It turns out that malware has been distributed via the back door provided in the official 'ASUS Live Update Utility' of ASUS

by
We found that the official software 'ASUS Live Update Utility', which ASUS uses to update the BIOS, UEFI, and software on the PC, was equipped with a backdoor, and that an attack was being conducted that malware was distributed. The Kaspersky Lab has named the attack ' Operation ShadowHammer '.
Malicious updates for ASUS laptops | Kaspersky Lab official blog
https://www.kaspersky.com/blog/shadow-hammer-teaser/26149/
Operation ShadowHammer | Securelist
https://securelist.com/operation-shadowhammer/89992/
Hackers Hijacked ASUS Software Updates to Install Backdoors on Computers of Mothers-Motherboard
https://motherboard.vice.com/en_us/article/pan9wn/hackers-hijacked-asus-software-updates-to-install-backdoors-on-thousands-of-computers
The 'ASUS Live Update Utility' used for the attack is the official software for keeping the drivers and utilities up-to-date with an ASUS PC. The backdoor used by the attacker was not always provided from the beginning but was installed in the guise of updates to the ASUS Live Update Utility. The 'Trojan Horse' update was signed with a legitimate certificate and was hosted on a server used for official updates.
According to the Kaspersky Lab, the problem update is distributed between June and November 2018, with more than 57,000 installed, and is believed to have an impact of 1 million.
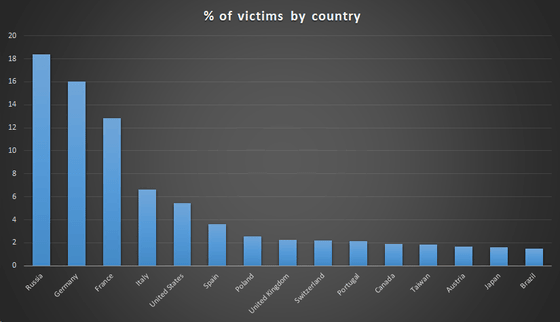
The largest number of victims is Russia. Following are Germany, France, Italy, the United States, and Spain.
'Operation Shadow Hammer' was not aimed at an unspecified number, but was aimed at 600 specific hard-coded MAC addresses. The Kaspersky Lab states that it is comparable to or better than the CCleaner case targeted at large companies in 2017.
Information on the 'Operation Shadow Hammer' will be announced at the Security Conference Kaspersky Security Analyst Summit (SAS) to be held in Singapore on April 8, 2019 (Monday).
Related Posts:
in Software, Posted by logc_nt