Microsoft Teams's 'forced termination' and 'scam site guidance' vulnerabilities have been left unattended for more than 9 months
With the spread of remote work, communication tools such as Microsoft Teams and Zoom have become widely used. Meanwhile, security company Positive Security has reported four vulnerabilities in Microsoft Teams.
MS Teams: 1 feature, 4 vulnerabilities | Positive Security
https://positive.security/blog/ms-teams-1-feature-4-vulns
In Microsoft Teams, when you send a message containing a URL, thumbnails and some of the linked information will be displayed as a preview. Positive Security has verified the potential exploitation of the preview feature and found four vulnerabilities.
◆ 1: Attack via Microsoft server
Previews are generated on Microsoft's servers, and it is difficult to exploit the preview feature to directly attack users. However, according to Positive Security, attacks on Microsoft's servers themselves are relatively easy, and a technique called 'SSRF attacks' that attack users through Microsoft's servers is feasible.
◆ 2: Creating a spoofing preview
Positive Security also discovered a vulnerability that could change the link destination of the preview while maintaining the URL and thumbnail displayed in the preview. We have released a movie recording how the vulnerability is actually used.
In the published movie, the link to 'bing.com ' has been rewritten to the link to ' google.com'.
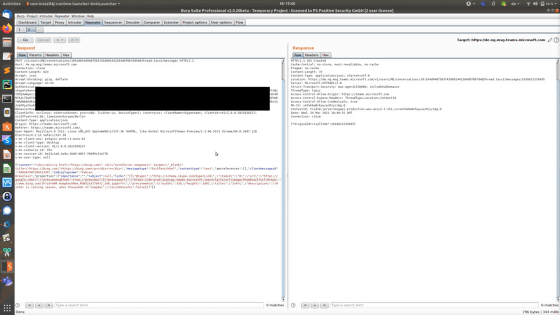
Even after rewriting, the URL displayed in Microsoft Teams remains 'https://bing.com/' ...
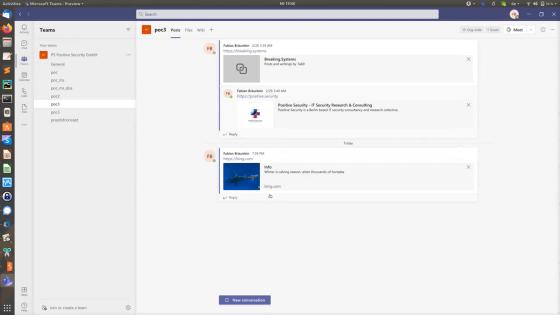
Clicking on the preview opened the Google home page. Exploitation of this vulnerability could allow users to connect to malicious websites.
◆ 3: IP address interception
The thumbnail displayed on the preview screen is generated by Microsoft's server, and even if you click the thumbnail to access the website, the user's IP address and user agent are not transmitted to the website. However, Positive Security has discovered a vulnerability that allows you to change the link destination to a thumbnail. According to Positive Security, Microsoft Teams for Android does not have the ability to restrict domains, and it is possible to illegally obtain user IP addresses and user agents by exploiting the discovered vulnerabilities. It was said that. At the time of writing the article, this vulnerability has been fixed.
◆ 4: Forcibly crash just by sending one message
In addition to the above vulnerabilities, Microsoft Teams for Android has also discovered a vulnerability that 'the app crashes when a message containing an invalid URL is received'. When you play a movie published by Positive Security, you can see how Microsoft Teams crashes the moment you open a chat screen that receives a malicious URL.
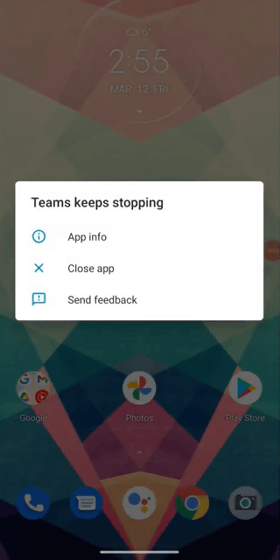
Positive Security reported four vulnerabilities to Microsoft on March 10, 2021. And as a result of re-examining the vulnerability on December 15, 2021, only 'IP address interception' was fixed, and the other three cases were not fixed. Positive Security says, 'The impact of the discovered vulnerabilities is limited, but it's amazing that simple attacks don't seem to be tested and Microsoft doesn't have the willingness or resources to protect users. That's it. '
Related Posts: