Malware 'XCSSET' targeting Apple application developers turns out to be exploiting a new vulnerability

Zero-Day TCC bypass discovered in XCSSET malware
https://www.jamf.com/blog/zero-day-tcc-bypass-discovered-in-xcsset-malware/
Actively exploited macOS 0day let hackers take screenshots of infected Macs | Ars Technica
https://arstechnica.com/gadgets/2021/05/hackers-exploit-a-macos-0day-that-allows-them-to-screenshot-infected-macs/
Apple fixes three zero-days, one abused by XCSSET macOS malware
https://www.bleepingcomputer.com/news/security/apple-fixes-three-zero-days-one-abused-by-xcsset-macos-malware/
XCSSET is malware that exploits two types of Xcode zero-day vulnerabilities reported by security company Trend Micro in August 2020. Functions such as reading cookies from a browser such as Safari, stealing information from communication tools such as Skype, taking screenshots of screens, and forcibly uploading specific files to a specified server were confirmed at the time of discovery I did.
Mac malware 'XCSSET' that spreads via Xcode project is now available --GIGAZINE

Regarding this XCSSET, Jamf, known as the management tool 'Jamf Pro ' for Apple devices, reported that 'another zero-day vulnerability is being exploited.' The newly discovered vulnerability is related to 'Transparency Consent and Control (TCC) ' that manages access rights for hard drives, microphones, cameras, etc. TCC is a prompt that appears when you run a program that contains actions that require explicit user permission, such as taking screenshots, recording keystrokes, or saving files to a document directory. , In macOS, the TCC of whether to give permission to the application is displayed on the user side.
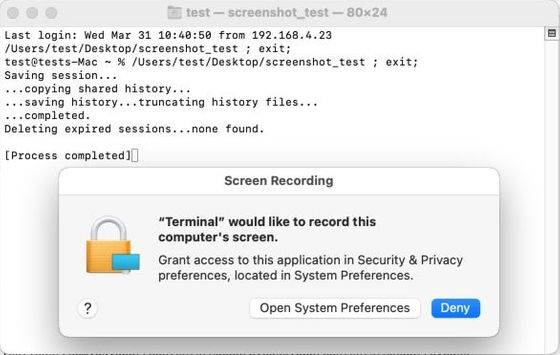
According to Jamf's research, XCSSET was 'piggybacking' on permissions by inserting malicious code into a granted app and hiding it in a directory. This piggybacking confirmed that XCSSET inherited the privileges given to the parent app and took screenshots and so on.
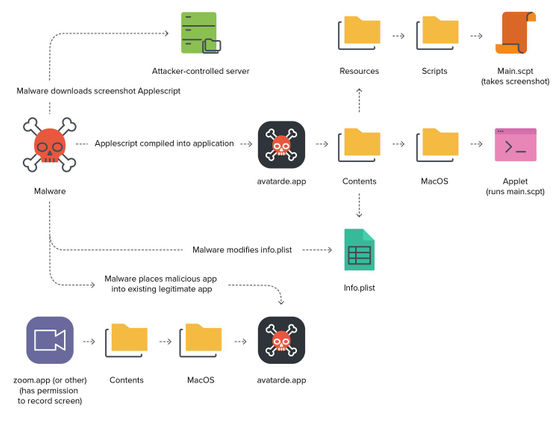
The three zero-day vulnerabilities utilized by XCSSET have been fixed in macOS Big Sur 11.4, released May 24, 2021. Jamf has also been reported waiting for the release of macOS Big Sur 11.4, in which Jamf calls for a quick patch.
Related Posts:
in Security, Posted by darkhorse_log