Added the ability for Windows to block the installation of vulnerable drivers

Windows
New Windows security feature blocks vulnerable drivers
https://www.bleepingcomputer.com/news/microsoft/new-windows-security-feature-blocks-vulnerable-drivers/
Windows has announced the ability to use WDAC to block the installation of known vulnerable drivers. This feature will be provided as part of the core isolation feature, which is a security feature.
The ability to block WDAC vulnerable drivers works on Windows 10/11 / Server 2016 with hypervisor-protected code integrity (HVCI) enabled and Windows 10 in S mode .

WDAC is a security layer that allows only trusted drivers and apps to run, protecting Windows from potentially malicious software by blocking the launch of malware and unwanted software. WDAC uses
In addition, Windows blocks third-party drivers with the following attributes.
· Known security vulnerabilities that attackers can exploit to elevate privileges in the Windows kernel
· Certificates used to sign malicious behavior (malware) or malware
Behavior that could be exploited by an attacker to evade a non-malicious Windows security model and elevate privileges in the Windows kernel.
The function to block vulnerable drivers of WDAC will be provided as an optional function called 'Microsoft Vulnerable Driver Blocklist', and it can be turned on and off from 'Windows Security' → 'Device Security' → 'Core Isolation'. ..
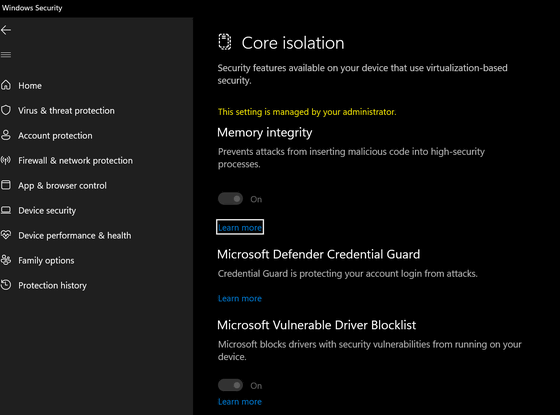
When this feature is enabled, it blocks certain drivers based on SHA256 hash , file attributes such as filename / version number, code signing certificate used to sign the driver, and so on.
However, Bleeping Computer points out that enabling the Microsoft Vulnerable Driver Blocklist will prevent legitimate programs in the blocklist, such as Cheat Engine and Process Hacker, from working.
In addition, Microsoft warns that 'If you block the kernel driver without sufficient testing, the device or software may malfunction and in rare cases a blue screen may occur', and use audit mode first. It is recommended.
Related Posts: