A vulnerability 'DNS pooq' that enables DNS hijacking is reported in the DNS transfer software 'Dnsmasq' that is also used by Google and IBM.

Seven vulnerabilities were found in the open source DNS transfer software '
DNSPOOQ --JSOF
https://www.jsof-tech.com/disclosures/dnspooq/
DNSpooq bugs let attackers hijack DNS on millions of devices
https://www.bleepingcomputer.com/news/security/dnspooq-bugs-let-attackers-hijack-dns-on-millions-of-devices/
DNSpooq Flaws Allow DNS Hijacking of Millions of Devices | Threatpost
https://threatpost.com/dnspooq-flaws-allow-dns-hijacking-of-millions-of-devices/163163/
JSOF, an Israeli-based security consultant, published seven vulnerabilities in Dnsmasq on January 19, 2021. These seven vulnerabilities are collectively referred to as ' DNSpooq '.
Dnsmasq is software used by many manufacturers for a variety of purposes. The manufacturers of Dnsmasq confirmed by JSOF in the survey include many large companies such as ASUS, AT & T, Cisco, DELL, General Electric, Google, Huawei, and IBM, and the impact of the vulnerability is wide-ranging.
JSOF is particularly concerned about its impact on three vulnerabilities that could be used for DNS cache poisoning: CVE-2020-25684, CVE-2020-25685, and CVE-2020-25686. DNS cache poisoning is a technique in which an attacker stores fake information in a DNS server and directs the user to a website prepared by the attacker. Users can unknowingly visit malicious fake websites and enter their personal information, which can lead to phishing scams and malware installations.
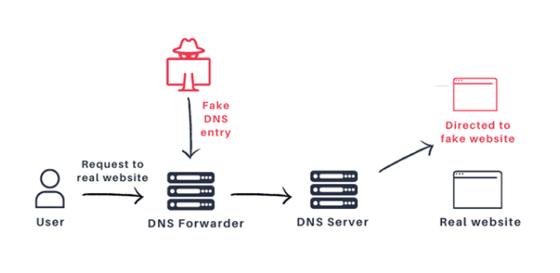
“Not only can you browse the Internet, but you can also be attacked by communications such as email,
The remaining four of the seven vulnerabilities, CVE-2020-25687, CVE-2020-25683, CVE-2020-25682, and CVE-2020-25681, are buffer overflow vulnerabilities that can lead to DoS attacks and information leaks. It may lead to remote code execution.
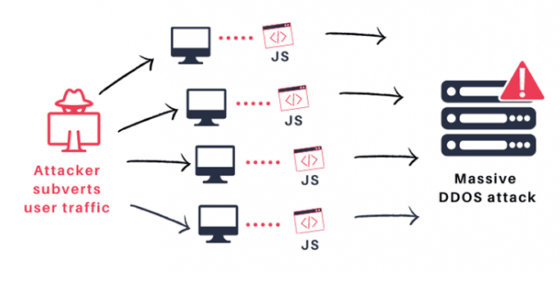
Researchers explain that attacks using DNSpooq are very easy and can be done in seconds to minutes without the use of special tools. In addition, researchers point out that many dnsmasq servers are accidentally exposed over the WAN , allowing direct attacks over the Internet. According to Shodan Search , there are more than 1 million Dnsmasq open to the Internet at the time of writing, and routers, VPNs, smartphones, tablets, access points, information communication systems, modems, etc. are at risk of attack. ... apparently ...
JSOF recommends updating Dnsmasq to the latest version (2.83 or later) as a way to prevent attacks using DNSpooq.
Related Posts:
in Security, Posted by darkhorse_log