The existence of malware using the attack "Process Doppelgining" that can not be detected at last by security countermeasure is confirmed

"Hacking method of extremely difficult detection by security counter software"Process Doppelgangling (process doppel ganging)"Was announced in Black Hat Europe 2017 in December 2017, but finally the first malware using process doppelginingSynAckThe existence of "was confirmed.
SynAck targeted ransomware uses the Doppelgänging technique - Securelist
https://securelist.com/synack-targeted-ransomware-uses-the-doppelganging-technique/85431/
First-Ever Ransomware Found Using 'Process Doppelgining' Attack to Evade Detection
https://thehackernews.com/2018/05/synack-process-doppelganging.html
(PDF file)Process DoppelgatingIs "Process Hollowing(Process Hallowing)It is a code injection tool similar to "Hacking technology which malicious code forcibly stops process and inject alternative code. Process Hollowing makes legitimate and very common processes such as "explorer.exe" of Windows hidden behind malicious code, but instructions of executable files are written directly to memory, so it is possible to detect by using security software . On the other hand, Process Doppelgaging does not write to memory but starts an NTFS transaction on storage and issues instructions to malware and so on. Since transactions are abandoned immediately afterwards, no trace remains, and it is very difficult to detect by security software.
Kaspersky Lab researchers have discovered malware (transomware) using Process Doppelgining technology. This malware is a variant of "SynAck" and it is targeting America, Kuwait, Germany, Iran. The malware itself was discovered in September 2017, but it seems that measures to obfuscate the code were applied to prevent reverse engineering. Correspondence between hash value and API function that Kaspersky Lab has located is as follows.
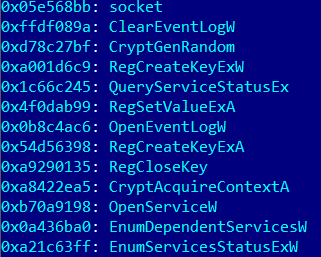
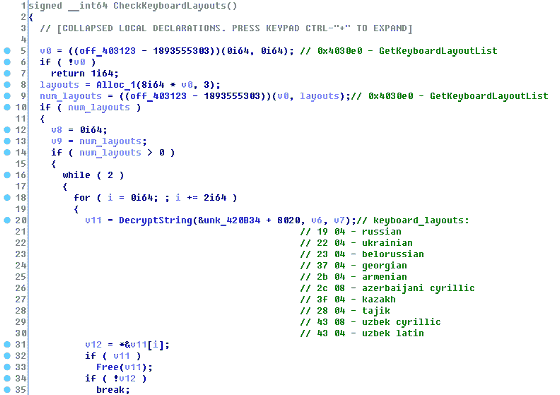
In order to identify the user's country, SynAck first checks the keyboard layout installed in the PC against the list in malware. After confirming the match with the list, it goes to the sleep state for 300 seconds and calls ExitProcess to stop file encryption. It has also been confirmed that SynAck was set not to be infected by users of Russia, Belarus, Ukraine, Georgia, Tajikistan, Kazakhstan, Uzbekistan.
When infected, SynAck uses the AES - 256 - ECB algorithm to encrypt the file and demonstrates the principle as a so - called ran - gam wear that delivers the decryption key by following the attacker's request.
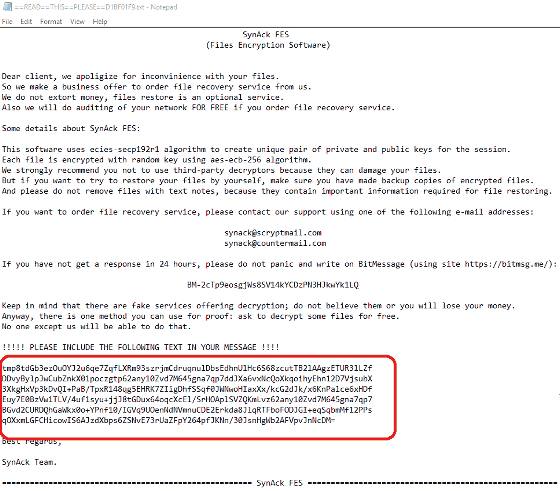
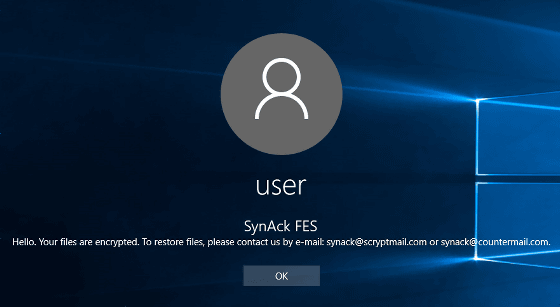
Also, SynAck can add arbitrary text to Windows login screen by changing LegalNoticeCaption and LegalNoticeText in the registry. You can also let the user know that it was attacked at PC startup.
Although Kaspersky Lab does not disclose the infection route of how SynAck adopted by Process Doppelgangling is spreading, most malware goes through phishing mail, a malicious advertisement banner on the web, a third party application, etc. , We need to do these work more carefully. Process Doppelganging Adoption Because it is difficult to detect malware by security counter software, it seems that the current situation is that only important correspondence such as attaching the habit of regularly backing up important files to the outside can be taken.
Related Posts:







