UEFI rootkit 'Cosmic Strand' that remains infected even if the OS is reinstalled or the storage is replaced, damages ASUS and GIGABYTE motherboards

Since 2016, Chinese hackers have been using malware that is not detected on the firmware image of some motherboards. This malware is expressed as 'UEFI rootkit' by combining
CosmicStrand rootkit hides in the UEFI firmware | Kaspersky official blog
https://www.kaspersky.com/blog/cosmicstrand-uefi-rootkit/45017/
CosmicStrand UEFI malware found in Gigabyte, ASUS motherboards
https://www.bleepingcomputer.com/news/security/cosmicstrand-uefi-malware-found-in-gigabyte-asus-motherboards/
Discovery of new UEFI rootkit exposes an ugly truth: The attacks are invisible to us | Ars Technica
https://arstechnica.com/information-technology/2022/07/researchers-unpack-unkillable-uefi-rootkit-that-survives-os-reinstalls/
CosmicStrand: the discovery of a sophisticated UEFI firmware rootkit | Securelist
https://securelist.com/cosmicstrand-uefi-firmware-rootkit/106973/
CosmicStrand Malware Infects ASUS, Gigabyte Motherboards | Tom's Hardware
https://www.tomshardware.com/news/cosmicstrand-malware-asus-gigabyte
Kaspersky Researchers Dissect Bootup Rootkit --InfoRiskToday
https://www.inforisktoday.com/kaspersky-researchers-dissect-bootup-rootkit-a-19645
According to cybersecurity firm Kaspersky, the early Cosmic Strand was first introduced in 2017 and was named ' Spy Shadow Trojan ' by Qihoo 360 analysts who develop antivirus software.
It's unclear how an attacker infiltrated the UEFI rootkit into the firmware image of the device being attacked, but researchers said they discovered the Cosmic Strand on devices with ASUS and GIGABYTE motherboards. I am reporting.

UEFI is software that connects the OS of a computer to the firmware on the hardware. UEFI resides in an SPI-connected flash storage chip that is soldered to the computer's motherboard, making code inspection and patching difficult. UEFI code also affects the operating system, security software, and other software because it runs before the operating system and other available security solutions in the computer's boot sequence.
Not only is it difficult to identify malware loaded in UEFI, but it is also characterized by the fact that it cannot be removed by reinstalling the OS or replacing the storage drive. This means that UEFI rootkits can permanently affect your PC as long as you are using the same motherboard.
To elaborate on how CosmicStrand works, the first infected firmware
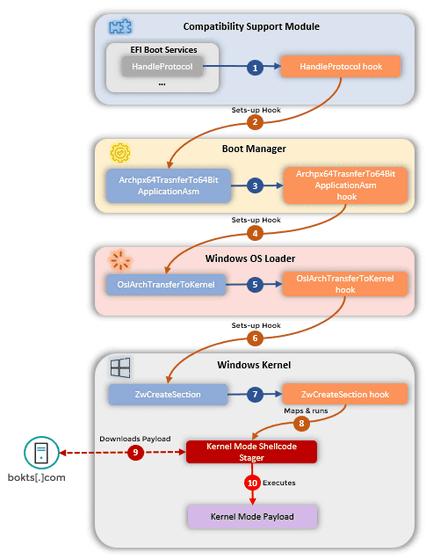
Kaspersky researcher Ivan Kwiatkowski commented on the peculiarities of Cosmic Strand: 'Whether the rootkit is installed on the victim's device depends on whether it is a bootkit or not. Even if it is infected with the component used for booting, it may or may not be a rootkit. Firmware is one of the components that can infect a bootkit, but there are other possibilities as well. On the other hand, Cosmic Strand does all this at the same time, so it can infect the boot process by applying a malicious patch to the firmware image of the motherboard while still having the features of a stealth rootkit. ' increase.
Mark Lechtik, a former Kaspersky reverse engineer who was involved in the investigation and now a Mandiant member, explained that the firmware image had a modified CSMCORE DXE driver that enabled the legacy boot process. .. 'This driver has been modified to intercept the boot sequence and introduce malicious logic,' Lechtik
Qihoo 360 analysts analyzed Spy Shadow Trojan after receiving reports from malware victims that 'my computer suddenly created a new account and antivirus software continued to warn of malware infections.' have started. Analysts reported that the system compromised by the Spy Shadow Trojan was running on a 'used ASUS motherboard' that the user purchased from an online store.
Meanwhile, Kaspersky reports that 'Cosmic Strand is included in the firmware image of GIGABYTE and ASUS motherboards with the H81 chipset.' The H81 chipset was released in 2013 and was mainly used in 2013-2015.
To install Cosmic Strand on the motherboard firmware, you need to use either 'Physical access to the motherboard' or 'Precursor malware that can automatically patch the firmware'. It is unknown by what means the attacker used to infiltrate the Cosmic Strand into the motherboard.
According to Kaspersky, Cosmic Strand has been shown to target individuals in China, Iran, Vietnam and Russia. However, at the time of writing, few other clues to attackers using Cosmic Strand have been revealed.
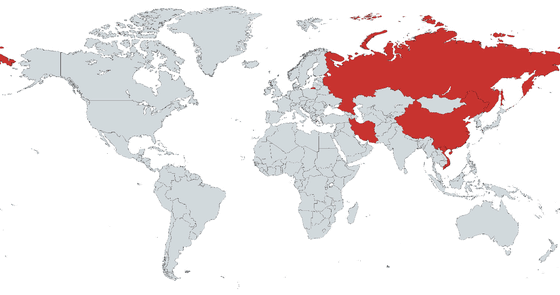
However, Cosmic Strand also has similarities to the code patterns found on crypto botnets called 'My Kings' where Sophos malware analysts discovered Chinese artifacts, so some attackers use Cosmic Strand. It is presumed to be a Chinese-speaking hacker. According to Kaspersky, Cosmic Strand has evidence of years of operation since late 2016.
Related Posts:
in Security, Posted by logu_ii