Exploit ``LogoFAIL'' has been discovered that allows arbitrary code execution by replacing the logo image displayed in UEFI when starting a PC, targets Windows and Linux and bypasses any security

Security company Binarly has announced an exploit called LogoFAIL that attacks 24 vulnerabilities found in UEFI related to booting devices running Windows or Linux.
Finding LogoFAIL: The Dangers of Image Parsing During System Boot | Binarly – AI -Powered Firmware Supply Chain Security Platform

Just about every Windows and Linux device vulnerable to new LogoFAIL firmware attack | Ars Technica
https://arstechnica.com/security/2023/12/just-about-every-windows-and-linux-device-vulnerable-to-new-logofail-firmware-attack/
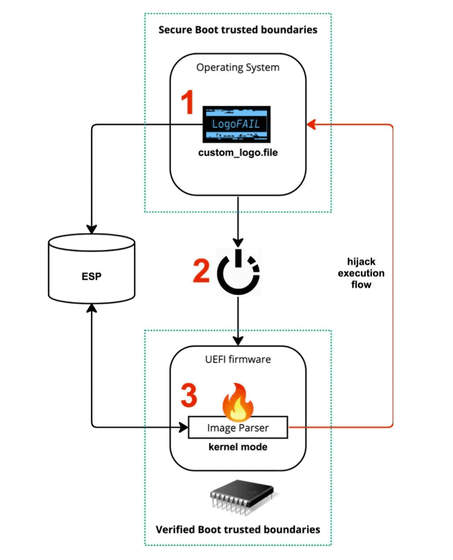
The 'Logo' in LogoFAIL comes from the device logo that appears on the screen when running UEFI. By replacing the legitimate logo image with a specially crafted logo image to exploit these bugs, LogoFAIL inserts malicious code into the most sensitive stage of the boot process called DXE (Driver Execution Environment). allows you to execute.
Below is a video that actually reproduces LogoFAIL. Binarly researchers say, 'If arbitrary code execution becomes possible during the DXE stage, it's game over for platform security.'
Finding LogoFAIL: The Dangers of Image Parsing During System Boot - YouTube
The malicious logo causes UEFI to execute attacker-written code during the DXE stage every time the device boots. By executing the code at an early stage, the exploit can hijack all subsequent execution flows to prevent security defenses such as Secure Boot or hardware-based security defenses such as Intel Boot Guard, AMD Hardware-Validated Boot, and ARM TrustZone-based Secure Boot. This allows you to ignore the verified boot mechanism.
This issue affects motherboards that use UEFI provided by independent BIOS vendors such as AMI, Insyde, and Phoenix. Many OEMs, such as Dell, do not allow logo changes in UEFI, and logo image files are also protected by Image Boot Guard, so they are not affected by LogoFAIL.
If your system integrator doesn't allow boot image rewriting in the BIOS, that's fine, but both the motherboard manufacturer and OEM will need to patch it. Binarly says, 'AMI, Insyde, Lenovo, and others have issued advisories, but there is no complete list of affected companies, so you should check with your motherboard manufacturer to find out if your system is vulnerable.' There is.”
◆Forum now open
A forum related to this article has been set up on the GIGAZINE official Discord server . Anyone can write freely, so please feel free to comment! If you do not have a Discord account, please create one by referring to the article explaining how to create an account!
• Discord | 'Have you ever encountered any BIOS or UEFI related problems on your PC?' | GIGAZINE
https://discord.com/channels/1037961069903216680/1182242834145886238
Related Posts: