Ransomware targeting Mac users ``Evil Quest'' is discovered, the violence that does not miss the target even after payment of ransom

A new malware ' EvilQuest ' was discovered on June 30, 2020, targeting Macs with macOS installed. This malware called 'Evil Quest' not only has the function of
New Mac ransomware spreading through piracy-Malwarebytes Labs | Malwarebytes Labs
https://blog.malwarebytes.com/mac/2020/06/new-mac-ransomware-spreading-through-piracy/
Objective-See's Blog
https://objective-see.com/blog/blog_0x59.html
New EvilQuest ransomware discovered targeting macOS users | ZDNet
https://www.zdnet.com/article/new-evilquest-ransomware-discovered-targeting-macos-users/
'Evil Quest' was first identified by security researcher Dinesh Devadoss. He posted on Twitter on June 30, 2020, 'I discovered ransomware targeting macOS that has been spoofed as a software update program for Google Chrome that has never been detected', targeting macOS Reported the discovery of ransomware.
#macOS #ransomware impersonating as Google Software Update program with zero detection.
— Dinesh_Devadoss (@dineshdina04) June 29, 2020
MD5:
522962021E383C44AFBD0BC788CF6DA3 6D1A07F57DA74F474B050228C6422790 98638D7CD7FE750B6EAB5B46FF102ABD @philofishal @patrickwardle @thomasareed pic.twitter.com/r5tkmfzmFT
Following a report from Devadoss, Thomas Reed of security firm Malwarebytes conducted an EvilQuest survey. 'We found that EvilQuest was included in the pirated installer of the network monitoring software ' Little Snitch ' for macOS,' Reid reports in the Malwarebytes official blog.
In addition, Evil Quest was found to be included in the pirated version of the music production software for DJ ' Mixed In Key ' by Patrick Woldle of Objective-See, a security company specializing in macOS.
Wardle also said, 'keyloggers function' in EvilQuest from the results of the analysis of the code of EvilQuest and, to establish a communication to the attacker from the victim reverse shell 'through the cryptographic currency function steal data related to' also features I found out that.
From this, the US IT news site ZDNet says, 'Even if the victim pays the ransom, the attacker can access the victim's PC and continue to steal files and inputs to the PC.' I said.
According to Reed, EvilQuest, which slipped into the pirated Little Snitch installer, has the ability to install the malware itself, but the process of installing the pirated Little Snitch does not work properly, and the installer stops halfway.
Also, Chrome's update program, which was the origin of the discovery of EvilQuest, has a function to detect that the file has been changed and replace it with a normal file, so it was not possible to confirm infection via Chrome either. ..
Mr. Reed set the time of the Mac intentionally infected with EvilQuest three days after the infection, the file in the terminal was encrypted, and a message requesting a ransom of 50 dollars (about 5300 yen) was displayed. It was It is speculated that the reason why encryption starts 3 days after infection is because of the intention to hide the infection route.
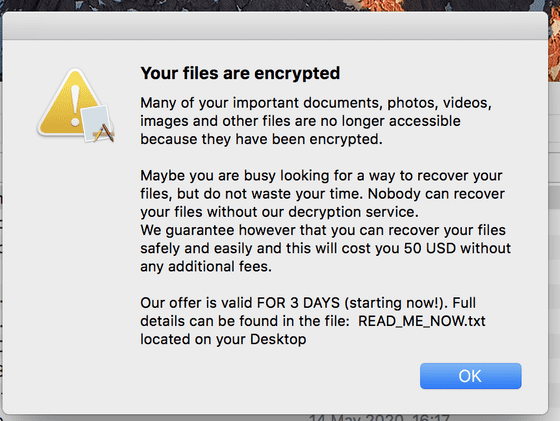
by Malwarebytes Labs
``If you get this malware, you need to remove it from your Mac as soon as possible, and the best way to avoid the effects of ransomware is to have a backup,'' said Reed. Make sure you have two backups of your most important data, one of which should never be left connected to your Mac. With proper backup, ransomware is not a threat.'
As Devadoss pointed out, as of June 30, antivirus software that can detect EvilQuest even if you search with VirusTotal, a service that can detect malware using more than 60 major antivirus engines. There was no On the other hand, it is possible to detect with
Malwarebytes for Mac — Mac Antivirus Replacement | Malwarebytes
https://www.malwarebytes.com/mac/
Related Posts: