Google explains the attack method used by North Korean hacker group targeting security researchers on official blog

Google Threat Analysis Group (Google TAG) has revealed that
Active North Korean campaign targeting security researchers
https://blog.google/threat-analysis-group/active-north-korean-campaign-targeting-security-researchers/
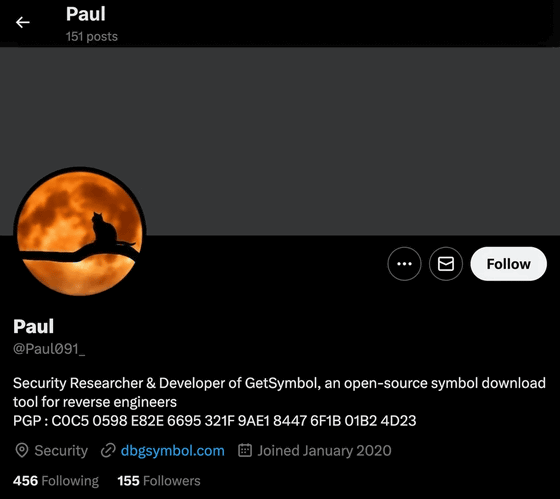
Attackers backed by the North Korean government use social media such as X (formerly Twitter) to build relationships with their target security researchers. In one case, he actually talked with the target on X for several months and even offered to cooperate with the target on a common topic.
Below is the profile of the account that the attacker actually created on X. In addition, the account was frozen at the time of article creation.
The attackers contacted their targets via X, then moved to messaging apps such as Signal and WhatsApp, maintaining relationships with their targets and sending them malicious programs, including at least one zero-day exploit. About. The malicious program sends information and screenshots collected on the target's device to
Google TAG has not disclosed the details of the vulnerability exploited by the zero-day exploit because the patch is being applied at the time of article creation. However, it has vowed to publish an analysis of the exploit and additional technical details in accordance with Google's vulnerability disclosure policy once a patch is applied.
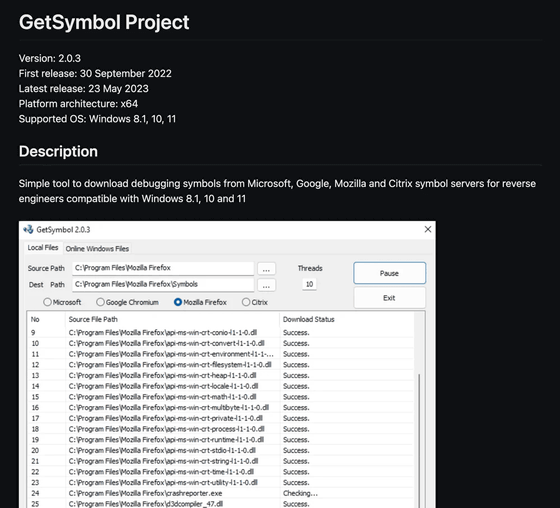
Furthermore, the attacker had also developed a tool for Windows called ``A tool to download debugging symbols from Microsoft, Google, Mozilla, and Citrix.'' The source code of this tool has been published on GitHub since September 30, 2022, and updates have been released several times. At first glance, it was ``a tool that allows you to quickly and easily download symbols from various sources,'' but in reality it also had the ability to download and execute arbitrary code from a server controlled by an attacker. .
Google TAG: 'We are committed to sharing our findings with the security community to raise awareness and share them with companies and individuals who may have been targeted by these activities. Understanding Tactics and Techniques We hope that by deepening our knowledge, we will be able to improve our ability to detect threats and improve user protection across the industry.'
Related Posts:
in Security, Posted by log1i_yk