Malware discovered in iOS app that uses text image recognition to read confidential information for the first time

Security company Kaspersky has reported that it has discovered malware with text image recognition capabilities in Android and iOS apps. The malware, called ' SparkCat ,' has the ability to read the contents of screenshots taken by users, specifically targeting
SparkCat crypto stealer in Google Play and App Store | Securelist
https://securelist.com/sparkcat-stealer-in-app-store-and-google-play/115385/
Malware With Screen Reading Code Found in iOS Apps for the First Time - MacRumors
https://www.macrumors.com/2025/02/05/ocr-malware-app-store/
SparkCat is distributed through official app stores and requests permission to access images under the guise of seemingly legitimate functions, such as attaching images in support chats. According to Kaspersky, SparkCat began its activity around March 2024, and has been confirmed to infect apps on the App Store, such as ComeCome, WeTink, and AnyGPT. It is unclear whether these infections are the result of intentional actions by developers or a supply chain attack.
Once downloaded, the infected apps request permission to access the user's photos, and if granted, use OCR functionality to search for images with relevant text. The malware was allegedly primarily targeting iOS users in Europe and Asia.
According to Kaspersky, SparkCat is based on the Java SDK 'Spark' and upon initialization, it downloads a JSON configuration file from a GitLab URL, which is base64 encoded and encrypted with AES128 CBC mode , and if the configuration fails, the default settings are used.
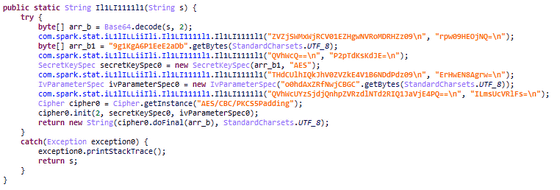
It uses POST requests to communicate with HTTP servers and encrypts data with
Kaspersky points out that the code is written in Rust , which is unusual for a typical mobile app, suggesting advanced technical capabilities behind the attack. In addition, analysis of the code suggests that the developer is familiar with Chinese, and error messages from the C2 server are also returned in Chinese, suggesting that a cybercrime group linked to China may be involved. However, Kaspersky states that 'there is insufficient data to make a definitive association with a specific cybercrime group.'
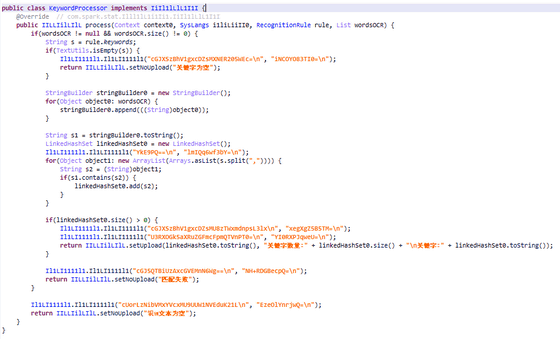
The malware's core functionality is text recognition , which uses Google's ML Kit library, and depending on the system language it loads different OCR (Optical Character Recognition) models capable of recognizing Latin, Korean, Chinese, and Japanese characters. Image processing is performed in three ways, combining keyword processing, word length processing, and localized dictionary processing.
The following is a food delivery app used in the United Arab Emirates and Indonesia, which had been downloaded more than 10,000 times on Google Play at the time Kaspersky began its investigation.
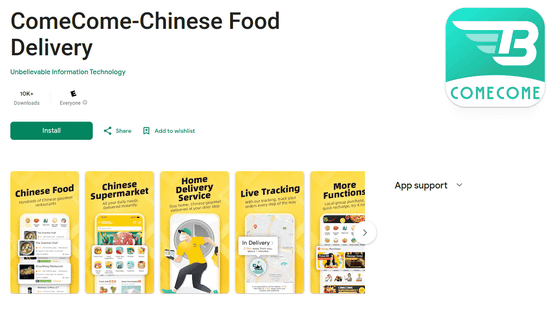
The food delivery app was also distributed on the App Store, but the iOS version was also infected with SparkCat. Further investigation revealed that several other apps were also distributed with SparkCat. Kaspersky said this is the first time that malware with OCR capabilities has been found on the App Store.

Kaspersky says that the distribution of malicious apps on the App Store with the explicit goal of identifying and stealing cryptocurrency wallet recovery phrases not only shows the increasing technical sophistication of attackers, but also that the App Store's review process and iOS security are not perfect.
Kaspersky urges users to 'delete any of the infected apps if they are installed on your device and do not reinstall them until a fix is released,' and 'do not save screenshots containing sensitive information, such as cryptocurrency wallet recovery phrases, to your gallery. Use a password manager or similar tool to manage your passwords and other sensitive information.'
Related Posts:
in Smartphone, Security, Posted by log1i_yk







