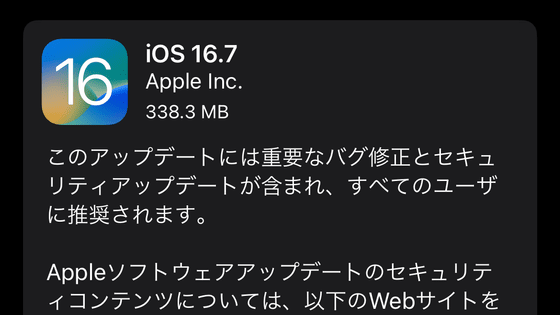
A zero-day exploit chain that actually attacks iPhone is discovered, you need to update as soon as possible
Google's
0-days exploited by commercial surveillance vendor in Egypt
https://blog.google/threat-analysis-group/0-days-exploited-by-commercial-surveillance-vendor-in-egypt/
PREDATOR IN THE WIRES: Ahmed Eltantawy Targeted with Predator Spyware After Announcing Presidential Ambitions - The Citizen Lab
https://citizenlab.ca/2023/09/predator-in-the-wires-ahmed-eltantawy-targeted-with-predator-spyware-after-announcing-presidential-ambitions/
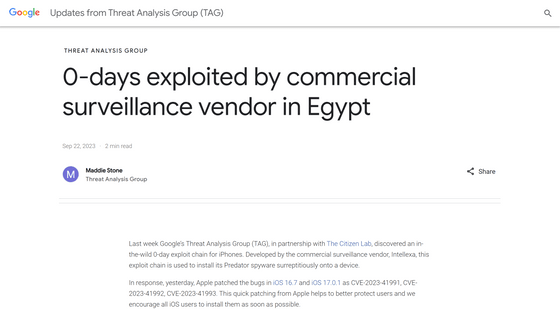
The exploit discovered this time installs the spyware ``Predator'' developed by Intellexa (formerly Cytrox) on iOS devices. This was discovered when former Egyptian parliamentarian Ahmed El-Tantawi had doubts about the safety of his smartphone and asked The Citizen Lab to investigate. The exploit was carried out after El-Tantawy publicly announced his plans to run for president in the 2024 Egyptian elections, and Intellexa's past business dealings with the Egyptian government suggest that Intellexa may be under threat from the Egyptian government. It is believed that this was carried out upon receiving a request.
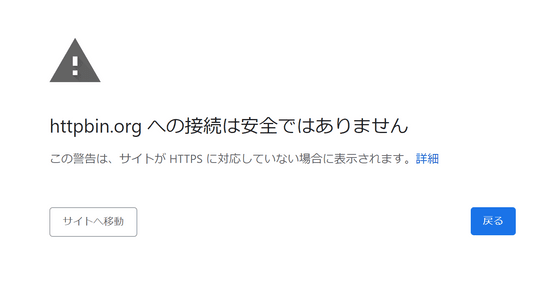
This attack used a man-in-the-middle attack (MITM), in which the attacker enters between the target and the website. If the target is trying to access a website using 'http', the attacker can intercept the traffic and replace it with fake data. On the other hand, when you access a website using 'http s ', your traffic is encrypted and cannot be viewed by prying eyes, and a server certificate is used to ensure that the data received is from a legitimate server. can be verified.
In Mr. Eltantawy's case, accessing any 'http' site would redirect him to Intellexa's site. Afterwards, it was confirmed that a small binary was executed without user interaction using an exploit chain that combined the following three vulnerabilities.
・CVE-2023-41993: Initial remote code execution (RCE) in Safari
・CVE-2023-41991: PAC bypass
・CVE-2023-41992: Local privilege escalation (LPE) in XNU kernel
Detailed information is expected to be released in due course in accordance with Google's vulnerability disclosure policy .
In addition, as a countermeasure against MITM attacks, Google Chrome is equipped with ' HTTPS first mode ' which attempts to communicate using https even if http is specified in the URL. They appear to notify users that they are less secure.
Related Posts:
in Security, Posted by log1d_ts







