attacker steals notifications and location information using the vulnerability discovered by Trellix.
Today, we published our discovery of a new bug class fundamentally affecting Apple's security model. Austin Emmitt ( @alkalinesec ) breaks down the full story on the blog. https://t.co/DwmPkn2O2s
—Trellix Advanced Research Center (@TrellixARC) February 21, 2023
Summary of our research (and a reminder to update your devices) below .
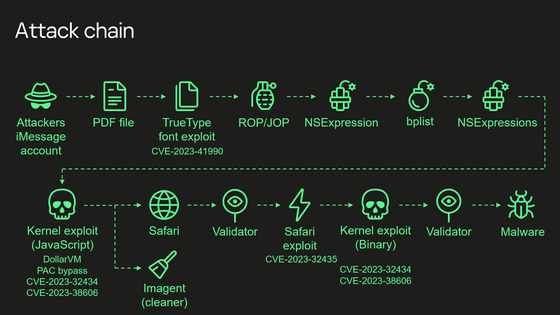
In 2021, Citizen Lab announced `` FORCEDENTRY '', a zero-click exploit used in iPhone spyware Pegasus. Citizen Lab analyzed FORCEDENTRY in cooperation with `` Project Zero '', a security team tasked with discovering zero-day vulnerabilities within Google, and found that FORCEDENTRY is a framework used by iOS to draw images Core Graphics It has been revealed that it is possible to execute multiple codes by targeting vulnerabilities in the PDF processing of , and that it has a sandbox evasion mechanism.
Google's Project Zero points out that the zero-click exploit for the iPhone used in spyware Pegasus used for monitoring VIPs is ``the most technically sophisticated exploit''-GIGAZINE

This sandbox evasion mechanism included NSPredicate , which allowed developers to filter a list of arbitrary objects. NSPredicate's syntax is a full scripting language, so it's possible to dynamically generate and run code on iOS. Trellix explains that this creates a completely new vulnerability that can completely break the interprocess security of macOS and iOS.
The vulnerability discovered by Trellix resides in 'coreduetd', a process that collects data about activity on the device. By executing code in a process with appropriate credentials such as Messages or Safari and sending a malicious NSPredicate, it will be possible to execute code with the privileges of this process. This process runs with root privileges on macOS, allowing the attacker to access the user's calendars, contacts, and photos. A very similar issue with the same impact also exists in the related process 'contextstored', allowing an attacker to execute code from a process with heavy access to the device using the vulnerable XPC service. It is said that it will be possible to cause behavior like FORCEDENTRY.
iOS 'appstored' and macOS 'appstoreagent' daemons also have vulnerable XPC services, and attackers who control processes that can communicate with these daemons can exploit these vulnerabilities to install arbitrary applications, including system apps. It is possible to
These vulnerabilities also exist in services accessible by arbitrary apps that do not require entitlements. Trellix first found the vulnerability in 'OSLogService', which is an XPC service that could be used to read potentially important information from syslog. In addition, by exploiting the NSPredicate vulnerability of UIKitCore on the iPad, attackers can access sensitive data such as location information, camera, microphone, call history, and photos, and delete these data from the device. It seems that it will be possible.
The above vulnerabilities have been fixed in macOS 13.2 and iOS 16.3 released by Apple, ``Thank you to Apple for working with us quickly to resolve the issue,'' Trellix wrote.
Related Posts: