Malware "Kwampirs" to spy company through healthcare equipment appears

byAsh Edmonds
Symantec of security software development is a hacking group that conducts corporate spies targeting medical institutions and related departments around the worldOrangeworm"The existence of" Orangeworm is a software hosting machine used for controlling high-tech medical devices used for X-rays, MRI, etc., and a machine used for creating a consent form of a patient, by infecting malware, a company It is said that they are doing spies.
New Orangeworm attack group targets the healthcare sector in the U.S., Europe, and Asia | Symantec Blogs
https://www.symantec.com/blogs/threat-intelligence/orangeworm-targets-healthcare-us-europe-asia

Hackers Behind Healthcare Espionage Infect X-Ray and MRI Machines
https://thehackernews.com/2018/04/healthcare-cyber-attacks.html
According to a report released by Symantec, Orangeworm has been conducting spy activities for companies since the early 2015, hacking targeting international companies' companies based in the US, Europe and Asia, mainly in medical institutions It is said that.
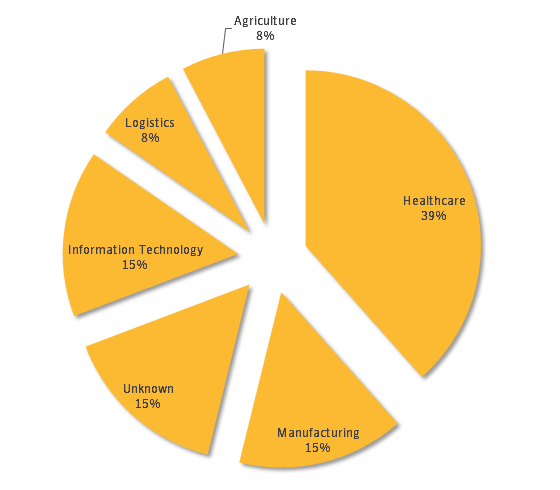
The industries of companies targeted by Orangeworm as hacking are as follows. Approximately 40% are related to healthcare, followed by manufacturing / IT related / unknown industries at 15% of the same rate.
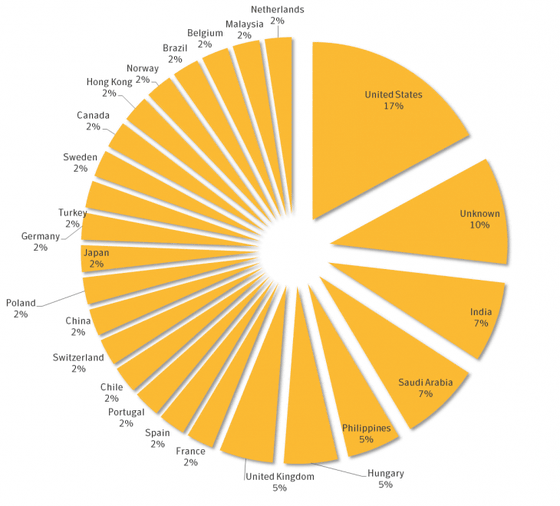
The headquarters of the targeted companies are as follows. The most common are 17% of American companies, followed by nationality unknown (10%), India / Saudi Arabia (7%), Philippines / Hungary / UK (5%).
Orangeworm will install a Trojan horse called "Kwampirs" which allows you to steal confidential data by remotely accessing the terminal at any time by establishing a backdoor after entering the network via the target machine. Analysis of Kwampirs reveals that randomly generated character strings are inserted into the main DLL payload to avoid hash-based detection. In addition, Kwampirs creates a service with the following settings so that the service can be restarted immediately even if the intruding system restarts.
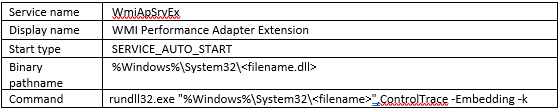
Also, Kwampirs gathers some basic information about the compromised computer and sends a remote command control server for the hacker, thereby grouping what kind of user the hacked system is used It is supposed to be able to do. Specifically, it is highly likely that "whether the system is being used by researchers" or "whether the system user is a target with high hacking value" is high.
And Kwampirs had the property of duplicating itself and diffusing it to other systemswormHowever, infected systems proactively spread their own alter ego on the network to which they are connected. And in the same way it will try to create multiple 'infected computers' with Kwampirs.
Kwampirs collects information using system built-in commands, not using third-party reconnaissance tools and the like. On the system actually infected with Kwampirs, the following command seems to be executed secretly.
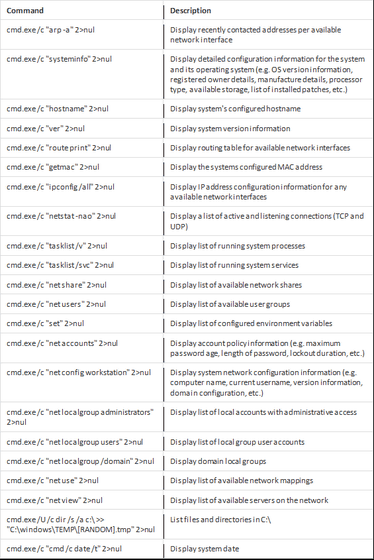
The command above states that Orangeworm says "(computers infected by Kwampirs) recently accessed, information on the network adapter you are using, as well as available network shares, mapped drives, compromised computers Information on files to be sent "and so on.
Furthermore, Symantec stated, "The exact motivation of Orangeworm is not known and there is no information useful to identify the origin of the organization, but Orangeworm is likely to conduct spy activities for commercial purposes."
Related Posts: