What is "Lakshasa" that infects BIOS and firmware and creates backdoor that can not be detected by hardware?

BySemino 1e
British researchers in MayDiscovered an unknown backdoor capable of cyber attack on Chinese-made silicon chip used for nuclear power plants and militaryThere was an article saying that,Black Hat security conferenceHe is the CEO at Toucan System and is also a security consultantJonathan BrorosadeActually demonstrated the behavior of the hardware backdoor.
HARDWARE BACKDOORING IS PRACTICAL
http://www.blackhat.com/usa/bh-us-12-briefings.html#Brossard
[Defcon] Hardware backdooring is practical
http://www.slideshare.net/endrazine/defcon-hardware-backdooring-is-practical
First of all, the perfect back door has the following characteristics. "Persistent", "Hard to be sensed" (Do not place hostile code on the computer) "Can be carried (independent from the OS)" "Remote access, Remote update possible" "Maintain normal state "" You can cross the network (Firewall, Authentication proxy, etc) "" Redundancy "" Not sensed (needless to say) ".

So let's see what features Rakshasa has. "Rakshasa" consists of four core components, "Coreboot", "SeaBios", "iPXE", and "payloads" as a core component, and portability is important, not belonging to anywhere · It is as cheap as possible and quick development (completed in about 4 weeks), and it is really difficult to detect with real seriousness. At the moment it is possible to infect 230 types of motherboard, booting by BIOS rewriting (possible by treating Coreboot and PCI ROM as iPXE) and rewriting via infection · network or PCI device (there is redundancy) Activation and infection · It is also possible to activate and infect by payload over the network. However, since this boot kit is cleverly made from legitimate open source tools, it is hard to be recognized from various systems that detect malicious software. Furthermore, every time it is activated, it is expanded in memory newly, so even if you disinfect it, it will restore.
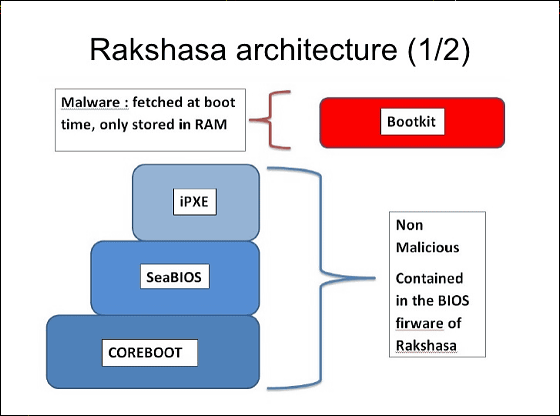
At boot time, this boot kit is started via HTTPS via the Internet and can be started via wireless LAN, WiMAX, or local network if possible.
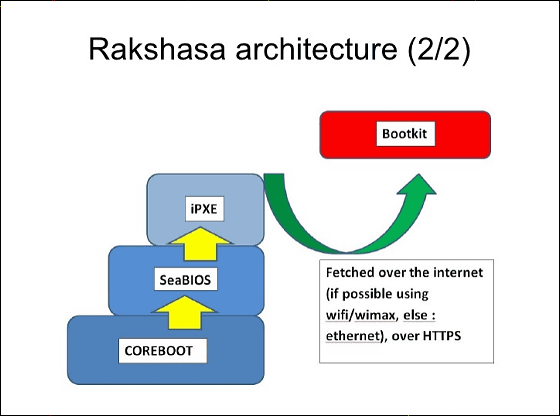
After that, "Rakshasa"NX bit, Making it impossible for CPU to update by microcode, and antiSMMInvalidate protection function,ASLRIt is to start activities such as disabling. Besides being excellent in stealth performance, it lets you start up via remote without leaving any evidence in the file system, it can start up even via wireless LAN or WiMAX, but if you need a fake BIOS menu as well It can even display and even fill in the CMOS image.
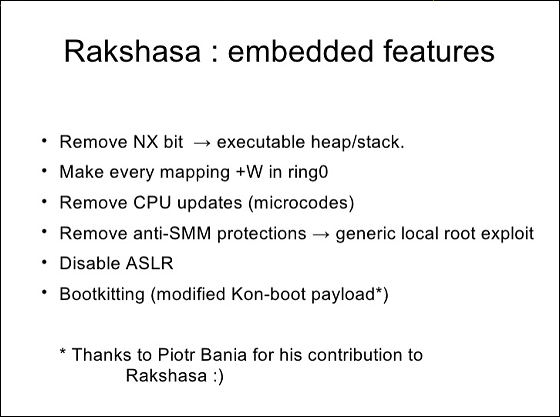
By the above action, "Rakshasa" is "Permanently lower security level regardless of OS"It makes it to the security level of 1997"Continuity that it keeps remaining even if hard disk and OS are removedIt is now possible to realize.

Anyone who can physically contact hardware can install "Rakshasa" on the hardware. For example, it can be installed at the time of manufacturing or installed via USB, and these operations can be executed within just 3 minutes. Also, it is possible to sell the hardware that had previously stocked such backdoor in the net auction, and if such parts are used in the data center it is the end of one volume.
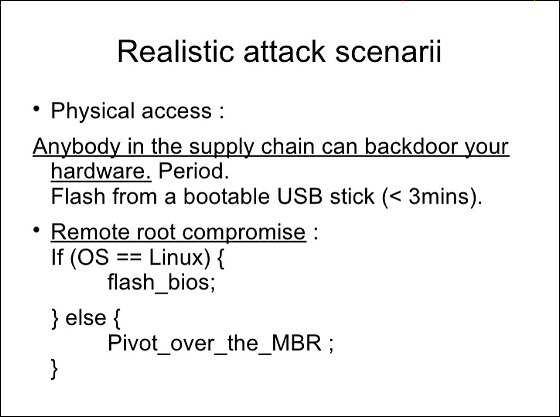
Considering that almost all electronic devices are manufactured in China, it is easy to hold backdoors on all kinds of hardware such as computers, if we hold down China, the dangers are inevitable.
Jonathan Brorosad says that by widely notifying the dangers of "Rakshasa" this will lead to better analysis of technology and invasion.
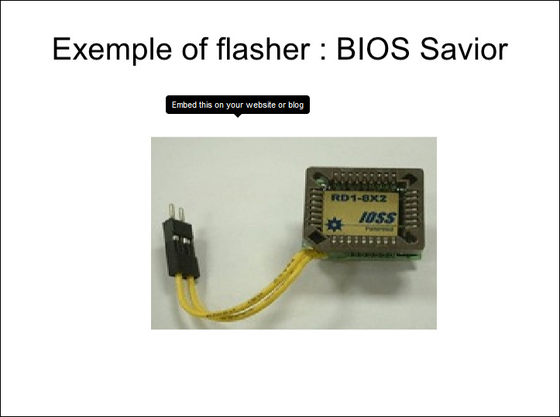
In addition, as a defense method, I ceased to trust unconditionally as "BIOS is safe", I also disapprove BIOS update via OS and BIOS update on floppy / CD-ROM, etc., only for physical BIOS update A kit, for example "BIOS SaviorIt is good to update the firmware of all the motherboards that are using at the same time.
Related Posts:
in Note, Posted by darkhorse_log