A serious vulnerability ``GameOver (lay)'' that affects 40% of Ubuntu, an emergency situation that should have been fixed in 2020 but will be discovered again
A local privilege escalation vulnerability 'GameOver(lay)' was discovered in Ubuntu, one of the Linux distributions. There are two CVEs, 'CVE-2023-2640' and 'CVE-2023-32629', and although patches have been released for both on July 24, 2023, the details of the vulnerabilities were discovered in the Linux kernel in 2020. It is the same as the corrected 'CVE-2021-3493', and the cloud security company Wiz, who discovered this vulnerability, explained 'why the vulnerability that should have been fixed remained.' doing.
GameOverlay Vulnerability Impacts 40% of Ubuntu Workloads | Wiz Blog

According to Wiz, the main Ubuntu versions affected are as follows, and about 40% of Ubuntu workloads are applicable. Other versions are available for CVE-2023-32629 and CVE-2023-2640 in Ubuntu.
| Release | Version | CVE-2023-2640 | CVE-2023-32629 |
|---|---|---|---|
| Ubuntu 23.04 (Lunar Lobster) | |||
| 6.2.0 | ✔ | ✔ | |
| Ubuntu 22.10 (Kinetic Kudu) | |||
| 5.19.0 | ✔ | ✔ | |
| Ubuntu 22.04 LTS (Jammy Jellyfish) | |||
| 5.19.0 | ✔ | ✔ | |
| 6.2.0 | ✔ | ✔ | |
| 5.15.0 | ✘ | ✘ | |
| Ubuntu 20.04 LTS (Focal Fossa) | |||
| 5.15.0 | ✘ | ✘ | |
| 5.4.0 | ✘ | ✔ | |
| Ubuntu 18.04 LTS (Bionic Beaver) | |||
| 5.4.0 | ✘ | ✔ |
The vulnerability this time was due to a function called OverlayFS and file capabilities . OverlayFS is a function that bundles directories as layers and shows them as one directory, and is divided into a layer of one or more read-only lower directories and a layer of writable upper directories. If a file with the same name exists in multiple layers, the file in the top layer will be displayed first, and when the user tries to write to a file in the read-only layer, the file will be automatically transferred to the upper directory. Copy and write. OverlayFS is used to implement Docker containers.
Also, capabilities are functions that allow some of the root privileges to be used when executing a file. Of course, only users with root privileges can assign capabilities to files. Wiz discovered that the namespace restriction was erroneously lifted when copying to a higher layer, allowing it to run with root privileges.
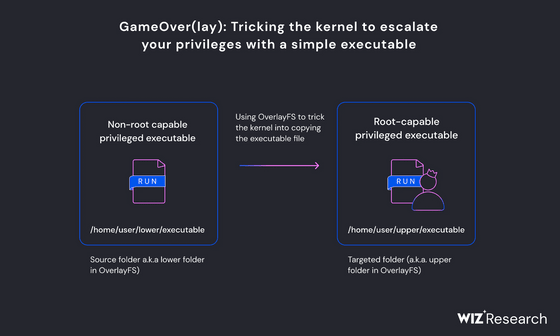
This vulnerability has the same content as 'CVE-2021-3493', which was resolved in 2020, and the attack method at that time is said to be valid. When Wiz investigated why the vulnerability that should have been fixed remained in Ubuntu, on January 29, 2018, instead of the function 'vfs_setxattr' that sets extended attributes, the internal implementation '__vfs_setxattr_noperm' It turned out that it was not affected by the changes that went into 'vfs_setxattr' as a fix for CVE-2021-3493 on December 14th, 2020, as we had modified the kernel to utilize it.

Ubuntu has released a patch for the affected kernel version for this vulnerability, so it is very important for users who are using the affected version to update to the new version. If you cannot update for some reason, it is possible to prevent exploitation of this vulnerability by setting the use of the user namespace to only users with restricted privileges with the following command.
[code]sudo sysctl -w kernel.unprivileged_userns_clone=0[/code]
If you want to keep the above settings after rebooting the system, you can use the following command.
[code]echo kernel.unprivileged_userns_clone=0 | \
sudo tee /etc/sysctl.d/99-disable-unpriv-userns.conf[/code]
Related Posts:
in Security, Posted by log1d_ts