Privilege elevation vulnerability in 'sudo' command, list of correspondence of each distribution

A vulnerability was found in the command '
CVE-2021-3156: Heap-Based Buffer Overflow in Sudo (Baron Samedit) | Qualys Security Blog
https://blog.qualys.com/vulnerabilities-research/2021/01/26/cve-2021-3156-heap-based-buffer-overflow-in-sudo-baron-samedit
Buffer overflow in command line unescaping
https://www.sudo.ws/alerts/unescape_overflow.html
Alert regarding sudo vulnerability (CVE-2021-3156)
https://www.jpcert.or.jp/at/2021/at210005.html
New Linux SUDO flaw lets local users gain root privileges
https://www.bleepingcomputer.com/news/security/new-linux-sudo-flaw-lets-local-users-gain-root-privileges/
The 'sudo' command is used when you want to temporarily execute a program with privileges, and you can handle privileges with limited privileges without logging in as the root user. Qualys , a cloud security service provider, discovered that sudo had been vulnerable to privilege escalation due to a heap-based buffer overflow since July 2011, about 10 years ago, and named it 'Baron Samedit'.
The vulnerability existed in 'set_cmnd ()' that escapes command arguments. The following is a partial excerpt of the code for set_cmnd (), where 'from' is the variable where the arguments are stored and 'to' is the heap-based buffer.
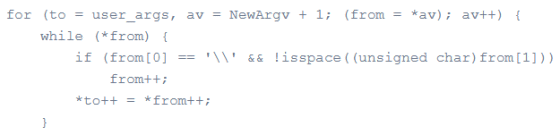
The processing of this while statement is 'If the character stored in the address pointed to by the from pointer is a backslash and the character stored in the next address is not a space, that character is stored in the buffer'. This is a description for processing backslash-escaped arguments, but if you enter only a backslash in the argument, the
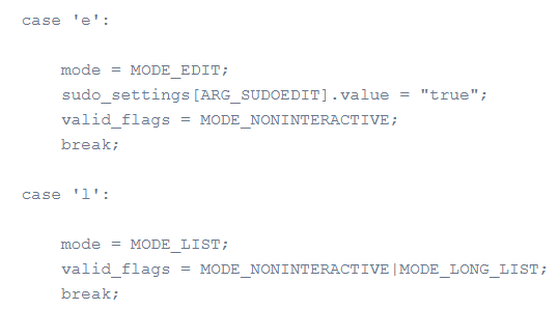
Escape processing by set_cmnd () is executed only when 'MODE_SHELL' is specified in the flag 'valid_flags', and 'MODE_SHELL' is not included when the option is specified by the normal sudo command. The initialization was done.
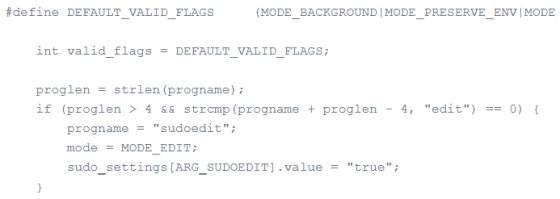
However, the sudoedit command did not perform this initialization process, and valid_flags specified 'DEFAULT_VALID_FLAGS' including MODE_SHELL. Therefore, it was possible to cause a buffer overflow via sudoedit.
Qualys has also released a movie that actually gains privileges by exploiting this vulnerability. Since the attacking code itself is private, the content of the process is unknown, but you can see how the privilege is actually acquired.
CVE-2021-3156: Heap-Based Buffer Overflow in Sudo (Baron Samedit) on Vimeo
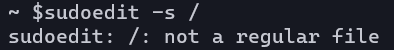
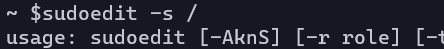
To check whether the OS you are using is affected by the vulnerability, execute 'sudoedit -s /', and if 'not a regular file' is displayed, correct it, 'usage: sudoedit ..... If '.' Is displayed, it has been corrected.
This vulnerability has been numbered as ' CVE-2021-3156 ', and the support status of major Linux distributions is as follows.
-Ubuntu: Fixed package distributed after 14.04 ESM
CVE-2021-3156 | Ubuntu
https://ubuntu.com/security/CVE-2021-3156
-Debian: Fixed package distributed after Stretch
CVE-2021-3156
https://security-tracker.debian.org/tracker/CVE-2021-3156
-RHEL: RHEL 5 has no effect, and modified packages have been distributed since RHEL 6
CVE-2021-3156- Red Hat Customer Portal
https://access.redhat.com/security/cve/CVE-2021-3156
-Fedora: Fixed package distributed in 32 and 33
[SECURITY] Fedora 33 Update: sudo-1.9.5p2-1.fc33 --package-announce --Fedora Mailing-Lists
https://lists.fedoraproject.org/archives/list/[email protected]/message/LHXK6ICO5AYLGFK2TAX5MZKUXTUKWOJY/
[SECURITY] Fedora 32 Update: sudo-1.9.5p2-1.fc32 --package-announce --Fedora Mailing-Lists
https://lists.fedoraproject.org/archives/list/[email protected]/message/CALA5FTXIQBRRYUA2ZQNJXB6OQMAXEII/
Gentoo: Fixed package distributed
sudo: Multiple vulnerabilities (GLSA 202101-33) — Gentoo security
https://security.gentoo.org/glsa/202101-33
-Amazon Linux: Fixed package distributed
Sudo Security Issue
https://aws.amazon.com/jp/security/security-bulletins/AWS-2021-001/
-Cisco: Affects multiple network devices, patch has been distributed
Sudo Privilege Escalation Vulnerability Affecting Cisco Products: January 2021
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-sudo-privesc-jan2021-qnYQfcM
For OSs other than the above, such as macOS and Solaris, the latest version of the fix package is distributed from the official sudo website.
Download Sudo
https://www.sudo.ws/download.html
Related Posts: