Microsoft hasn't fixed 8-year-old shortcut exploit used by North Korea, Russia, and China for espionage
Trend Micro has reported that a vulnerability in Windows shortcut files, ZDI-CAN-25373, discovered by Trend Micro's bug bounty program platform Zero Day Initiative (ZDI), is being exploited by cyber attack groups linked to North Korea, Iran, Russia, China, etc. Trend Micro has reported ZDI-CAN-25373 to Microsoft, but it has not been fixed in a security update.
ZDI-CAN-25373 Windows Shortcut Exploit Abused as Zero-Day in Widespread APT Campaigns | Trend Micro (US)
Microsoft isn't fixing 8-year-old zero day used for spying • The Register
https://www.theregister.com/2025/03/18/microsoft_trend_flaw/
ZDI-CAN-25373 could allow an attacker to execute malicious code on a user's machine by embedding a hidden command within a shortcut file.
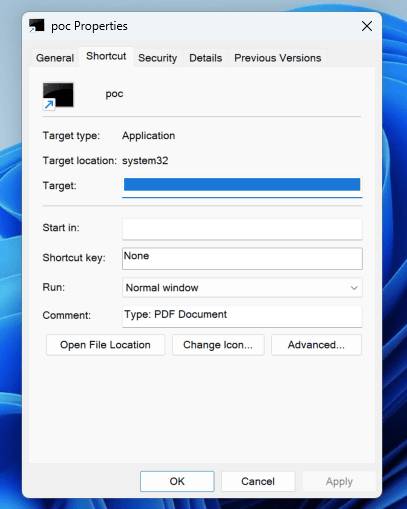
Shortcut files, which are binary files, have a specific structure and store command line arguments in an area called COMMAND_LINE_ARGUMENTS. If an attacker inserts a large number of whitespace characters into this COMMAND_LINE_ARGUMENTS section, enters a malicious command, and edits the shortcut file, the file can appear to be a normal document or a legitimate application.
If a user were to check the shortcut properties, the malicious command would be hidden in the Windows user interface due to the large amount of whitespace inserted. This is technically very simple, but difficult for the average user to detect.
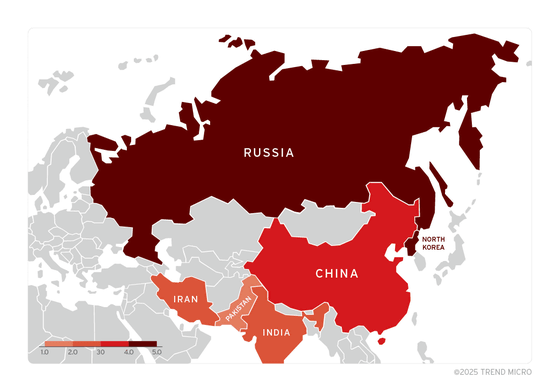
ZDI found approximately 1,000 malicious shortcut files and estimates that ZDI-CAN-25373 has been used in attacks since at least 2017. ZDI-CAN-25373 has been abused by nation-sponsored cyber attack groups such as North Korea, Iran, Russia, and China, with North Korea-related groups accounting for approximately 45.5% of the total attacks.
Around 68.2% of the attacks were aimed at information theft and cyber espionage, while around 22.7% were aimed at financial gain, primarily targeting government agencies, private companies, financial institutions, think tanks, telecommunications companies, the military and the energy sector.
ZDI reported ZDI-CAN-25373 to Microsoft, but Microsoft deemed it a user interface issue and decided not to address it as a security update. ZDI considers ZDI-CAN-25373 a significant security risk, and warns that when combined with a privilege escalation vulnerability, the entire system could easily be compromised.
'ZDI-CAN-25373 is one of many bugs that attackers are exploiting, but we're reporting it as a zero-day because it has not been patched,' Dustin Childs, ZDI's head of threat awareness, told The Register. 'Microsoft has not deemed it a security update that should be fixed, but it may be fixed in a future OS update or feature release.'
Related Posts:







