Malware “ComRAT v4” that steals confidential documents using Gmail
ESET, a cybersecurity company, has released a report on the latest version of the malware 'ComRAT' that has been used by hacker group '
From Agent.BTZ to ComRAT v4: A ten‑year journey | WeLiveSecurity
https://www.welivesecurity.com/2020/05/26/agentbtz-comratv4-ten-year-journey/
New ComRAT Malware Uses Gmail to Receive Commands and Exfiltrate Data
https://thehackernews.com/2020/05/gmail-malware-hacker.html
Turla, also known as 'Snake' or 'Uroburos', is a hacker group known for invading US military networks in the mid-1990s. In 2008, when it invaded the U.S. Central Forces' network, it caused enormous damage, which was described as 'the largest network invasion that the U.S. military has ever experienced.' At this time, the Trojan horse malware used by Turla is 'ComRAT'.
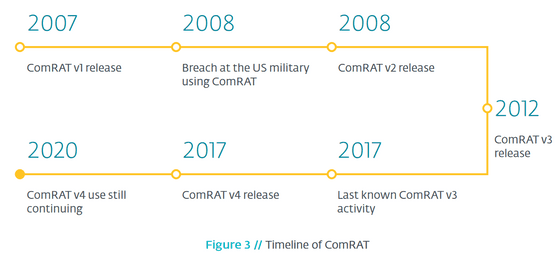
Since successfully attacking the U.S. Central Army in the midst of the Iraq war, Turla has updated ComRAT multiple times to expand its capabilities. Among them, “ComRAT v4”, which was first confirmed in 2017, is an old code that has been used until then, and has a complicated structure that sets it apart from the previous code.
According to ESET, 'ComRAT v4' has successfully attacked at least three public authorities. Two of the three are the Ministry of Foreign Affairs of countries in Eastern Europe, and the other is the Caucasus State Parliament. However, in order to prevent the spread of damage, specific country names, organization names, details of leaked files, etc. were not disclosed.
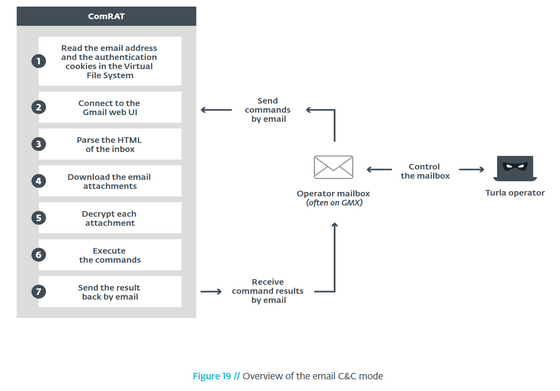
The most notable feature of 'ComRAT v4' is that it has acquired a new attack vector using Gmail. The attack route of 'ComRAT v4' was confirmed not only via the conventional
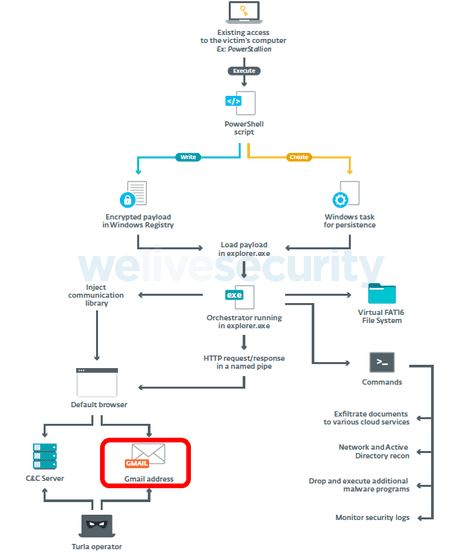
On the other hand, ESET has succeeded in approaching Turla's identity through the analysis of 'ComRAT v4'. Turla's operators say they are logging regularly via email to see if 'ComRAT v4' is being detected by security software. Therefore, by calculating the time when the email was sent and received by Gmail, the time when the operator executed the command to get the 'ComRAT v4' log can be estimated.
The result of ESET actually extracting the Gmail time stamp is as follows. Sending and receiving mail was concentrated in the daytime in the
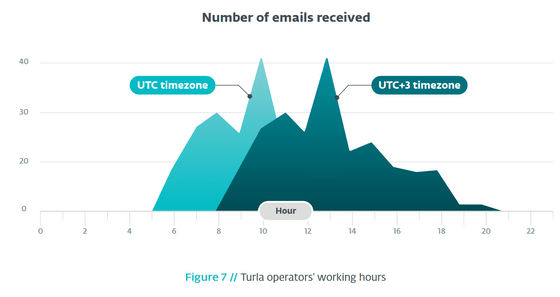
For this reason, ESET believes Turla is likely to be based in regions that are in UTC + 3 or UTC + 4 time zones. It has been said for a long time that Turla has a close relationship with Russia, but the damage of 'ComRAT v4' specified this time is concentrated in the area close to Russia, and Turla is active in Moscow etc. This allegation became more intense as it overlapped with the included time zones.
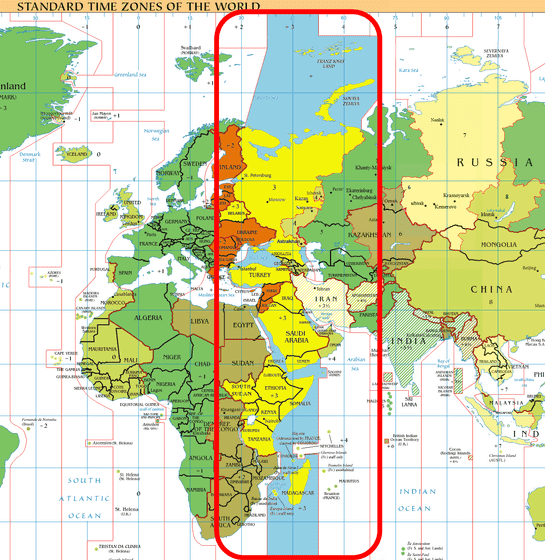
by Wikimedia Commons
In a report, ESET malware researcher Matthieu Faou said, 'The most interesting feature of ComRAT v4 is that it uses Gmail's web user interface to receive commands and leak data. It is possible to bypass some security controls by allowing malicious domain-independent attacks, and we have discovered that ComRAT v4 was also used in January 2020. , Which means that Turla remains a major threat to diplomats and the military. ”
Related Posts:
in Web Service, Security, Posted by log1l_ks