Security researchers warn that Gmail and Amazon ``passwords are stored in plain text in HTML''

Analysis of vulnerabilities related to browser text input fields revealed that passwords are stored in plain text in the HTML source code of sites of major companies and government agencies. Experts who discovered the problem reported that they created a test extension that could extract sensitive data and were able to easily upload it to the Chrome Web Store.
[2308.16321] Exposing and Addressing Security Vulnerabilities in Browser Text Input Fields
Chrome extensions can steal plaintext passwords from websites
https://www.bleepingcomputer.com/news/security/chrome-extensions-can-steal-plaintext-passwords-from-websites/
In a paper published on the preprint server arXiv, Asmit Nayak of the University of Wisconsin-Madison and his colleagues write, ``The coarse -grained permissions model that underpins browser extensions is a combination of the principle of least privilege and complete intermediation. 'It has become clear that this is in violation of principles,' he said, pointing out that the vulnerabilities are caused by unnecessary permission requests and inadequate security enforcement prevalent in browsers such as Chrome. did.
According to the research team, the problem identified this time is due to the way the extension accesses the internal code of the web page. Many sites operate on a mechanism called Document Object Model (DOM) that allows programs to manipulate documents written in HTML etc., but due to the problem that extensions can access this DOM tree without restriction. , The research team explains that sensitive data in the source code can be easily extracted.

Google introduced a specification called '
To test the Chrome Web Store's ability to check extensions, the researchers uploaded a proof-of-concept extension disguised as a GPT-based assistant. The extension had a built-in function that read the HTML source code and then extracted the password entered by the user, but it did not contain any obvious malicious code and was compliant with Manifest V3. It passed the review without any problems and was approved. In addition, the research team set the extension to 'private' to prevent actual harm, and deleted it immediately after approval.
The researchers identified 190 extensions that provide direct access to password input fields, including some popular extensions with over 100,000 downloads. We also confirmed that approximately 17,300 extensions, or 12.5% of the total, have permissions to exploit this vulnerability.
More seriously, the research team found that many sites, including large and government sites with large numbers of users, store users' passwords in plain text format.
The main sites where problems were found are as follows.
・Amazon (amazon.com): Credit card information including security code and postal code are displayed in plain text on the page's source code.
・Gmail (gmail.com): Plaintext passwords are stored in the HTML source code
・Cloudflare (Cloudflare.com): Same as above
・Facebook (facebook.com): User input can be extracted via DOM API
・Citibank (citibank.com): Same as above
- U.S. Internal Revenue Service (irs.gov): Social Security Numbers (SSNs) are displayed in plain text on the source code of web pages.
The following shows how the login ID and password are actually extracted.
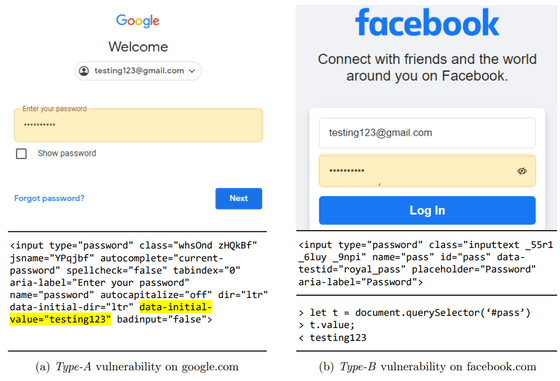
'Major online marketplaces such as Google and Amazon do not implement any protections for credit card input fields,' the researchers wrote in their paper. We are particularly concerned that the site is not secure.'
In response to this announcement, an Amazon spokesperson said, ``We encourage browser and extension developers to leverage security best practices to further protect customers using their services.'' announced. A Google spokesperson also said they are investigating the issue.
In addition, Google is introducing a feature that will alert users when an extension installed in Chrome is removed from the Web Store or is found to contain malware. This feature is scheduled to be officially implemented in Chrome 117, but according to the IT news site
Related Posts:
in Security, Posted by log1l_ks