What is a clever way for North Korean hackers to steal the contents of Gmail?

Security research firm
SharpTongue Deploys Clever Mail-Stealing Browser Extension 'SHARPEXT' | Volexity
https://www.volexity.com/blog/2022/07/28/sharptongue-deploys-clever-mail-stealing-browser-extension-sharpext/
North Korea-backed hackers have a clever way to read your Gmail | Ars Technica
https://arstechnica.com/information-technology/2022/08/north-korea-backed-hackers-have-a-clever-way-to-read-your-gmail/
North Korean Hackers Are Going After Gmail Accounts
https://futurism.com/north-korean-hackers-gmail-malware?amp
SharpTongue is a group that conducts hacks targeting individuals working for organizations in the United States, Europe, and South Korea that work on the topic of North Korean national security. Although there is some overlap with the hacker group known by other security researchers as Kimski , Volexity distinguishes SharpTongue from Kimski by categorizing the organizations they target.
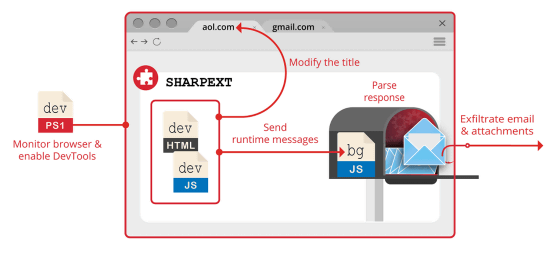
The newly reported hacking technique uses a malicious browser extension called ' SHARPEXT ', which was confirmed to be used by SharpTongue hackers in September 2021. Rather than trying to steal usernames and passwords, SHARPEXT is characterized by stealing emails and attachments when victims open their Gmail or AOL email accounts in a browser.
SHARPEXT has continued to evolve since it was discovered in September 2021, and is 'version 3.0' at the time of writing. Volexity says that the first version only supported Google Chrome, but the latest version 3.0 targets three browsers: Chrome, Edge, and Whale. Whale is a Chromium-based browser developed by Korean IT company NAVER, and is said to be used almost exclusively by Korean users.

According to Volexity, the hackers infiltrated the target device before deploying SHARPEXT and collected the browser's resources.pak file, the user's
The modified preference file preserves existing user-configured settings while loading SHARPEXT and related parameters, without the need for users to voluntarily install extensions.
SHARPEXT runs a PowerShell script that enables the browser's DevTools and checks the processes associated with the target browser in an infinite loop. At this time, the PowerShell script hides the DevTools and even hides the window that warns the victim, making it difficult for the victim to notice that the attack is underway.
Once installed, SHARPEXT will be able to upload Gmail and AOL email data and attachments to remote servers. Volexity also reports that it has a function to list emails collected from victims in the past, prevent duplicate emails from being uploaded, and a function to ignore specific email addresses.
Although cases of North Korean hackers using browser extensions have been confirmed in the past, it is almost always used as an infection source for attacks, and cases where attacks themselves are executed by browser extensions are rare.
Volexity says SharpTongue has been deploying SHARPEXT for over a year and has successfully collected thousands of emails from multiple victims. Volexity also points out that while SHARPEXT was an immature tool with many bugs in its early days, hackers have found value in operating SHARPEXT as it has become increasingly sophisticated through constant updates and maintenance. increase.
Volexity President Steven Adale warned that although SHARPEXT works only on Windows in the version at the time of writing, there is no reason not to extend it to macOS and Linux in the future.
Related Posts:
in Web Service, Security, Posted by log1h_ik







