What is the method of the hacker group 'GoldenJackal' that steals data from PCs isolated from the Internet via USB drives?

Mind the (air) gap: GoldenJackal gooses government guardrails
https://www.welivesecurity.com/en/eset-research/mind-air-gap-goldenjackal-gooses-government-guardrails/
GoldenJackal is a hacker group active since at least 2019, targeting government and diplomatic institutions in Europe, the Middle East and South Asia. Few details are known about the group, but the toolset reported by security firm Kaspersky in 2023 could all be used for espionage.
In May 2022, ESET's research team discovered a toolset that could not be associated with any hacker group. Because this toolset had similarities to the GoldenJackal toolset reported by Kaspersky, ESET began detailed analysis. As a result, two new toolsets used by GoldenJackal from 2019 to 2024 were identified. Details of the two toolsets are as follows:
◆2019 Toolset
The older version of the newly discovered toolset by ESET targeted the South Asian nation's embassy in Belarus in attacks believed to have been carried out in August and September 2019, and again in July 2021.
Below is a diagram of a series of air-gapped attacks by ESET. The attack requires three elements: an Internet-connected PC owned by the target, a USB drive, and an air-gapped PC that is the target. The Internet-connected PC is already infected with the worm component and a component called 'GoldenDealer'.
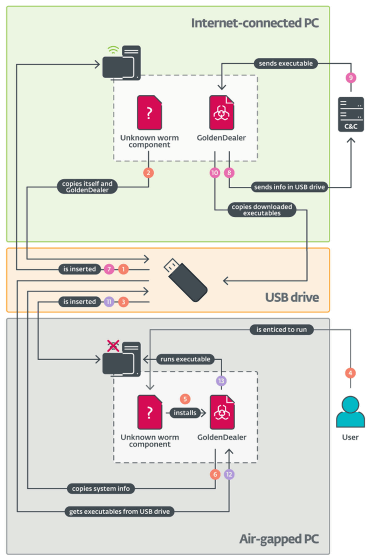
The flow of the attack is as follows:
1: When a user connects a USB drive to a PC connected to the Internet, the worm component and GoldenDealer that have already infected the PC are copied to the USB drive. At this time, the worm component hides by disguising itself as the last changed directory name on the USB drive.
2. A user then plugs the USB drive into an air-gapped PC and accidentally executes the worm component, which had been disguised as a directory name.
3. The worm component installs GoldenDealer on air-gapped PCs and copies system information to a USB drive.
4. When the USB drive is plugged back into a PC with Internet access, the information about the air-gapped PC stored on the USB drive is sent to the C&C server.
5: The C&C server sends a file to the USB drive to run on the air-gapped PC.
6. When the user plugs the USB drive back into the air-gapped PC, the files stored on the USB drive are executed.
The 2019 toolset uses three main components, one of which is 'GoldenDealer', which monitors the insertion and removal of USB and determines whether it is connected to an air-gapped PC or a PC connected to the Internet. GoldenDealer is responsible for downloading executable files from a C&C server when connected to the Internet and for executing files when connected to an air-gapped PC.
The second component is a modular backdoor called 'GoldenHowl' that performs a variety of functions, such as loading malware configurations from a JSON file, creating directories used by the malware, and supporting communication with the C&C server.
The third component is a simple component written in Go called 'GoldenRobo,' which is responsible for accessing each drive on the air-gapped PC and sending files to the C&C server.

New Toolset Used to Target European Government Agencies
Another toolset discovered by ESET was used in attacks targeting European government organizations between May 2022 and March 2024. This toolset similarly targeted air-gapped PCs, but used more sophisticated and modular components than the previous toolset.
The components identified in the new toolset are as follows: ESET classifies the eight components into four types: Collection, Distribution, Processing, and Exfiltration.
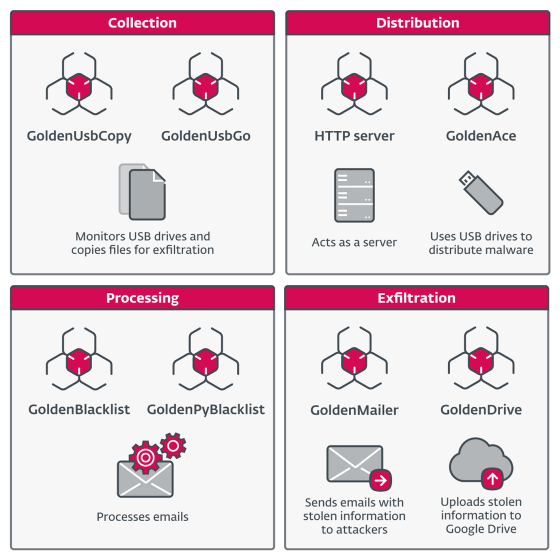
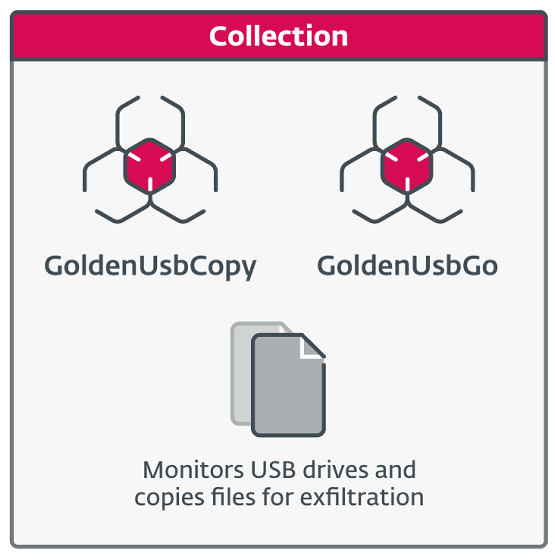
Among these, 'GoldenUsbCopy,' classified as 'collection,' is a component that monitors the insertion of a USB drive and copies files stored on the disk. 'GoldenUsbGo' is a similar component, but it provides the same functionality with a more sophisticated and simple implementation.
The component classified as 'Distribution' is used to spread other malicious executables and retrieve staged files via USB drives, and a packaged Python HTTP server is also included in the module.
The “processing” component, “GoldenBlacklist”, downloads the encrypted archive from a local server, examines emails and saves only messages of interest. “GoldenPyBlacklist” is a Python implementation of this.
The 'GoldenMailer' component, classified as a 'leak' component, steals files by sending emails with attachments to accounts controlled by the attacker, while the 'GoldenDrive' component has the ability to steal files by uploading them to Google Drive.
Conclusion
'In this blog post, we uncover two new toolsets that GoldenJackal has used to target isolated systems at government organizations, including in Europe, with common capabilities including the use of USB drives to steal sensitive documents,' ESET said. 'Deploying two different toolsets for compromising air-gapped networks in just five years indicates that GoldenJackal is an advanced threat actor that is aware of the network segmentation used by its targets.'
Although ESET has not linked GoldenJackal’s activities to any specific nation state, the use of language contained in GoldenHowl that is characteristic of Russian-speaking countries suggests that at least its developers are Russian speakers.
Related Posts:







