An attack using the Linux vulnerability 'Dirty Pipe', in which a movie that instantly steals the root authority of an Android device is released, is realistic
Demonstration movie to take root authority of 'Pixel 6 Pro' and 'Samsung S22' by using '
Researcher uses Dirty Pipe exploit to fully root a Pixel 6 Pro and Samsung S22 | Ars Technica
https://arstechnica.com/information-technology/2022/03/researcher-uses-dirty-pipe-exploit-to-fully-root-a-pixel-6-pro-and-samsung-s22/
Dirty Pipe is a vulnerability caused by ' pipes ' that are responsible for communication between programs. When Dirty Pipe is abused, 'SSH key' is used for Linux-based systems and Android-based terminals developed based on Linux. It has been reported that attacks such as 'create' and 'create a user with root privileges' are possible.
Although the latest version of Linux has already been modified, it has been confirmed that there are smartphones on the market with versions of Android under the influence of Dirty Pipe. The following articles explain how to find out if your smartphone is affected by Dirty Pipe.
A critical elevating vulnerability was discovered in the Linux kernel, affecting Android devices--GIGAZINE

And on March 15, 2022, security researcher Fire 30 released a demonstration movie that actually
Dirty Pipe-> kernel r / w + selinux disabled + root shell on Pixel 6 Pro and Sasmsung S22 latest update :) pic.twitter.com/WwhwjLyU5q
— Fire30 (@ Fire30_) March 14, 2022
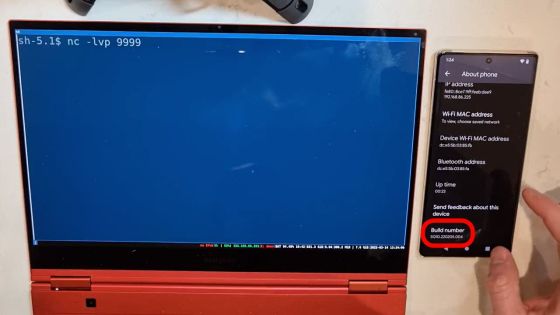
First of all, verification will be done with 'Pixel 6 Pro'. 'SQ1D.220205.004' is written in the build ID column, and you can see that it is the latest build at the time of article creation.
Run a demo app that can attack using Dirty Pipe.
Processing is completed in an instant. When I run the 'id' command to display user information on the machine on the left, I get a result showing that I am logged in as the root user. In other words, if you execute an 'application that abuses Dirty Pipe' like this demo application, you will be instantly deprived of root authority and will be in a state where you can execute all operations from the outside.
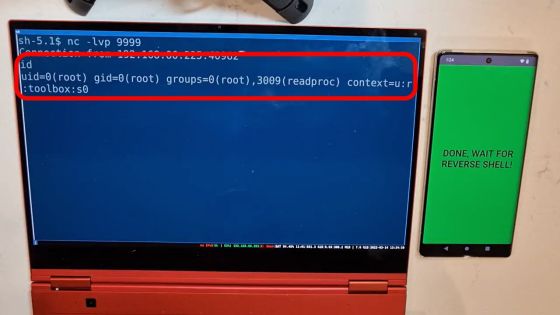
If you run the 'uname' command to display kernel information, you will see that you are using the kernel of version '5.10.43' affected by Dirty Pipe.
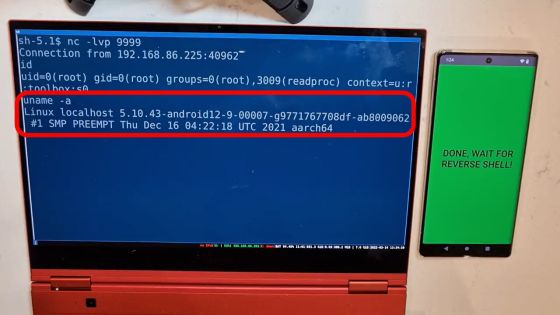
Furthermore, when the 'getenforce' command that displays the usage status of the Linux security enhancement module '
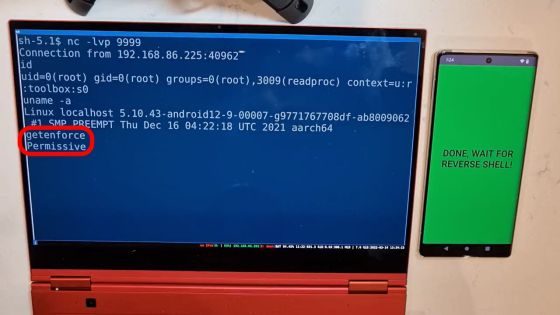
Next, when you run the demo app on 'Samsung S22' with the version '5.10.43' kernel installed ...
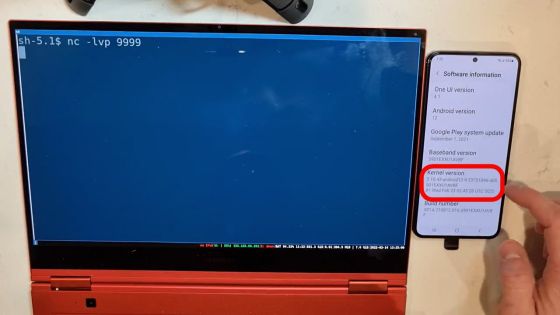
As with 'Pixel 6 Pro', the capture of root authority has been completed in an instant.
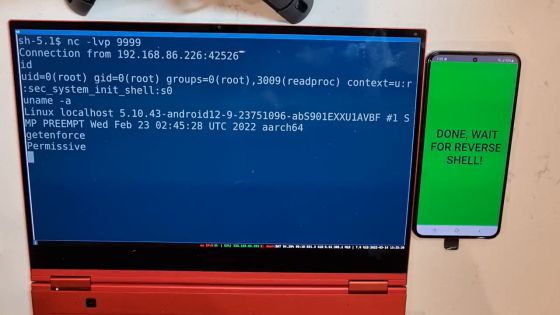
According to Fire30, the setting change of SELinux is realized by 'proprietary technology developed by Fire30' instead of Dirty Pipe, and it may be difficult to take root authority of Android terminal with Dirty Pipe alone. .. However, if an attacker develops a method to change SELinux settings like Fire30, it will be possible to execute a malicious program by instantly stealing root authority from the Android terminal as in the above movie. increase.
A Google representative told Ars Technica, an overseas media company, 'The Android development team is aware of the problem and is providing information to each device manufacturer on how to apply the patch.' However, it is not clear when the fix will be available to users.
Related Posts:
in Smartphone, Security, Posted by log1o_hf