A new vulnerability `` LVI '' was found in Intel CPUs, and personal information and company confidential information may leak out

A vulnerability called ' Load Value Injection (LVI) ' has been identified that could expose sensitive information such as certificates and passwords to Intel CPUs. LVI is a CPU vulnerable to ``
LVI: Hijacking Transient Execution with Load Value Injection
https://lviattack.eu/
Intel CPUs vulnerable to new LVI attacks | ZDNet
https://www.zdnet.com/article/intel-cpus-vulnerable-to-new-lvi-attacks/
LVI Attacks: New Intel CPU Vulnerability Puts Data Centers At Risk
https://thehackernews.com/2020/03/intel-load-value-injection.html
This vulnerability 'LVI' is intended to speed up the CPU, 'speculative execution' that pre-reads the processing after branching before conditional branching, and postpone the subsequent processing before processing is completed Related to “out-of-order execution”. ' Meltdown ' and ' Specter ' using the same vulnerability structure are described in detail in the following articles.
The root of the vulnerability problem inherent in Intel CPUs is deeply pointed out that `` all processors have a problem that they can not balance safety and high speed ''-GIGAZINE
Meltdown and Specter use speculative execution of data itself. leakage LVI is a vulnerability that allows an attacker to obtain data by inserting malicious code as a target for speculative execution. The code can be inserted locally by malware, or by executing JavaScript remotely on the browser.
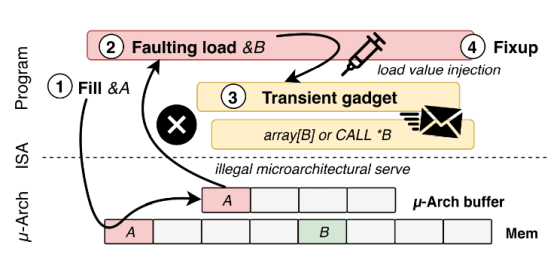
In LVI, the target program first loads improper data through a hidden buffer, causing an exception such as a buffer overflow. The CPU that detects the exception performs 'temporary execution' of the program before returning to the normal state, but by reading the confidential information in the memory of the attack target by modifying the code of the temporary execution It is a mechanism that can be.
Also, a demo movie of hacking by LVI has been released on YouTube.
LVI (Load Value Injection) Demo Video-YouTube
LVI can also bypass mitigation measures that have been taken against Meltdown and Specter that cause CPU performance degradation, and it can not be completely fixed just by changing the CPU microcode by firmware. The affected CPUs this time are reported to be CPUs with Intel SGX prior to the Ice Lake generation.
Related Posts:
in Security, Posted by darkhorse_log