High-performance spyware that continues to hide in PC from 2008 "Regin"

ByAlan
"Regin" is a high-performance malware used for international spy activities since 2008. It was used for investigating secretly the government, infrastructure companies, private enterprises, research institutes and individuals and was able to finely customize the capabilities according to the target, so it had a great effect on collective monitoring of groups etc. around the world It turned out in the investigation of Symantec.
Regin: Top-tier espionage tool allowed stealthy surveillance | Symantec Connect
http://www.symantec.com/connect/blogs/regin-top-tier-espionage-tool-enables-stealthy-surveillance
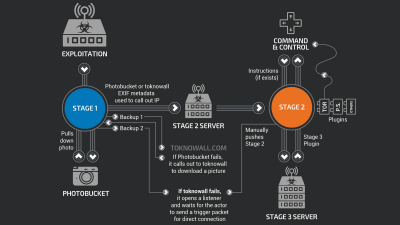
"Regin", a high-performance backdoor-type Trojan horse malware, has been confirmed to be active in international spy campaign since 2008. According to Symantec's research report, "Backdoor.Regin" adopts "multi-stage structure" with five stages, and the four stages except the initial stage are encrypted while being concealed . The first stage has the role of loading a total of five stages, but each stage does not have complete package information, and in order to analyze Regin it is necessary to obtain all 5 stages.
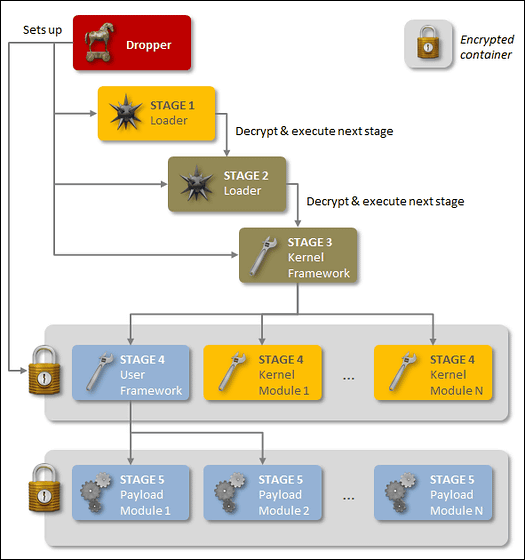
In addition, Regin has the feature of enabling custom loading suitable for the target by "modular approach". The modular approach is "Flamer"Or"Weevil (The Mask)It is also used for sophisticated malware similar to "multiple stage loading configuration"Duqu"StuxnetIt is a characteristic confirmed with malware of kind.
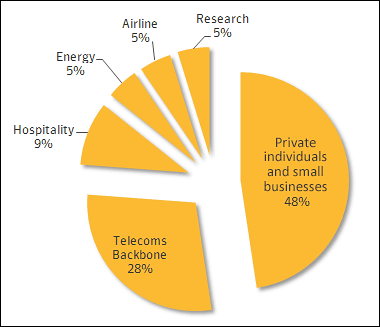
The following is a graph showing the infection rate of Regin for each sector. Although target is widely set, 48% is for individuals and small and medium enterprises, 28% for spy acts, 9% for hospitality business, 5% for energy industry / aviation enterprises / research organizations, It has become a breakdown. Regin infection was confirmed between 2008 and 2011, but the new version of Regin has been rediscovered after 2013.
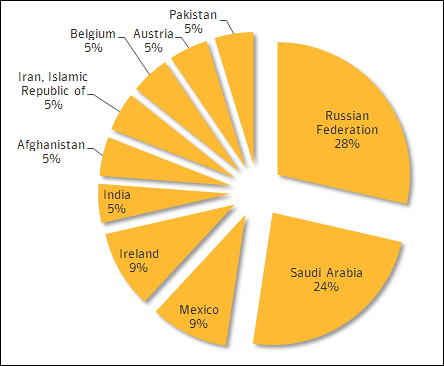
Looking at the infection rate of Regin by country, Russia is 28%, Saudi Arabia 24%, Mexico / Ireland 9%, India / Afghanistan / Iran / Belgium / Austria / Pakistan each 5%. Although the infection route varies depending on the target, it has been found from the log file of one PC that Regin was installed through Yahoo! Instant Messenger. Symantec says that Regin is likely to be installed from web browsers and applications.
Regin has multiple remote access functions, and when actually infected it saves "screenshot" "point and click control of mouse" "get password" "monitor network traffic" "deleted file Restore "and so on. Microsoft'sIIS web serverMore complicated and sophisticated modules such as traffic monitoring of the network and the mobile phone base station control function of the administrative agency by the LAN analyzer have been discovered.
While being used for international spy campaign for several years, Regin, which had hardly been confirmed, is an advanced malware that is hard to detect even. Symantec forecasts that it is suggesting that national-level organizations are involved in order to realize these 'stealth functions' because of the large amount of investment, time and resources required. In the future Symantec will explore unidentified versions of Regin and undiscovered additional features.
Related Posts:
in Software, Posted by darkhorse_log