"Thunderstrike 2" which infection spreads through Thunderbolt accessory of Mac and it is difficult to detect / remove

At the end of 2014, on MacBookVulnerability that makes it impossible to detect / delete infected boot kits (malware) via ThunderboltI found. This vulnerability should have been resolved by Apple's patch distribution in January 2015, but it is a vulnerability discoveryTrammel · HudsonMr. said that there is still danger remaining in the new boot kit "Thunderstrike 2"I demonstrate by demonstration.
Procedures for actually infecting Thunderstrike 2 on MacBook are published on YouTube.
Thunderstrike 2 "firmworm" for MacBooks Preview Video - YouTube
Download "Download a cute cat screensaver"
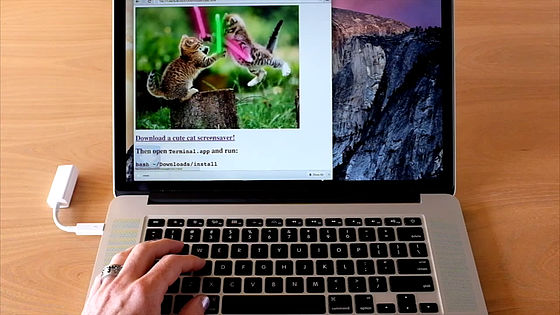
Then, by executing remote code, root (administrator authority) was acquired.
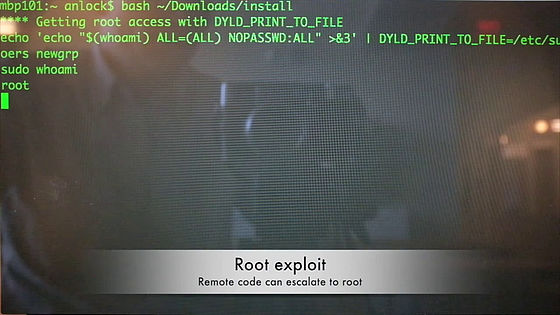
Unlock BIOS ......

Is there a removable disk?PCIe busThen,Option ROMWill write to.
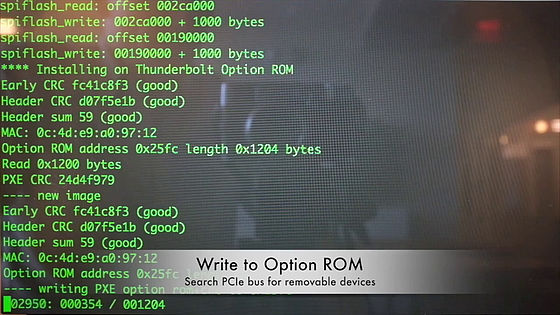
The accessories that were connected to the Thunderbolt port now infected "Thunderstrike 2".

After rebooting, "Thunderstrike 2" will work on MacBook as well.

The character of "Thunderstrike 2" that appeared before the kernel was loaded.

Next, a MacBook not infected with Thunderstrike 2 appeared. However, the Thunderbolt port has an infected adapter ......

Launch MacBook.

The option ROM is loaded before the kernel. At this time, it seems to hook the script for sleeping and shift to the sleep state when started.

Once started, go to sleep mode immediately.

When entering sleep mode, the system stops supplying power to anything other than memory.

You can see that the fan stopped and the power supply to the CPU ceased.

And the system restarted.

At this time,Boot flashInfected with Thunderstrike 2. Once infected with bootflash, it is impossible to remove even if reinstalling OS or exchanging HDD / SSD.

Next time you start MacBook ......

Thunderstrike 2 is called from the bootflash. With this, MacBook, which had not been infected to anything so far, was infected with Thunderstrike 2.

Insert a clean Thunderbolt adapter into this MacBook.

Thunderstrike 2 will be written to option ROM.

In the meantime the adapter was also infected.

The figure showing this flow looks something like this. Thunderstrike 2 has infiltrated MacBook with malicious software, first infected with MacBook's bootflash. After that, Thunderstrike 2 is written in option ROM of the accessory every time inserting something accessory to Thunderbolt port, infection spreading. When the accessory is inserted in Thunderbolt port of other MacBook etc, S3 resume mode and SMM (System management mode) To spread further infection by hacking ... cycle.

It was in December 2014 that Trammel Hudson found a vulnerability on the Mac and demonstrated the boot kit "Thunderstrike". As a vulnerability of EFI firmware, Dell, Hewlett-Packard, Lenovo, Samsung, and other manufacturers found a total of six vulnerabilities, five of which were also applicable to Macs. Apple created and distributed a patch that addresses the vulnerability, but only one was completely blocked, the other was partial response, the remaining three vulnerabilities were not resolved .
Boot kit for Mac "Thunderstrike": Things to Know | Kaspersky Daily - Official Kaspersky Blog
https://blog.kaspersky.co.jp/thunderstrike-mac-osx-bootkit/6623/
As a boot kit to exploit this unresolved vulnerability, Mr. HudsonXeno KovahWith Mr.Corey Kallenberg"Thunderstrike 2" produced under the cooperation of Mr. Kim.
Thunderstrike 2 - Trammell Hudson's Projects
https://trmm.net/Thunderstrike_2
In the case of "Thunderstrike", it was necessary to access the hardware directly, but "Thunderstrike 2" does not necessarily need direct access as the first infection like the above-mentioned movie, so the risk degree is raised I can say
It is difficult to detect / delete the boot kit with anti-virus software or virus scanner. Firmware analysis is required for users to detect and it is assumed that they have some skill. Researchers offer several optional ROM checkers that you can use for free, but for the first time Forbes suggests that users will need to learn the basics of chip-level security.
By the way, Mr. Kovah points out that "There are parts that Apple does not really take precautions."
Thunderstrike 2: Remote Attacks Can Now Install Super Stealth 'Firmworm' Backdoors On Apple Macs - Forbes
http://www.forbes.com/sites/thomasbrewster/2015/08/03/apple-mac-firmworms/
For details of these, Mr. HudsonBlack Hat USA 2015,andDEF CON 23It is supposed to make a presentation at.
· 2015/08/12 12:05 Addendum
The contents of presentation at DEF CON 23 and Black Hat USA 2015 was released with a slide. Among them, Mr. Hudson got a hint from Windows and Linux UEFI security story pointed out by Mr. Rafal Wojtczuk and Corey Kallenberg, "How about if you can adapt on Mac?" "What if you combine with Thunderstrike?" Thunderstrike 2 was revealed by thinking and discovering.
Thunderstrike 2 details - Trammell Hudson's Projects
https://trmm.net/Thunderstrike2_details
Thunderstrike 2 is not a zero-day attack that exploited a new vulnerability, but it was already pointed out on other platforms and a patch was also issued as well, although it is called a zero-day attack after the vulnerability is found until the fix patch is issued It is an attack against "old vulnerability" like that.
The following is a vulnerability referred to as "Snorlax / Price Harming" in June 2015 in the situation of Mac OS X against information disclosed vulnerability from 2013 to 2014 indicated by Hudson. "Darth Venamis" which was discovered in 2014 has been partially modified. However, "SpeedRacer / BIOS_CTNL", "King's Gambit", "The Sicilian" etc. are abandoned.

Related Posts:
in Video, Posted by logc_nt