What kind of person was the target of the legendary Holy Grail 'Pegasus' that hackers sought?

From Pearl to Pegasus: Bahraini Government Hacks Activists with NSO Group Zero-Click iPhone Exploits --The Citizen Lab
https://citizenlab.ca/2021/08/bahrain-hacks-activists-with-nso-group-zero-click-iphone-exploits/
Zero-click iMessage Pegasus exploit defeated Apple's iOS 14 security | AppleInsider
https://appleinsider.com/articles/21/08/24/zero-click-imessage-pegasus-exploit-defeated-apples-ios-14-security
Phones of nine Bahraini activists found to have been hacked with NSO spyware | Bahrain | The Guardian
https://www.theguardian.com/world/2021/aug/24/phones-of-nine-bahraini-activists-found-to-have-been-hacked-with-nso-spyware
Pegasus Spyware Uses iPhone Zero-Click iMessage Zero-Day | Threatpost
https://threatpost.com/pegasus-spyware-uses-iphone-zero-click-imessage-zero-day/168899/
The nine activists found by The Citizen Lab in a survey are all human rights activists in the Kingdom of Bahrain in the Middle East. Bahrain is said to be 'the most oppressive nation in the Middle East,' and the Internet is severely censored. In 2020, a report from the human rights group Freedom House said , 'Many websites have been blocked, and social media users who have been spotted have been cross-examined by the security department and pressured to remove content. it has been imprisoned arrested by who posted the content to online 'and their situation has been reported . Three of the nine hacked are members of the left-wing party Waad, which was suspended on suspicion of terrorism in 2017, as well as bloggers, members of the Bahrain Center for Human Rights, and members of the opposition Alwifferk. Is included in the hack target.
One of the hacks was Moosa Abd-Ali , an activist and exile in London.

Several methods have been confirmed for hacking using Pegasus, and as of 2020, an attack using the zero-click vulnerability of iMessage called 'KISMET' was carried out targeting the iPhone equipped with iOS 13. .. However, with iOS 14, Apple
The hacks identified by The Citizen Lab this time were generally from June 2020 to February 2021. KISMET was used for hacking mainly in 2020, and FORCE DENTRY was held in 2021. Of the nine activist hacks, at least four were believed to have been carried out by a hacker named 'LULU' belonging to the Bahraini government. However, the two hacked activists lived in London, England at the time, and the Bahraini government used Pegasus to spy in Bahrain and Qatar. The Citizen Lab believes that a hacker from another government carried out the hack.
The iPhone hacked by KISMET between July and September 2020 was powered by iOS 13.5.1. When The Citizen Lab checked the log, the hacked iPhone had a crash in the 'IM Transcoder Agent' related to iMessages image preview and transcoding. After the crash, IMTranscoderAgent was confirmed to call WebKit to download and render items from a Pegasus-infected server. KISMET was implemented for at least iOS 13.5.1 and iOS 13.7, The Citizen Lab said.
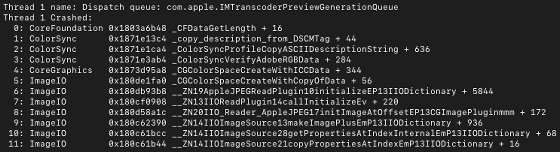
KISMET has been confirmed to be infected with spyware even if the recipient does not have access to the URL. Bill Marzac, a senior researcher at The Citizen Lab, said of KISMET: 'This is not only a very scary exploit, but also the legendary Holy Grail that hackers have sought to hack their devices. With this, you can operate other people's terminals normally, and you don't have to worry about it being distracted, 'he commented as of 2020.
Journalists hacked by government for 'zero-click vulnerability' hidden in iPhone iMessage-GIGAZINE

After that, when Apple introduced security measures BlastDoor in iOS 14, Pegasus's method will change. One of the activists reportedly received an SMS message with UR from a sender calling himself 'Mail Express' as soon as he updated to iOS 14 in September 2020.

Activists are believed to have accidentally previewed the content of the message when trying to copy it. This action caused the activist VPN to record a 'link opened' and redirected to the attacking hacker LULU, but the activist's iPhone was not infected with Pegasus. The Citizen Lab describes this case as 'an example of how the KISMET exploit cannot run on iOS 14'.
Then, between February and July 2021, a new 'FORCE DENTRY exploit' will be observed that avoids the Blast Door. According to the device log, this also caused a crash related to 'IMTranscoderAgent', and 'copyGifFromPath: toDestinationPath: error' was called in the file received through iMessage, causing a segmentation fault. In addition, The Citizen Lab reports that there are two patterns of crashes that have been successfully run on at least iOS 14.4 and iOS 14.6.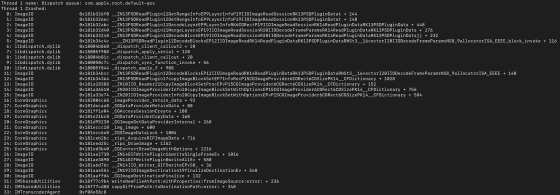
The Citizen Lab, with the consent of the activists targeted by the attack, reported these crashes to Apple and shared logs, and Apple is investigating the situation.
Related Posts:
in Security, Posted by darkhorse_log






