Google's Project Zero points out that the zero-click exploit for iPhones used in the spyware Pegasus, which was used to monitor important people, is the 'most technically sophisticated exploit'

Project Zero: A deep dive into an NSO zero-click iMessage exploit: Remote Code Execution
https://googleprojectzero.blogspot.com/2021/12/a-deep-dive-into-nso-zero-click.html
NSO Group used fake GIFs to hack Apple iMessage - Security - iTnews
https://www.itnews.com.au/news/nso-group-used-fake-gifs-to-hack-apple-imessage-574081
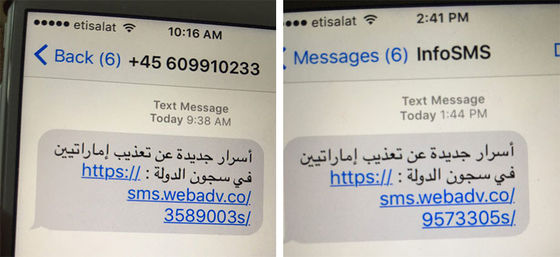
Pegasus, a spyware provided by NSO Group, has been used for years to monitor the smartphones of specific targets. Initially, Pegasus sent a URL like the one in the image below via SMS, and if the target tapped (clicked) on the link, the device would be hacked. This type of exploit that hacks a device with a single click is called a one-click exploit.
However, NSO Group is said to be developing a zero-click exploit that does not even require a click. Because there is no need for a click, even people familiar with security-related technologies may not notice that their device has been hacked. Because zero-click exploits do not require user interaction, attackers do not need to send messages like one-click exploits. Zero-click exploits work secretly in the background, and Project Zero explains that 'there is no way to prevent this.' The zero-click exploit used by Pegasus is called '
FORCEDENTRY hacks the device by sending a message to the target via iPhone iMessage and displaying a GIF image attached to this message. When displaying a GIF image on iMessage, Apple has a specification that plays the video in an infinite loop rather than playing it only once. A process called 'IMTranscoderAgent' related to image preview and transcoding renders image files with the extension '.gif', but Project Zero points out that 'just because the file name ends with '.gif' does not mean that the file sent is really a GIF image.' NSO Group is believed to have secured a route for external code to enter by using a ' fake GIF image ' that pretends to be a GIF image that completely ignores the file extension.

In addition, FORCEDENTRY targets vulnerabilities in PDF processing in Core Graphics, a framework used by iOS to draw images, allowing it to execute multiple codes.
Project Zero describes FORCEDENTRY as 'one of the most technically sophisticated exploits we have ever seen.'
Project Zero thanks CitizenLab for providing samples of the FORCEDENTRY exploit developed by NSO Group for Pegasus, and Apple's Security Engineering and Architecture group for their technical analysis. However, the details of the zero-click exploit published this time 'do not necessarily reflect the views of these companies.'
Related Posts:
in Software, Smartphone, Security, Posted by logu_ii







