Two zero-day vulnerabilities with a severity of `` emergency '' in Windows, possibility that attacks have already been made
by Bolly Holly Baba
Microsoft issued a new security advisory on March 23, 2020, warning of two unfixed zero-day vulnerabilities . According to Microsoft, this vulnerability affects Windows 10 and other Windows series, related to the file preview feature used in Windows Explorer. In addition, it has been reported that a targeted attack that seems to have exploited this vulnerability has already been confirmed.
ADV200006 | Type 1 Font Parsing Remote Code Execution Vulnerability
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/adv200006
According to Microsoft, ' PostScript Type1 ' font processing in the ' Adobe Type Manager ' library that displays fonts in the 'Preview Pane' and 'Details Pane' that allows you to view the contents on Explorer without opening the file 'Remote code There are two unfixed vulnerabilities that can be executed. ' In each case, Microsoft states that an attacker could exploit this vulnerability by having the user open a particular document in a third-party software or view the document in a preview window.
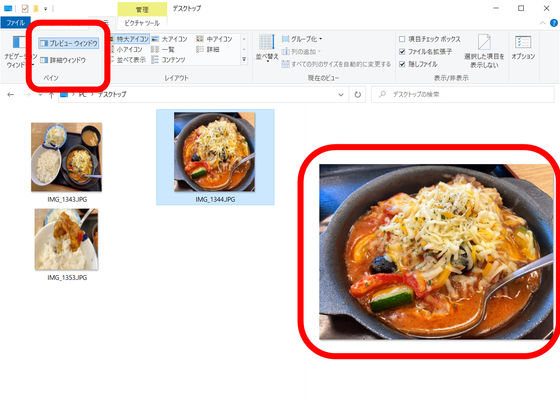
The versions of the operating systems affected by this vulnerability are as follows, and the severity is 'Critical'.
・ Windows 7 (32bit) SP1
・ Windows 7 (64bit) SP1
・ Windows 8.1 (32bit)
・ Windows 8.1 (64bit)
・ Windows RT 8.1
・ Windows 10 (32bit)
・ Windows 10 (64bit)
・ Windows 10 version 1607 (32bit)
・ Windows 10 version 1607 (64bit)
・ Windows 10 version 1709 (32bit)
・ Windows 10 version 1709 (64bit)
・ Windows 10 version 1709 (ARM64)
・ Windows 10 version 1803 (32bit)
・ Windows 10 version 1803 (64bit)
・ Windows 10 version 1803 (ARM64)
・ Windows 10 version 1809 (32bit)
・ Windows 10 version 1809 (64bit)
・ Windows 10 version 1809 (ARM64)
・ Windows 10 version 1903 (32bit)
・ Windows 10 version 1903 (64bit)
・ Windows 10 version 1903 (ARM64)
・ Windows 10 version 1909 (32bit)
・ Windows 10 version 1909 (64bit)
・ Windows 10 version 1909 (ARM64)
・ Windows Server 2008 (32bit) SP2
・ Windows Server 2008 (32bit) SP2 ServerCore
・ Windows Server 2008 (32bit) for Itanium-based Systems SP2
・ Windows Server 2008 (64bit) SP1
・ Windows Server 2008 (64bit) SP1 ServerCore
・ Windows Server 2008 (64bit) SP2
・ Windows Server 2008 (64bit) SP2 ServerCore
・ Windows Server 2008 R2 for Itanium-based Systems SP2
・ Windows Server 2012
・ Windows Server 2012 ServerCore
・ Windows Server 2012 R2
・ Windows Server 2012 R2 ServerCore
・ Windows Server 2016
・ Windows Server 2016 ServerCore
・ Windows Server 2019
・ Windows Server 2019 ServerCore
Although there are no patches at the time of writing, Microsoft has acknowledged this vulnerability and states that it is also working on developing patches, and plans to distribute it on Windows Update on the second Wednesday of every month.
In a security advisory, Microsoft strongly recommends disabling the preview and details panes as a workaround for all affected Windows users. It also states that disabling the WebClient service will prevent remote attacks via WebDAV clients.
Furthermore, Microsoft also introduces a rough technique of `` temporarily disabling Adobe Type Manager itself by changing the file name of Adobe Type Manager Font Driver (ATMFD.dll) '', but this method is Please note that some third-party apps may stop working.
Related Posts: