A security company reports that the free password manager 'Bitwarden' has a flaw that can steal passwords by embedding another site

Security company Flashpoint reported that the popular open source password manager ``
Bitwarden: The Curious (Use-)Case of Password Pilfering | Flashpoint
https://flashpoint.io/blog/bitwarden-password-pilfering/
Bitwarden flaw can let hackers steal passwords using iframes
https://www.bleepingcomputer.com/news/security/bitwarden-flaw-can-let-hackers-steal-passwords-using-iframes/
The problem pointed out this time is the function to automatically enter passwords in Bitwarden's browser extension. If Bitwarden determines that the user is on a page that stores IDs and passwords, it will suggest entering the information in the respective fields. Also, if the 'Enable auto-fill when loading page' item in the options is checked, it will be auto-filled without user interaction.
Flashpoint's analysis of Bitwarden found that the feature also autofills embedded forms using iframes. Flashpoint explains that 'a page embedded in an iframe cannot access the content of the parent page, but can wait for login forms to be filled and forward the entered credentials to a remote server.' I'm here.
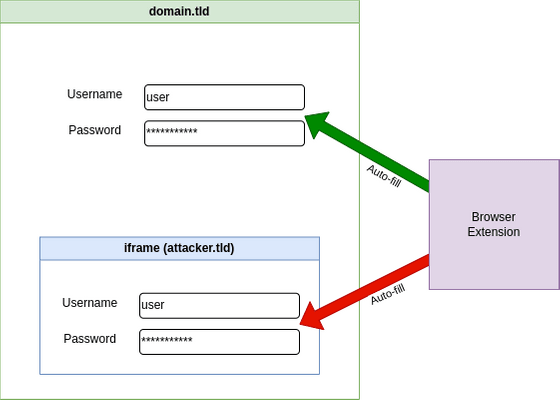
Nonetheless, this action itself does not pose such a great danger. Flashpoint's study of how often iframes are embedded in the login pages of popular high-traffic sites shows that the number of dangerous cases is very low.
However, in Flashpoint's investigation of the iframe problem, it was found that there is another problem that 'Bitwarden autofills credentials even on
A subdomain is another domain under the original domain. For example, a company had a login page called 'https://logins.company.tld' and allowed another client to serve content from 'https://clientname.company.tld'. In that case, the client could place a fake page there to steal the credentials from the Bitwarden extension.
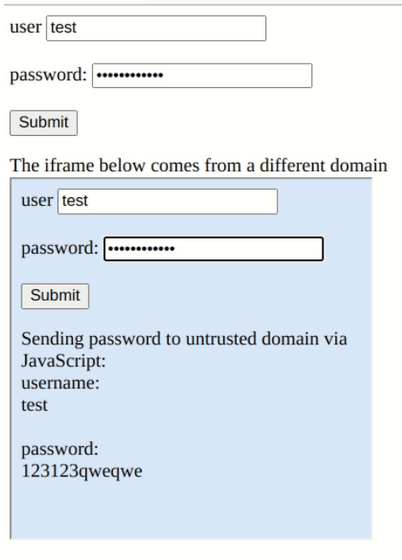
“Some content hosting providers allow third parties to host arbitrary content on subdomains of their official domains and also provide login pages for them,” Flashpoint notes.
In other words, if autofill is enabled and an attacker prepares a page for phishing attacks under the base domain, the victim's ID and password can be stolen simply by visiting that page. It means that there is a danger of falling.
In
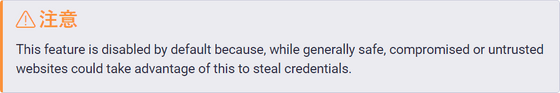
Since this issue was first revealed in a security evaluation in November 2018, Bitwarden has been aware of the risk of iframes being abused since then. However, in response to the demand for logging into services using iframes on external domains, Bitwarden decided to respond by adding warnings to the documentation and extension settings screens rather than changing the behavior.
In response to Flashpoint's re-reporting of the issue, Bitwarden promised to block autofill in hosting environments where the issue was found in a future update, but said it had no plans to change the behavior of iframe functionality.
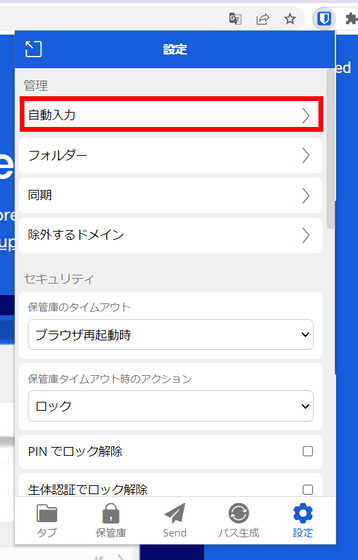
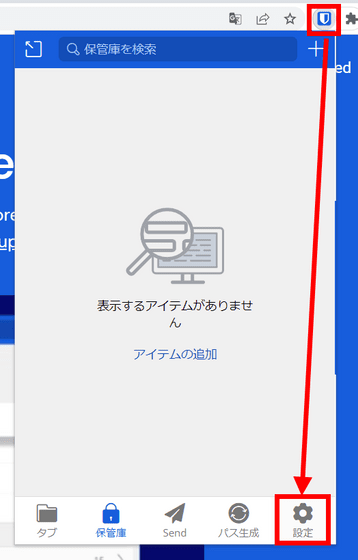
Here's how to check if autofill is enabled in your Bitwarden extension: First, click 'Settings' in the extension menu.
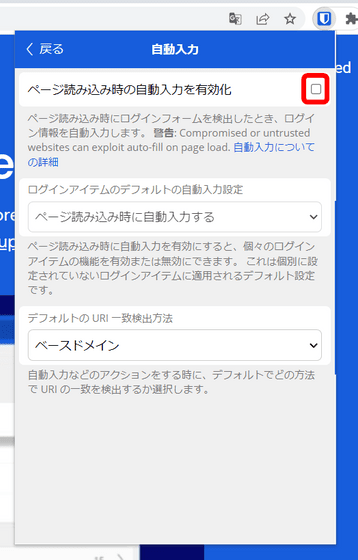
If the check box in the red frame is not checked, autofill is turned off.
Related Posts:
in Security, Web Application, Posted by log1l_ks