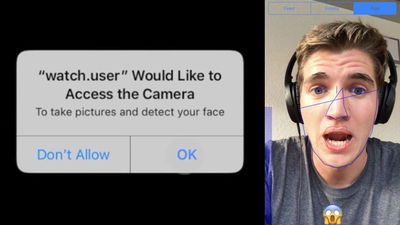
Vulnerabilities in Microsoft apps such as Excel, Outlook, PowerPoint, Teams, Word, and OneNote for macOS could allow unauthorized access to microphones and cameras

How multiple vulnerabilities in Microsoft apps for macOS pave the way to stealing permissions
https://blog.talosintelligence.com/how-multiple-vulnerabilities-in-microsoft-apps-for-macos-pave-the-way-to-stealing-permissions/
Vulnerability in Microsoft apps allowed hackers to spy on Mac users
https://9to5mac.com/2024/08/19/vulnerability-microsoft-apps-mac/
Bug Leaves Microsoft Apps for MacOS Open to Silent Takeovers | PCMag
https://www.pcmag.com/news/bug-leaves-microsoft-apps-for-macos-open-to-silent-takeovers
Flaws in Microsoft apps could let attackers spy on users
https://appleinsider.com/articles/24/08/19/security-flaws-in-microsoft-mac-apps-could-let-attackers-spy-on-users
Cisco Talos conducted an analysis of macOS applications and research into the potential exploitation of the permission-based security model that is central to macOS's user protection feature, the Transparency, Consent and Control (TCC) framework.
TCC is a framework that manages app permissions for accessing location services, camera, microphone, photos in the library, and other files in macOS. Each app must obtain explicit consent under TCC to access these protected resources.
Whether or not a user allows an app to access their camera, microphone, or other resources is recorded in a database, and future requests are managed based on the previous records, allowing users to prevent malicious apps from performing sensitive actions.
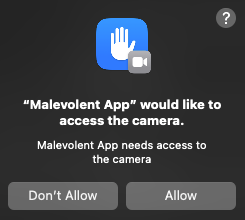
macOS provides a feature called 'Hardened Runtime' that protects the security of apps. Apps that adopt Hardened Runtime must declare the necessary functions as 'entitlements' to perform certain actions within the app. For example, unless you enable the entitlement 'com.apple.security.device.camera', the app will not be allowed to access the camera, and no popup requesting permission will be displayed.
In addition, library validation is enabled by default in Hardened Runtime, and libraries that can be loaded are limited to those signed by the app developer or Apple. However, if library validation is an obstacle to supporting third-party plug-ins, etc., you can avoid library validation by disabling the entitlement 'com.apple.security.cs.disable-library-validation'.
As a result of Cisco Talos' investigation, it was found that library verification of Hardened Runtime is disabled in Microsoft's macOS applications 'Microsoft Word', 'Microsoft Outlook', 'Microsoft Excel', 'Microsoft OneNote', 'Microsoft PowerPoint', and three Microsoft Teams-related applications. Cisco Talos points out that this allows attackers to insert malicious libraries into legitimate applications and abuse the access permissions granted to the apps based on TCC.
The permissions that the hackers can exploit vary depending on the app they compromise, but all apps except Excel can access the microphone to record audio, and those that can access the camera can take photos and videos. All apps except Outlook can also send Apple events to Outlook, which allows them to send emails without the user's prompting.
Cisco Talos said, 'The effectiveness of TCC depends on apps handling the permissions they receive responsibly. If a trusted app is compromised, its permissions could be abused and manipulated to allow an attacker to perform actions without the user's knowledge. For example, a video chat app with access to the camera and microphone could be abused to force recording without warning the user.'

Microsoft says it has disabled library validation in the affected apps because it needs to allow third-party plugins.
Of the eight apps reported by Cisco Talos, the issues were fixed by Microsoft for 'three Microsoft Teams-related apps' and 'Microsoft OneNote,' but 'Microsoft Word,' 'Microsoft Outlook,' 'Microsoft Excel,' and 'Microsoft PowerPoint' remain vulnerable.
Related Posts: